Introduction
Data collection and analysis across hybrid-cloud environments is crucial for modern organizations. As businesses adopt a mix of on-premises, private cloud, and public cloud services, managing and securing data becomes increasingly complex. Effective data collection strategies are key to addressing these challenges.
Core to these strategies are tools like Microsoft Sentinel, Azure Arc for hybrid infrastructure management, and the Azure Monitor Agent (AMA). Microsoft Sentinel provides robust security information and event management (SIEM) capabilities for identifying, assessing, and mitigating security threats. Azure Arc extends Azure’s management capabilities to diverse environments, enabling seamless resource management across the hybrid landscape. The Azure Monitor Agent (AMA) complements these services by offering a unified solution for collecting and analyzing telemetry data from various sources, enhancing monitoring, diagnostics, and analytics.
This blog post explores key components for data collection in hybrid-cloud environments. We’ll examine Data Collection Endpoints (DCE), Data Collection Rules (DCR), and the Azure Monitoring Agent (AMA) in depth. Our focus is on providing insights for IT professionals and technical architects aiming to optimize data collection strategies and ensure robust system performance and security in a hybrid-cloud setup.
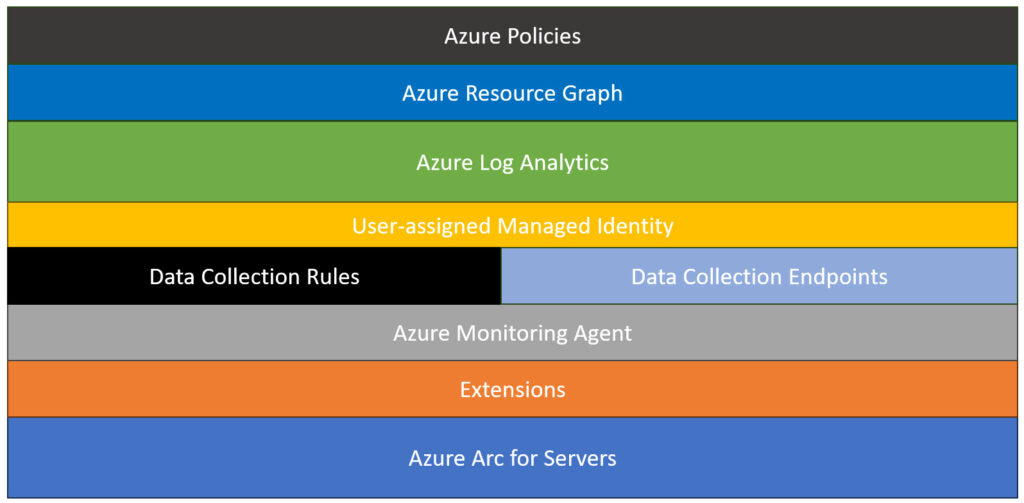
Below is a visual representation of the building blocks that comprise the architecture of hybrid-cloud data management, including Azure Policies, Azure Resource Graph, Azure Log Analytics, and other integral components for data collection and analysis.
Azure Monitoring Agent (AMA)
Overview of Azure Monitoring Agent (AMA)
The Azure Monitoring Agent (AMA) is a key tool in Azure’s data collection arsenal, designed to collect monitoring data from the guest operating systems of Azure and hybrid virtual machines. It then delivers this data to Azure Monitor for use by various features and services, including Microsoft Sentinel and Microsoft Defender for Cloud. Significantly, AMA replaces all of Azure Monitor’s legacy monitoring agents, streamlining the data collection process across different platforms.
Benefits of Using Azure Monitoring Agent
AMA offers several benefits that enhance data collection and management:
- Cost Efficiency: AMA enables targeted and granular data collection, as opposed to the “all or nothing” approach of legacy agents. This tailored collection, combined with filtering rules and data transformations, significantly reduces the volume of data uploaded, thus lowering ingestion and storage costs.
- Simpler Management: AMA supports data uploads to multiple destinations, including cross-region and cross-tenant data collection. Its centralized, cloud-based configuration allows for efficient troubleshooting and enterprise-scale management throughout the data collection lifecycle, including onboarding, deployment, updates, and changes.
