Understanding Advanced Hunting with Microsoft Defender for Identity
Building on our previous discussions about Microsoft Defender for Identity (MDI), let’s delve deeper into one of its most potent features: advanced hunting. While we’ve established the foundational role of MDI in safeguarding digital identities, advanced hunting takes this protection to the next level.
Advanced hunting is all about proactivity. Rather than waiting for threats to manifest, it actively scours through extensive data, searching for signs of potential threats. This approach allows organizations to anticipate and identify vulnerabilities before they can be exploited, providing a robust, preemptive layer of defense.
With the real-time querying capabilities of MDI’s advanced hunting, organizations gain the ability to sift through vast datasets swiftly. This not only ensures timely threat detection but also empowers businesses to stay ahead of potential cyber adversaries.
As we continue this series, it’s essential to recognize the value of tools like MDI’s advanced hunting. In a world where cyber threats are constantly evolving, being equipped with proactive defense mechanisms is crucial for maintaining a secure digital environment.
Diving Deep into the Advanced Hunting Tables
In cybersecurity, the adage “knowledge is power” couldn’t be more accurate. The depth and breadth of data at our disposal can often be the difference between detecting a threat in its infancy or reacting to a full-blown breach. Microsoft Defender for Identity (MDI) understands this imperative. It presents a suite of advanced hunting tables, each tailored to harvest precise data points, ensuring a 360° visibility into identity-centric activities. This granular data is invaluable for incident responders; without it, piecing together the puzzle of a cyber intrusion becomes exponentially challenging.
Let’s explore these tables further and unveil the insights they bring to the table.
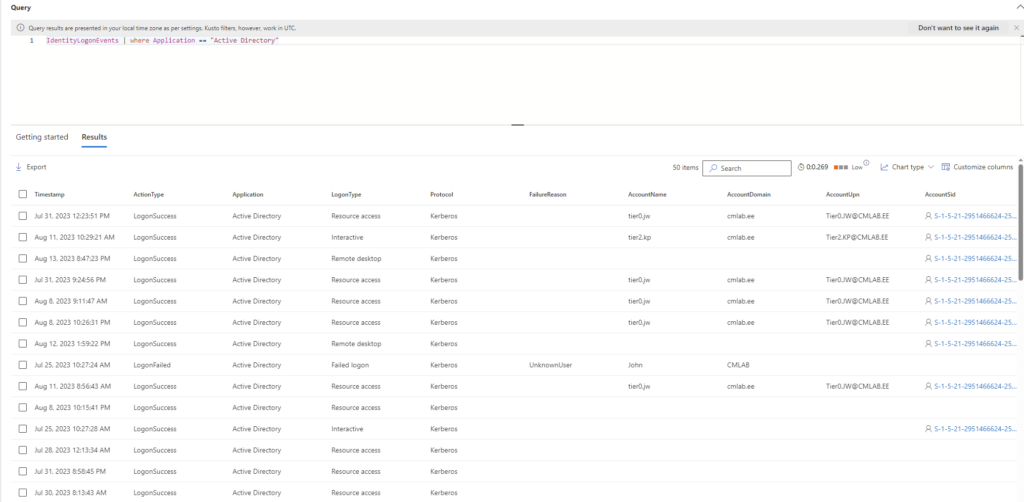
IdentityLogonEvents Table
The IdentityLogonEvents table in Microsoft Defender for Identity plays a pivotal role in capturing authentication events across a myriad of Microsoft services. It offers a granular perspective, detailing not only the specifics of user access patterns but also shedding light on the exact services being engaged. By keeping a vigilant eye on these events, organizations can preemptively identify and address potential security anomalies, ensuring a robust defense against unauthorized access.
This table is more than just a log; it’s a window into user interactions across different services such as Active Directory, Teams, Power BI, SharePoint Online etc. As we continue our series, anticipate more in-depth explorations into the intricacies of Microsoft Defender for Identity and its capabilities. Stay tuned!
