Introduction
As cloud services become more common, protecting administrative access is a top priority. Cloud administrators manage an organization’s digital assets, making their accounts attractive to cyber attackers. Microsoft’s response is authentication strength policies in Entra ID (formerly Azure AD), which improve security for cloud administrators and break glass accounts.
These policies expand on standard multi-factor authentication (MFA). They let organizations set specific authentication methods for accessing sensitive resources. This control is needed because advanced phishing attacks can sometimes bypass basic two-factor authentication.
A key principle in securing Azure administration is using FIDO2 security keys as the minimum authentication standard. FIDO2 keys offer a physical, phishing-resistant form of authentication that increases security against potential attackers. Requiring these keys for administrative access helps organizations reduce unauthorized access risk, even if passwords are compromised.
Why Use Authentication Strength Policies?
Authentication strength policies in Entra ID offer several benefits:
- Stronger security: Enforce more secure authentication methods for high-risk users and scenarios.
- Risk reduction: Decrease the likelihood of unauthorized access to sensitive resources.
- Compliance: Meet security best practices and regulatory requirements.
- Account protection: Safeguard cloud administrative accounts from compromise.
- Flexibility: Tailor authentication requirements to different user roles and access levels.
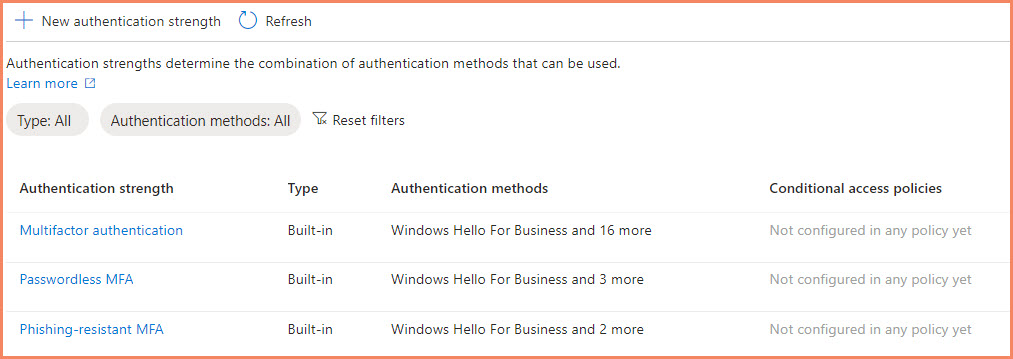
Default Authentication Strengths
Microsoft provides several built-in authentication strengths in Entra ID:
- Passwordless MFA
- Uses methods like Windows Hello, FIDO2 security keys, or the Microsoft Authenticator app.
- Phishing-resistant MFA
- Includes FIDO2 security keys and certificate-based authentication.
- Multifactor authentication
- Combines passwords with additional factors like phone calls, SMS, or app notifications.
For Azure administrative tasks, phishing-resistant MFA offers the highest level of protection. FIDO2 security keys, a key component of this strength, provide a physical factor that’s highly resistant to phishing attacks.
Configuring Authentication Strength Policies
To set up an authentication strength policy in Conditional Access:
- Access the Azure portal (portal.azure.com) and navigate to Entra ID.
- Go to Security > Conditional Access.
- Select “+ New policy“.
- Name your policy descriptively, e.g., “Admin FIDO2 Requirement“.
- Under “Assignments“, choose the users and cloud apps the policy applies to.
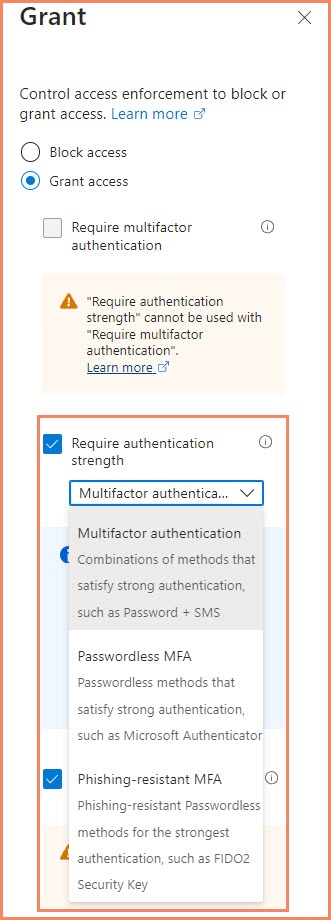
- In the “Access controls” section, select “Grant” and enable “Require authentication strength“.
- Choose “Phishing-resistant MFA” from the dropdown (or a custom strength that includes FIDO2).
- Review your settings, enable the policy, and click “Create“.
Remember to test the policy in report-only mode before full enforcement to avoid unintended access issues.
Creating Custom Authentication Strengths
For more specific needs, you can create custom authentication strengths:
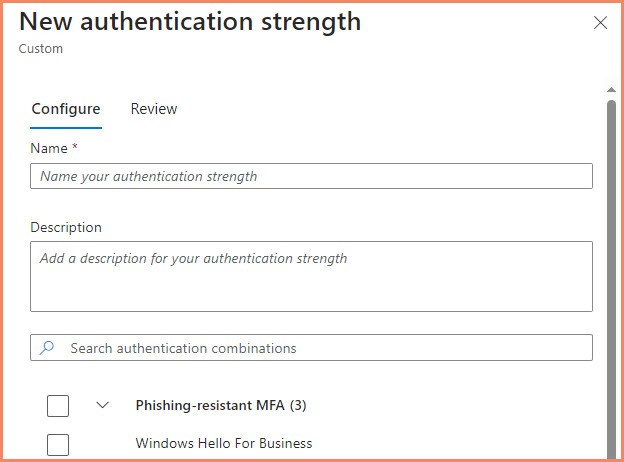
- In Entra ID, navigate to Security > Authentication methods > Authentication strengths.
