Introduction
Security teams face a persistent challenge: effectively monitoring and responding to device vulnerabilities across their organization. While Microsoft Defender for Endpoint provides excellent vulnerability detection capabilities, the process of tracking, communicating, and managing these vulnerabilities often remains manual and time-consuming.
The Challenge of Modern Vulnerability Management
IT Security departments regularly struggle with several critical aspects of vulnerability management. Vulnerability data is typically isolated within security portals that aren’t regularly accessed by IT personnel responsible for remediation. Security teams waste valuable time generating manual reports, while device owners remain unaware of critical vulnerabilities affecting their systems. The result is delayed remediation, inefficient resource allocation, and persistent security gaps that could be exploited by attackers.
Most organizations have experienced the frustration of discovering that a critical vulnerability – which was detected months ago by their security tools – remains unpatched simply because the information never reached the right people in an actionable format.
This challenge is particularly acute for administrators who share devices between productivity and administrative tasks. These dual-purpose machines often accumulate unnecessary applications and missed patches, creating significant security exposure. Third-party application patching remains a persistent blind spot, with many organizations lacking visibility into which non-Microsoft applications need updates.
Introducing the Device Vulnerability Management Solution
Today, I’m excited to announce the release of a comprehensive Device Vulnerability Management Solution for Premium Members. This solution addresses the vulnerability communication gap by automating the entire process – from detection to targeted reporting.
The solution is specifically designed for IT and Security departments, not end users. It leverages Azure Automation, Microsoft Graph API, and Microsoft Defender XDR to collect vulnerability data and deliver professional HTML reports directly to IT administrators responsible for specific devices. By automating this workflow, security teams can ensure that vulnerability information consistently reaches the right technical personnel at the right time.
The end goal is clear: maintain administrator workstations and devices with only necessary applications, fully updated software, and minimal attack surface. By providing weekly actionable reports, administrators can maintain continuous device hygiene rather than relying on sporadic security reviews.
How It Works
The solution creates a seamless bridge between Microsoft Defender XDR’s vulnerability data and your IT teams. It retrieves vulnerability information through Microsoft’s APIs, processes the data to create comprehensive yet easy-to-understand reports, and delivers these reports through your preferred distribution method-either via on-premises Exchange or Azure Logic Apps.
What sets this solution apart is its targeted approach for IT professionals. Rather than generating generic reports covering all devices, it delivers customized reports specifically for devices managed by designated IT administrators. The solution pulls data from Intune based on specific User Principal Names (UPNs), ensuring that IT staff receive only relevant information about systems they’re responsible for maintaining and securing.
The reports highlight both Microsoft and third-party application vulnerabilities, giving administrators a complete view of their exposure. With scheduled weekly reporting, it establishes a consistent cadence for vulnerability remediation activities, ensuring that security hygiene becomes part of the regular work routine rather than an afterthought.
Key Benefits
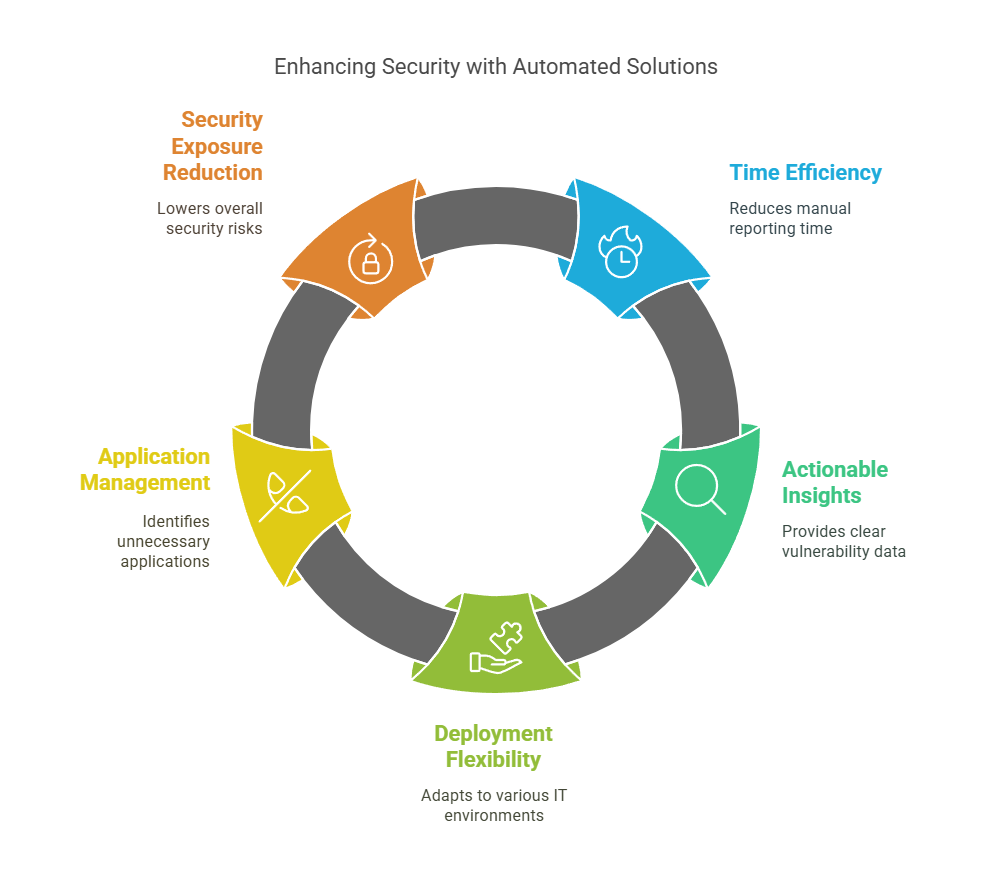
The automated solution dramatically reduces the time security teams spend on manual reporting while increasing the organization’s overall security posture. IT departments receive comprehensive, actionable vulnerability information without needing access to security portals. The solution includes complete vulnerability details in professional HTML format, making issues easy for technical staff to understand and prioritize.
With flexible deployment options, multi-platform support, and customizable reporting, the solution adapts to your organization’s specific IT environment rather than forcing you to adapt to it.
For administrators who use the same device for productivity and administrative work, this solution is particularly valuable. It helps maintain the principle of least functionality by identifying unnecessary or outdated applications that increase attack surface. The regular reporting cadence encourages prompt action on both Microsoft and third-party updates, significantly reducing overall security exposure.
Getting Started
The complete Device Vulnerability Management Solution is available now to all Premium Azure Solutions members. The documentation includes:
- A comprehensive architecture overview
- Step-by-step implementation guide
- Detailed configuration options
- Troubleshooting assistance
- PowerShell scripts for both on-premises Exchange and Logic App deployment
Visit the Premium Azure Solutions portal to access the solution today.
IMPORTANT! If you’re a Premium Member and haven’t received access credentials to the documentation portal yet, please check your email inbox or contact me directly for immediate assistance.
This solution represents our commitment to developing practical, production-ready automation that solves real security challenges for IT professionals. We’re continuing to expand our library of solution accelerators to help organizations maximize their Microsoft security investments.