- Security and Performance: Enhanced security is provided through Managed Identity and Microsoft Entra tokens, while event throughput is 25% better than the legacy Log Analytics (MMA/OMS) agents.
Deployment Recommendations
It is recommended to deploy AMA on all new virtual machines, scale sets, and on-premises servers to collect data for supported services and features. For machines already deployed with legacy Log Analytics agents, a migration to Azure Monitor Agent is advised before August 2024, after which the legacy agents will no longer be supported.
Integration with Data Collection Rules (DCRs)
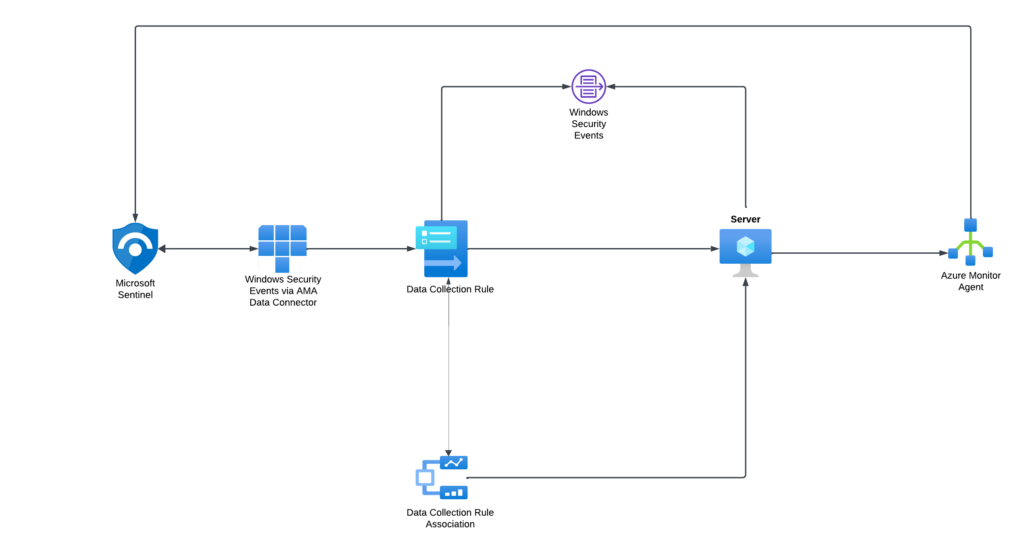
AMA utilizes data collection rules (DCRs) to define what data each agent should collect. DCRs allow for scalable management of data collection settings and the definition of unique configurations for subsets of machines. This means data can be sent from multiple machines to multiple destinations across regions and tenants, providing a flexible and efficient data collection framework.
Data Collection Rule Associations (DCRAs)
DCRAs associate a DCR with an object being monitored, such as a virtual machine equipped with AMA. These associations enable a single object to be linked with multiple DCRs and vice versa. When AMA is installed, it connects to Azure Monitor to retrieve any relevant DCRs, which then guide the agent on what data to collect from the machine. Azure Monitor also references these DCRs to decide whether a transformation should be applied to the data before sending it to the designated workspace and table.
Data Collection Endpoints (DCE) in Azure Monitor
Overview of Data Collection Endpoints (DCE)
Data Collection Endpoints (DCE) in Azure Monitor serve as vital connections for processing and ingesting data into Azure Monitor. These endpoints are used by the Logs ingestion API and the Azure Monitor Agent (AMA) to handle collected data and configuration files.
Deployment and Regional Considerations
The setup of DCEs in Azure Monitor depends on the location of the monitored resources and Log Analytics workspaces. The configuration of DCEs involves region-specific considerations, ensuring that the data collection aligns with the geographical distribution of resources and workspaces.
- Single Region Scenario: When all monitored resources are in the same region as the destination Log Analytics workspace, a single DCE is established to manage the data and configuration files.
- Cross-Region Scenario: In situations where monitored resources and Log Analytics workspaces are in different regions, a DCE is created in each region where the Azure Monitor Agent is deployed. This setup facilitates the transmission of configuration files to agents in their respective regions. Additionally, data from all resources is sent to a DCE located in the region of the destination Log Analytics workspace.
