Introduction
Your Active Directory delegations are invisible. You can’t query them. You can’t track changes. You can’t build intelligence around who has access to what.
I’ve changed that.
The Capability That Didn’t Exist
For 20 years, AD delegation management meant manual reviews, spreadsheets, and hoping nothing changed between audits. You had no way to write:
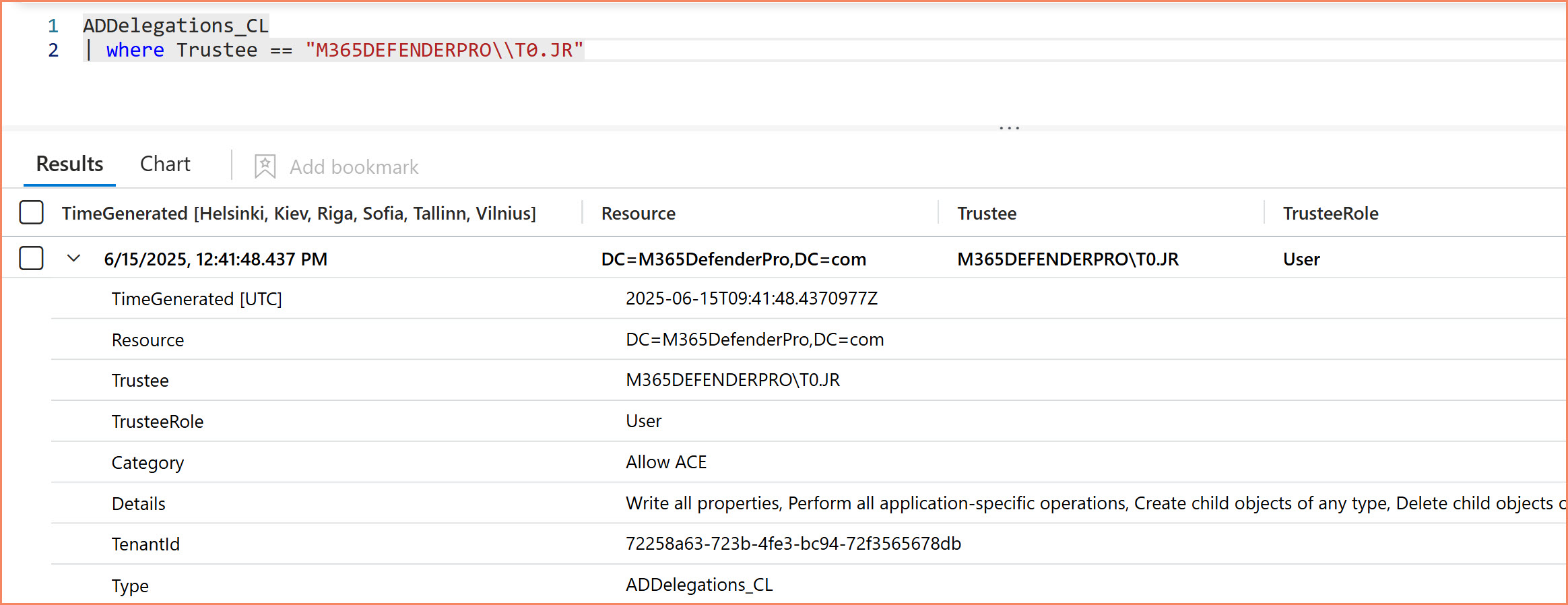
ADDelegations_CL
| where Trustee == "M365DEFENDERPRO\\T0.JR"
Now you can.
What This Actually Means
Through Azure Arc and Sentinel integration, I’ve made AD delegations queryable like any other security data. This isn’t an improvement to existing tools – it’s an entirely new capability.
You can query your entire delegation history with KQL. Build workbooks showing delegation patterns over time. Create analytics rules that fire on permission anomalies. Hunt for specific delegation patterns across your environment. Prove delegation state at any point in time.
How It Works
The solution uses PowerShell collectors running on your domain controllers via Azure Arc. These extract complete delegation data including direct permissions, custom delegations, and service account permissions. Daily ingestion into Sentinel creates queryable history where every delegation change becomes a searchable event. Pre-built queries, workbooks, and analytics rules turn raw data into actionable insights.
