Introduction
I have just published a new PowerShell module called DefenderforCloud on the PowerShell Gallery. This module allows Azure administrators to apply Microsoft Defender for Cloud pricing plans at the resource level, moving beyond the traditional subscription-level-only approach and providing flexibility for targeted configurations and proof of concept (POC) scenarios.
Module Overview
DefenderforCloud PowerShell module offers a targeted approach to security management within Azure. This module allows you to enable Defender for Cloud P1 on Azure VMs and Azure Arc for Servers. Currently no support for Virtual Machine Scale Sets.
Key features of this module include:
- Resource-Specific Security Management: Allows administrators to apply Defender plans directly to chosen resources, offering the ability to customize security settings to the specific needs of each resource.
- Comprehensive Functions: Includes capabilities to enable, remove, and retrieve pricing details for Defender plans, enhancing administrative control.
- Efficiency and Scalability: Automates the management of Defender plans, simplifying operations and reducing the administrative overhead in large-scale environments.
Key Functions
- Invoke-AzGraphQueryWithPagination
- This function facilitates querying Azure resources with pagination. It manages large datasets by breaking them into manageable segments, which is particularly useful for environments with a significant number of resources.
- Get-ServerPricingDetails
- Get-ServerPricingDetails retrieves the pricing details for Azure resources.
- Enable-DefenderPlan
- This function applies Defender plans to Azure resources by configuring the security settings at the resource level.
- Remove-DefenderPlan
- Remove-DefenderPlan allows for the deactivation of Defender plans on Azure resources.
- Get-AzureResources
- Get-AzureResources extracts details of Azure resources based (Azure VM or Azure Arc for Servers) on specified criteria such as resource type and tags.
Module Installation
To install the DefenderforCloud module from the PowerShell Gallery, use the following command:
Install-Module -Name Az.Accounts
Install-Module -Name Az.ResourceGraph
Install-Module -Name DefenderforCloud
Example: Enabling Defender Plans on Azure Arc or Azure VM Resources
First, connect to your Azure account and obtain an access token to authenticate further API requests. This step is important to ensure you have the necessary permissions to perform actions on the resources.
<#
=================================================================================
DISCLAIMER:
This script is provided "as-is" with no warranties. Usage of this script is at
your own risk. The author is not liable for any damages or losses arising from
using this script. Please review the full legal disclaimer at:
https://kaidojarvemets.com/legal-disclaimer/
=================================================================================
#>
# Connect to Azure and get an access token
Connect-AzAccount
$AccessToken = Get-AzAccessToken | Select-Object -ExpandProperty token
Use the Get-AzureResources function to fetch all Azure Arc resources within a specified resource group. This function will filter the resources based on the type set to “ARC” and the query type set to resource group (“RG”).
<#
=================================================================================
DISCLAIMER:
This script is provided "as-is" with no warranties. Usage of this script is at
your own risk. The author is not liable for any damages or losses arising from
using this script. Please review the full legal disclaimer at:
https://kaidojarvemets.com/legal-disclaimer/
=================================================================================
#>
# Retrieve Azure Arc resources from a specific resource group
$Servers = Get-AzureResources -ResourceType "ARC" -QueryType "RG" -ResourceGroupName "ARG-SERVERS" -SubscriptionId "MY SUBSCRIPTION ID" -AccessToken $AccessToken
If your Azure Arc servers are tagged for specific functionalities or features, you can use the Get-AzureResources function to select only those resources that match your tagging criteria. For example, to get all Arc servers that are tagged with “DEFENDER” set to “YES“:
<#
=================================================================================
DISCLAIMER:
This script is provided "as-is" with no warranties. Usage of this script is at
your own risk. The author is not liable for any damages or losses arising from
using this script. Please review the full legal disclaimer at:
https://kaidojarvemets.com/legal-disclaimer/
=================================================================================
#>
#Get Tag Based ARC Servers
$Servers = Get-AzureResources -ResourceType ARC -QueryType TAG -TagName "DEFENDER" -TagValue "YES" -AccessToken $AccessToken
In addition to fetching Azure Arc resources, the DefenderforCloud module also enables you to gather information about Azure Virtual Machines within a specific resource group or based on a tag name. This is especially helpful when you need to manage Defender plans for VMs. Here’s how to use the command:
<#
=================================================================================
DISCLAIMER:
This script is provided "as-is" with no warranties. Usage of this script is at
your own risk. The author is not liable for any damages or losses arising from
using this script. Please review the full legal disclaimer at:
https://kaidojarvemets.com/legal-disclaimer/
=================================================================================
#>
$Servers = Get-AzureResources -ResourceType VM -QueryType RG -ResourceGroupName "AZVM" -SubscriptionId "MY SUBSCRIPTION ID" -AccessToken $AccessToken
For each Azure Arc or Azure VM resource retrieved, apply a Defender plan using the Enable-DefenderPlan function. This function configures the Defender plan for each server by utilizing the pricing URL and server name extracted from the $Servers object. Before you are executing the Enable-DefenderPlan function, make sure to verify the results using the Out-GridView cmdlet. For example $Servers | Out-GridView.