- Multiple Regions and Workspaces: For environments with monitored resources and multiple Log Analytics workspaces across different regions, a DCE is set up in each region where Azure Monitor Agent is deployed and in each region with a destination Log Analytics workspace. This ensures that data is sent from each monitored resource to the appropriate regional DCE.
Understanding Log Types and Their Dependencies on DCEs
Different Log Types and DCE Requirements
In the intricate ecosystem of hybrid-cloud data collection, understanding the relationship between various log types and their dependencies on Data Collection Endpoints (DCEs) is essential. Each type of log has unique characteristics and requirements that dictate how they should be collected and processed. This section will explore some common log types and how their dependency on DCEs varies.
Here’s a breakdown of some common log types and their DCE dependencies:
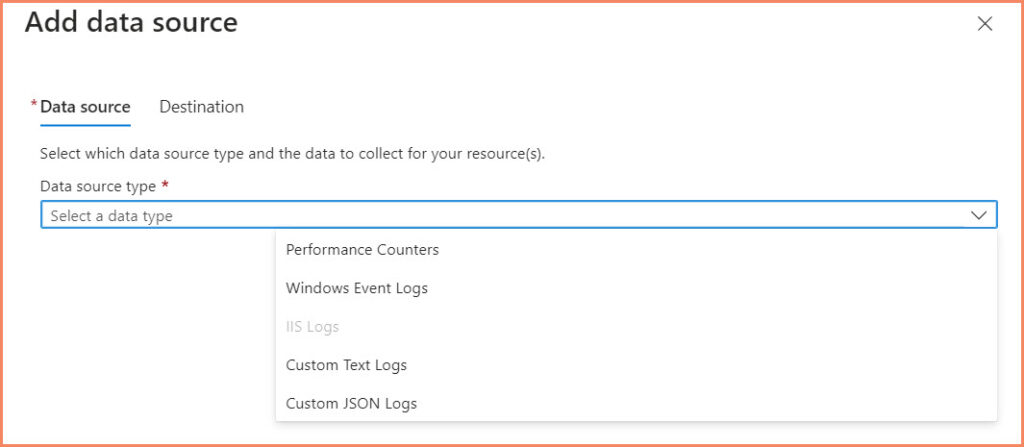
- IIS Logs
- Needs a Data Collection Endpoint: Yes
- IIS logs, which provide valuable information about the web server operations, require a DCE for effective collection and transmission.
- Custom Text Logs
- Needs a Data Collection Endpoint: Yes
- These logs, often unique to specific applications or systems, also necessitate a DCE for proper aggregation and analysis.
- Custom JSON Logs
- Needs a Data Collection Endpoint: Yes
- Given their structured nature, JSON logs are crucial for detailed data analysis and thus require a DCE to ensure accurate and timely collection.
- Performance Metrics, Windows Security Logs, Syslog, etc.
- Needs a Data Collection Endpoint: No
The Functionality and Importance of Data Collection Rules (DCR)
Understanding Data Collection Rules (DCR)
Data Collection Rules (DCR) are a fundamental component in the architecture of modern data collection frameworks, especially in hybrid-cloud environments. DCRs are essentially sets of instructions or policies that define how data should be collected, what data should be collected, and the way this data should be processed and forwarded. These rules are crucial in tailoring the data collection process to meet the specific needs and objectives of an organization.
The Dual Role of DCR
DCRs play a dual role in the data collection framework. Firstly, they specify the types of data to be collected. This can range from system metrics and logs, such as Windows Security Logs and application logs, to more specific data like performance counters or custom event logs. The ability to define what types of data to collect is vital for ensuring that the gathered information is relevant and valuable for the organization’s specific monitoring and analytical needs.
Secondly, DCRs determine how this data is processed and where it is forwarded. This involves specifying the pathways through which data travels, the transformation or filtration it undergoes, and ultimately, where it is stored or analyzed. By controlling these aspects, DCRs ensure that the data collection process is not only efficient but also aligned with security policies and compliance requirements.