- Click “+ New Authentication strength“.
- Provide a clear name and description.
- Select the allowed authentication methods. For admin access, always include FIDO2 security keys.
- Review your choices and create the policy.
Auditing Authentication Methods with Microsoft Graph
Understanding which authentication methods your users have configured helps maintain a strong security posture. Microsoft Graph allows you to audit these methods programmatically. Here’s how you can use PowerShell and Microsoft Graph to retrieve and analyze authentication methods for a specific user:
# Connect Microsoft Graph
Connect-MgGraph -Scopes @("UserAuthenticationMethod.Read")
# Define the user
$userId = "John@contoso.com"
# Fetch the user's authentication methods
$authMethods = Get-MgUserAuthenticationMethod -UserId $userId
# Initialize an array to hold the custom objects
$authMethodObjects = @()
# Loop through each method and extract relevant information into a custom object
foreach ($method in $authMethods) {
$authObject = [pscustomobject]@{
MethodType = $null
DisplayName = $null
Created = $null
AdditionalInfo = $null
}
switch ($method['@odata.type']) {
'#microsoft.graph.phoneAuthenticationMethod' {
$authObject.MethodType = "Phone"
$authObject.DisplayName = $method['phoneNumber']
$authObject.AdditionalInfo = "Type: $($method['phoneType']), SMS State: $($method['smsSignInState'])"
}
'#microsoft.graph.passwordAuthenticationMethod' {
$authObject.MethodType = "Password"
$authObject.Created = $method['createdDateTime']
}
'#microsoft.graph.emailAuthenticationMethod' {
$authObject.MethodType = "Email"
$authObject.DisplayName = $method['emailAddress']
}
'#microsoft.graph.fido2AuthenticationMethod' {
$authObject.MethodType = "FIDO2"
$authObject.DisplayName = $method['displayName']
$authObject.Created = $method['createdDateTime']
$authObject.AdditionalInfo = "Model: $($method['model']), Attestation: $($method['attestationLevel'])"
}
'#microsoft.graph.windowsHelloForBusinessAuthenticationMethod' {
$authObject.MethodType = "Windows Hello"
$authObject.DisplayName = $method['displayName']
$authObject.Created = $method['createdDateTime']
$authObject.AdditionalInfo = "Key Strength: $($method['keyStrength'])"
}
'#microsoft.graph.microsoftAuthenticatorAuthenticationMethod' {
$authObject.MethodType = "Authenticator"
$authObject.DisplayName = $method['displayName']
$authObject.Created = $method['createdDateTime']
$authObject.AdditionalInfo = "Device: $($method['deviceTag']), Version: $($method['phoneAppVersion'])"
}
}
# Add each object to the array
$authMethodObjects += $authObject
}
# Display the results in GridView
$authMethodObjects | Out-GridView
This script provides a detailed view of all authentication methods configured for a user, including:
- Method type (e.g., FIDO2, Phone, Authenticator)
- Display name or identifier
- Creation date (where available)
- Additional method-specific information
By running this script regularly, you can:
- Ensure administrators are using FIDO2 security keys as their primary authentication method
- Identify and remove outdated or less secure authentication methods
- Track the adoption of new authentication methods across your organization
- Quickly audit a user’s authentication setup in case of suspicious activity
Remember to handle the output securely, as it contains sensitive information about user authentication methods.
Best Practices for Implementation
- Gradual rollout
- Start with a small group of admins and expand gradually.
- User education
- Train administrators on using FIDO2 keys and explain the security benefits.
- Regular reviews
- Periodically review and update policies to address new security needs.
- Monitor and adjust
- Use Entra ID or Microsoft Sentinel reporting to track policy effectiveness and user adoption.
- Test thoroughly
- Ensure policies work as intended in various scenarios before full deployment.
Overcoming Common Challenges
- User resistance
- Address concerns through clear communication about security benefits.
- Hardware logistics
- Plan for procurement and distribution of FIDO2 keys to admins.
- Emergency access
- Set up break-glass accounts with appropriate controls for urgent situations.
Conclusion
Authentication strength policies in Entra ID, particularly those using FIDO2 security keys for Azure administration, significantly improve an organization’s security posture. By implementing these policies, you create a strong defense against unauthorized access and protect critical cloud resources.
As cyber threats continue to evolve, adopting strong authentication methods becomes increasingly important. FIDO2 security keys represent the current gold standard for administrative access, offering a balance of security and usability.
By following the guidelines and best practices outlined in this post, you can enhance your Azure environment’s security, protect against sophisticated attacks, and ensure that only authorized administrators can access and manage your cloud resources.
Remember, strong authentication is not just a technical measure—it’s a fundamental part of a comprehensive security strategy. Start implementing these policies today to secure your Azure administration and stay ahead of potential threats.