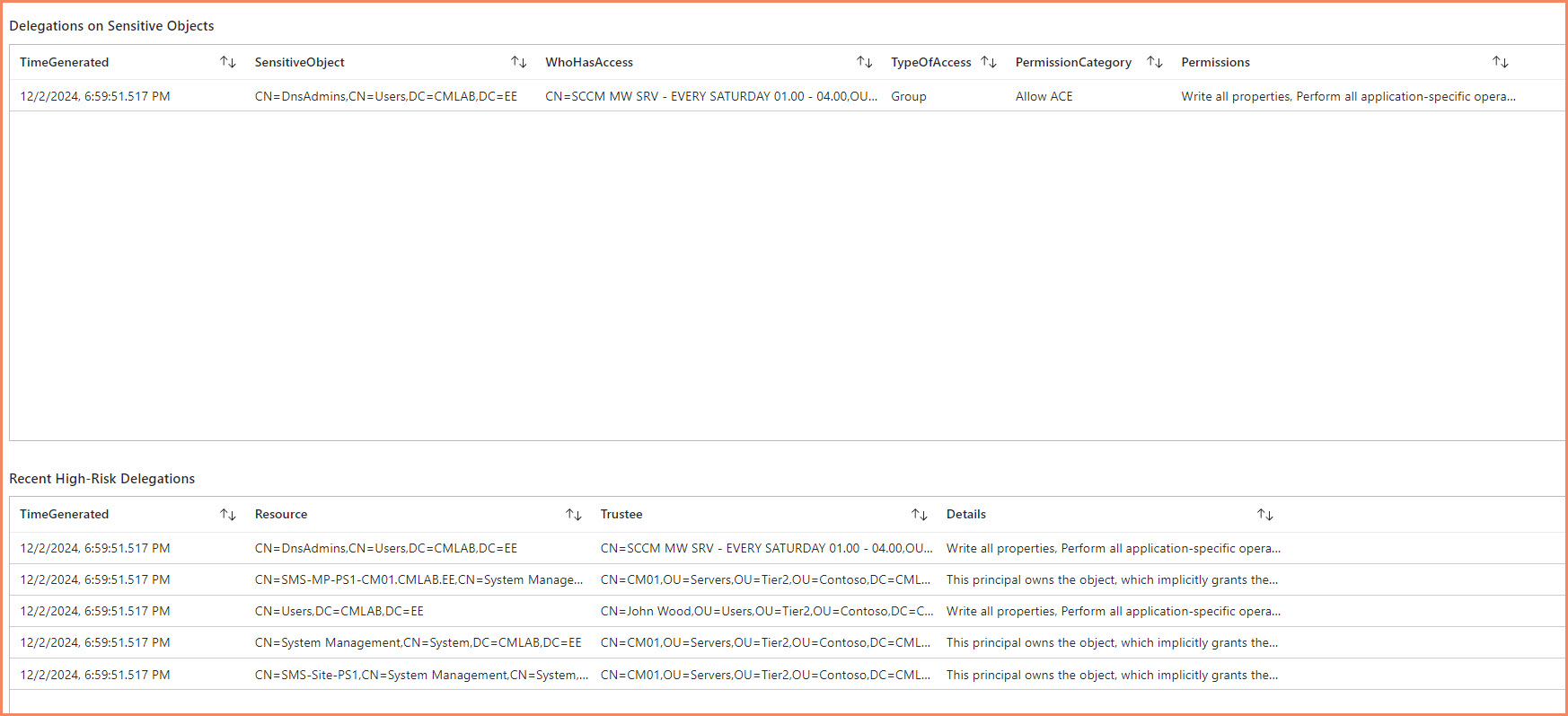
Real Discoveries from Real Deployments
Running this query often reveals surprising patterns:
ADDelegations_CL
| where Resource contains "Domain Admin"
Common findings include service accounts with 50+ delegated permissions, human accounts with administrative rights to dozens of OUs, delegation patterns that cluster around specific timeframes, and permission inheritance chains nobody knew existed.
Implementation Requirements
You’ll need an Azure subscription with Sentinel, a Log Analytics workspace, Azure Arc-enabled servers, and domain controller access. Deployment typically takes 2-3 hours including Arc agent configuration, script deployment, data ingestion setup, and workbook import.
What You Get
The complete implementation package includes production-tested PowerShell scripts, Arc extension configuration, managed identity setup guides, and over 20 KQL queries for common investigations. You’ll also receive pre-built Sentinel workbooks, analytics rule templates, a hunting queries library, and comprehensive documentation covering architecture, deployment, troubleshooting, and security considerations.
Transform Your AD Visibility
Organizations using this solution gain complete delegation visibility for the first time. They get historical tracking of permission changes, proactive alerting on anomalies, evidence for compliance requirements, and answers to previously impossible questions.
Your AD delegations are accumulating right now. Every day without visibility is another day of unknown permissions multiplying through inheritance.
Get Started Today
The complete AD delegation monitoring solution is available through our membership tiers at docs.kaidojarvemets.com.
Whether you need it for internal use, client deployments, or want us to implement it for you – we have the right option.
Have questions about implementation? Need help choosing the right tier? Contact me directly to discuss your specific environment.