Impact on Monitoring, Analytics, and Data Management
The implementation and configuration of DCRs have a significant impact on various aspects of an organization’s IT infrastructure. In terms of monitoring, DCRs enable the collection of targeted data that is most relevant to an organization’s monitoring objectives. This targeted approach leads to more efficient monitoring practices and helps in quickly pinpointing and resolving issues within the IT environment.
In the realm of analytics, DCRs ensure that the data being analyzed is accurate, relevant, and timely. By filtering out unnecessary data, DCRs contribute to more streamlined and effective analytical processes. This can lead to more insightful business intelligence and better-informed decision-making.
From a broader data management perspective, DCRs are instrumental in shaping an organization’s overall data strategy. They play a critical role in managing data flow, ensuring data integrity, and maintaining compliance with regulatory standards. By optimizing data collection and processing, DCRs contribute to the overall efficiency and effectiveness of the organization’s data management framework.
Azure Arc’s Role in Streamlining Data Collection
Overview of Azure Arc
Azure Arc represents a significant advancement in the management and governance of resources across hybrid-cloud environments. It is a set of technologies that extends Azure’s management capabilities to on-premises, multi-cloud, and edge environments, effectively bringing the Azure framework to a wide range of infrastructures. This unification is particularly beneficial in data collection, where consistency and control across diverse environments are paramount.
Relevance of Azure Arc in Data Collection
In the context of data collection, Azure Arc’s relevance is multifaceted. It enables organizations to implement consistent data collection practices across all their environments, whether they are on Azure, on-premises, or on other cloud platforms. This consistency is crucial for ensuring comprehensive monitoring, effective analytics, and streamlined management of data collection policies and procedures.
Integration with AMA, DCR, and DCE
The integration of Azure Arc with Azure Monitoring Agent (AMA), Data Collection Rules (DCR), and Data Collection Endpoints (DCE) forms the backbone of a cohesive data collection strategy in hybrid-cloud environments.
- With AMA: Azure Arc facilitates the deployment and management of AMA across various environments. This allows for uniform data collection practices, whether the resources are in Azure or outside of it. Through Azure Arc, AMA can be implemented consistently, ensuring that telemetry data from various sources is collected efficiently and securely.
- Through DCR: Azure Arc enhances the functionality of DCRs by enabling centralized management of data collection policies across diverse environments. This centralized approach simplifies the governance of data collection rules and ensures that they are consistently applied, regardless of where the resources are located.
- In Relation to DCE: The integration of Azure Arc with DCEs ensures that data collected from various environments is directed to the appropriate endpoints for processing and analysis. This integration is key to maintaining the efficiency and effectiveness of the data collection process, especially in complex hybrid-cloud environments.
Understanding User-Assigned vs System-Assigned Identities
Introduction to Managed Identities
Managed identities in Azure provide Azure services with an automatically managed identity in Entra ID (Azure AD), simplifying identity management for cloud applications. There are two primary types of managed identities: User-Assigned and System-Assigned.
System-Assigned Identities
System-Assigned Identities are directly tied to a specific Azure service instance, like an Azure VM or Azure App Service. These identities are inherently linked to the lifecycle of the service they are associated with:
- Lifecycle Management: When the service instance is deleted, the identity is automatically cleaned up by Azure, preventing orphaned identities.
- Ease of Setup: They are easy to set up and use, making them suitable for straightforward applications tied to a single service.
User-Assigned Identities
User-Assigned Identities, on the other hand, are independent and need to be created as standalone Azure resources. They offer more flexibility:
- Flexibility and Reusability: They can be associated with multiple Azure services and reused across different applications.
- Independent Lifecycle: These identities exist independently of the service instances they are associated with, offering more control over identity management.
- Simplified Role Management: Role assignments are retained even if the service instance is deleted, streamlining permission management in larger deployments.
- Enhanced Security and Compliance: User-assigned identities provide a more granular control over access, crucial for strict security and compliance standards.