<#
=================================================================================
DISCLAIMER:
This script is provided "as-is" with no warranties. Usage of this script is at
your own risk. The author is not liable for any damages or losses arising from
using this script. Please review the full legal disclaimer at:
https://kaidojarvemets.com/legal-disclaimer/
=================================================================================
#>
# Enable Defender plans on each server
$Servers | ForEach-Object {
Enable-DefenderPlan -AccessToken $AccessToken -PricingUrl $_.'Pricing URL' -ServerName $_.'Server Name'
}
Wait a few minutes to give the system enough time to apply the Defender plans across the selected resources. Then, re-run the Get-AzureResources function to retrieve the updated details of the Azure Arc resources and verify that the Defender plans have been successfully applied.
Verifying the Implementation
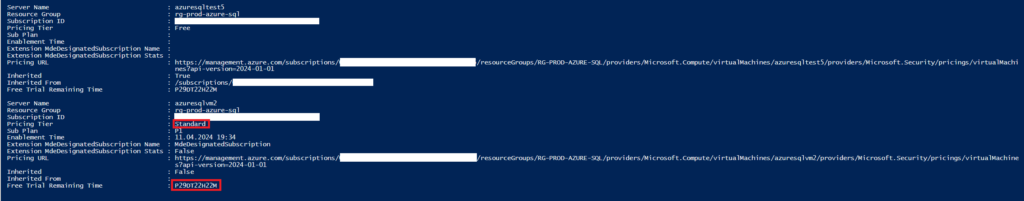
Once you’ve applied the Defender plans to your resources, it’s important to confirm the actions taken. By re-running the Get-AzureResources function after a short wait, you can obtain an output that displays the current status of each resource. Here’s how to interpret the key pieces of information in the output:
- Server Name: Displays the name assigned to the Azure server resource.
- Resource Group: Indicates the group where the server is categorized within Azure.
- Subscription ID: The unique ID for the Azure subscription encompassing the resource.
- Pricing Tier: Shows the level of the pricing plan applied, such as “Standard.”
- Sub Plan: Details the specific Defender plan, like “P1,” that’s active.
- Enablement Time: Timestamp marking when the Defender plan was enabled.
- Pricing URL: The endpoint for managing the resource’s Defender pricing details.
- Inherited: A Boolean value indicating if the pricing plan is inherited from the subscription level or not.
- Inherited From: If inherited, shows the source scope of the pricing plan.
- Free Trial Remaining Time: For those on a trial of the Defender plan, this states the time left.
In the provided output, there are entries for two servers. Notably, for azuresqlvm2, the ‘Inherited’ status is False, confirming that the Defender plan was applied directly to this server. This output confirms that the Defender plan configurations have been successfully implemented, and it provides all the necessary details for Azure administrators to verify the security settings of their resources.
Summary
The DefenderforCloud PowerShell module streamlines the way Azure administrators apply Microsoft Defender for Cloud pricing plans at the resource level. Tailoring security settings to each resource’s requirements is now more straightforward, enhancing control and flexibility in your security strategy.
The provided examples show the module’s practicality in handling Azure Arc servers or VMs, whether grouping them by resource group or pinpointing them with tags. This tool is about precision—giving you the ability to manage Azure’s security aspects more finely.