When you onboard a node to Azure Arc, you will also receive a system-assigned managed identity for that server. This managed identity provides a unique security identity for your server, and enables you to delegate different permissions for Azure resources such as Azure Key Vault. With this managed identity, you can create and manage Azure resource access policies and access controls, and can use it to securely authenticate and authorize your server to access Azure services and resources. This opens up many more possibilities and use cases for Azure Arc, and allows you to better secure and manage your hybrid and multi-cloud environments.
I recommend reading Authenticate against Azure resources with Azure Arc-enabled servers article.
You can install the Az.ManagedServiceIdentity PowerShell module directly from the PowerShell Gallery.
Install-Module -Name Az.ManagedServiceIdentity -Force -Verbose
Run the following command to print out all the command lets in Az.ManagedServiceIdentity PowerShell module
- Get-Command -Module Az.ManagedServiceIdentity
Get-AzFederatedIdentityCredentials
New-AzFederatedIdentityCredentials
Remove-AzFederatedIdentityCredentials
Update-AzFederatedIdentityCredentials
Get-AzFederatedIdentityCredential
Get-AzSystemAssignedIdentity
Get-AzUserAssignedIdentity
Get-AzUserAssignedIdentityAssociatedResource
New-AzFederatedIdentityCredential
New-AzUserAssignedIdentity
Remove-AzFederatedIdentityCredential
Remove-AzUserAssignedIdentity
Update-AzFederatedIdentityCredential
Update-AzUserAssignedIdentity
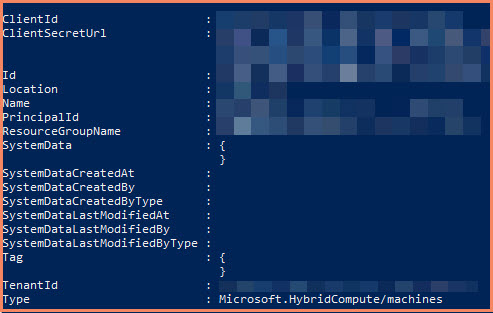
Get-AzSystemAssignedIdentity example
Gets the systemAssignedIdentity available under the specified RP scope.
Get-AzSystemAssignedIdentity -Scope "/subscriptions/XXXXXX/resourceGroups/RG-PROD-IT-ARC/providers/Microsoft.HybridCompute/machines/ADFS01"