Advantages of User-Assigned Identities
User-Assigned Identities are generally recommended, especially in complex environments and for services like Azure Monitor Agent (AMA) deployments:
- Flexibility in Dynamic Environments: In scenarios where resources have dynamic lifecycles or where identities need to be managed across multiple resources, user-assigned identities offer greater versatility.
- Stability and Control: They provide stability and control over identity management, essential in large-scale or complex deployments.
- Recommendation for AMA Deployment: For Azure Monitor Agent deployment, user-assigned identities are recommended due to their flexibility and independent lifecycle management. This approach aligns better with the dynamic and often complex requirements of modern cloud environments.
Integrating Azure Resource Graph in Hybrid-Cloud Data Management
Understanding Azure Resource Graph
With the evolution of hybrid-cloud environments, particularly with the integration of Azure Arc and other Azure services, data management extends beyond traditional confines like Log Analytics Workspaces. This is where Azure Resource Graph becomes a pivotal tool. It offers a comprehensive view across various Azure resources, enabling efficient data exploration and analysis across large-scale environments.
Azure Resource Graph and Hybrid-Cloud Data
Azure Resource Graph plays a crucial role in managing the complexity and scale of data in hybrid-cloud setups that incorporate Azure Arc and other Azure components:
- Extensive Data Querying: It enables advanced querying capabilities to explore Azure resources, providing insights that are more comprehensive compared to limited workspace-centric data views.
- Cross-Resource Visibility: Azure Resource Graph allows for a unified view of resources across different Azure services and deployments, crucial for maintaining consistency and oversight in complex environments.
- Integration with Azure Arc: With Azure Arc’s capability to extend Azure services beyond the Azure platform, Azure Resource Graph becomes even more significant. It allows for a unified data querying and exploration experience, regardless of where the resources are physically deployed.
The Synergy with Azure Arc
The integration of Azure Resource Graph with Azure Arc enhances the management of resources across hybrid-cloud environments:
- Unified Data Management: This integration offers a cohesive approach to managing data and resources, whether they are on Azure or external platforms managed through Azure Arc.
- Streamlined Compliance and Reporting: By providing a unified view of resources, Azure Resource Graph aids in streamlining compliance reporting and resource monitoring, making it easier to track and manage resources across a diverse environment.
Conclusion
The Azure Monitoring Agent (AMA) marks a significant progression from its predecessor, offering enhanced capabilities in data collection, security, and efficiency. Its integration across Azure and non-Azure environments exemplifies the evolving nature of cloud services. Data Collection Rules (DCR) are the strategic backbone, dictating what data is collected and how it is processed, profoundly impacting monitoring, analytics, and overall data management strategies.
Azure Arc emerges as a unifying force, bringing together diverse environments under a single management umbrella. Its integration with AMA, DCR, and DCE is instrumental in crafting a cohesive and efficient data collection strategy, ensuring consistency and control across all platforms.
Call to Action
As we wrap up our exploration of the key components in hybrid-cloud data collection, we extend an invitation to our readers to engage further with these concepts. The domains of Azure Monitoring Agent (AMA), Data Collection Rules (DCRs), Data Collection Endpoints (DCE), and the integration of Azure Arc present a landscape rich in complexity and opportunity. To truly master data collection in hybrid-cloud environments, one must embrace a journey of continuous learning and adaptation.
To aid in this journey, we are excited to announce an upcoming training session. On May 16th, delve deeper into Azure’s capabilities at the One-Day Training on Azure Arc for Servers Implementation, an event promising to be an enriching experience for those looking to deepen their understanding of managing servers across hybrid environments.
For a more comprehensive engagement, consider exploring our Hybrid Cloud Modernization Program, designed to provide extensive insights and practical solutions in hybrid-cloud technology.
We also invite our readers to share their insights, experiences, and questions in the comments below. Your contributions are invaluable in fostering a collaborative and knowledgeable community. Whether you are an IT professional, a technical architect, or simply someone interested in the nuances of cloud technology, your perspective adds depth to our collective understanding.
Together, let’s navigate the complexities of hybrid-cloud data collection and pave the way towards more efficient, secure, and compliant IT infrastructures. Join us in this endeavor and be a part of a community that drives innovation and excellence in the cloud technology space.