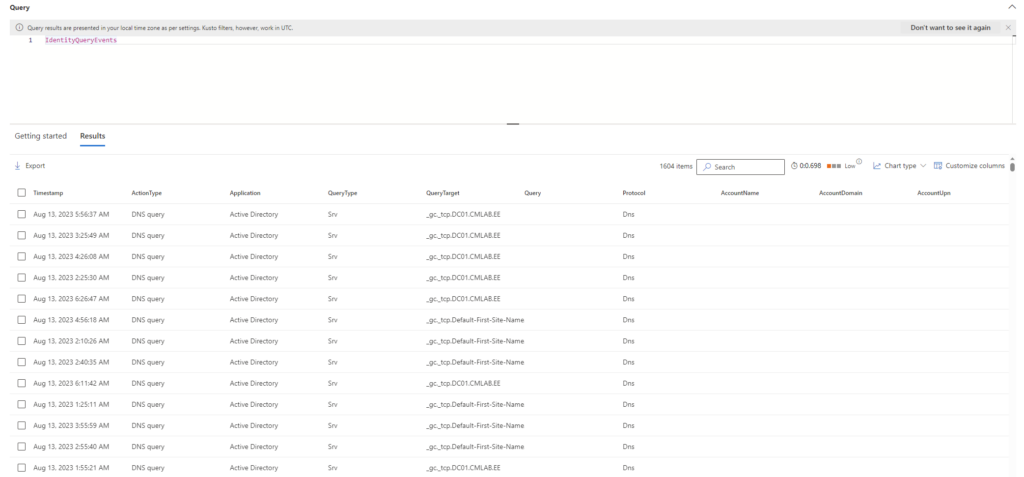
IdentityQueryEvents Table
The IdentityQueryEvents table in Microsoft Defender for Identity is purpose-built to monitor queries directed at AD. It provides a comprehensive log of all queries, enabling organizations to confirm the legitimacy of each request.
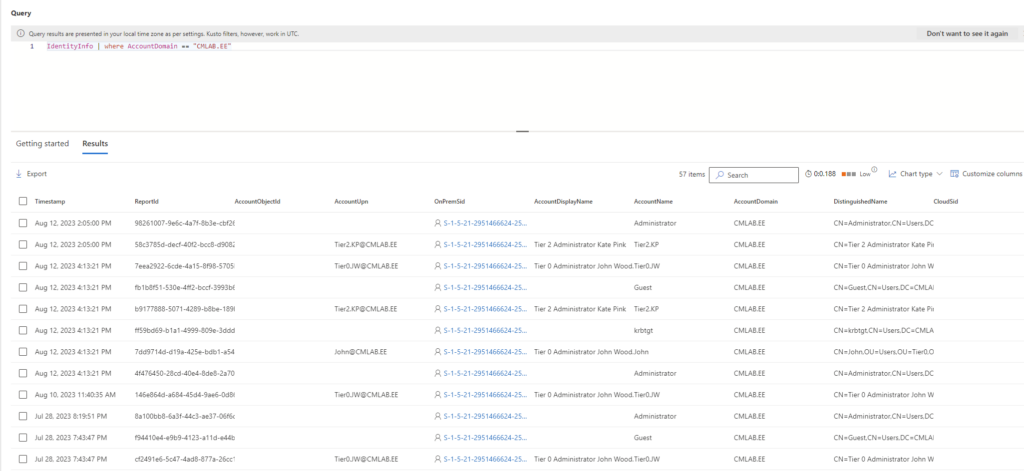
IdentityInfo Table
The IdentityInfo table consolidates data from both on-premises Active Directory and Entra ID (formerly known as Azure AD). By bringing together this information, it offers a unified view of user identities, bridging the gap between traditional infrastructure and modern cloud-based services.
Key Benefits
- Holistic View: With the integration of on-premises AD and Entra ID data, organizations get a comprehensive picture of user identities, ensuring no detail is overlooked.
- Consistency: By centralizing user account information, the table ensures that all account details remain consistent across various platforms and services.
- Enhanced Analytics and Hunting: The rich data provided by the IdentityInfo table empowers organizations to build watchlists in Sentinel. These watchlists can be instrumental in crafting analytics rules and facilitating advanced threat hunting, ensuring that potential vulnerabilities or malicious activities don’t go unnoticed.
- Streamlined Management: With all user identity data in one place, IT teams can more efficiently manage accounts, ensuring that permissions are correctly assigned and that any anomalies in user behavior are promptly addressed.
With this table in our hands, we can build up interesting use cases and solutions.
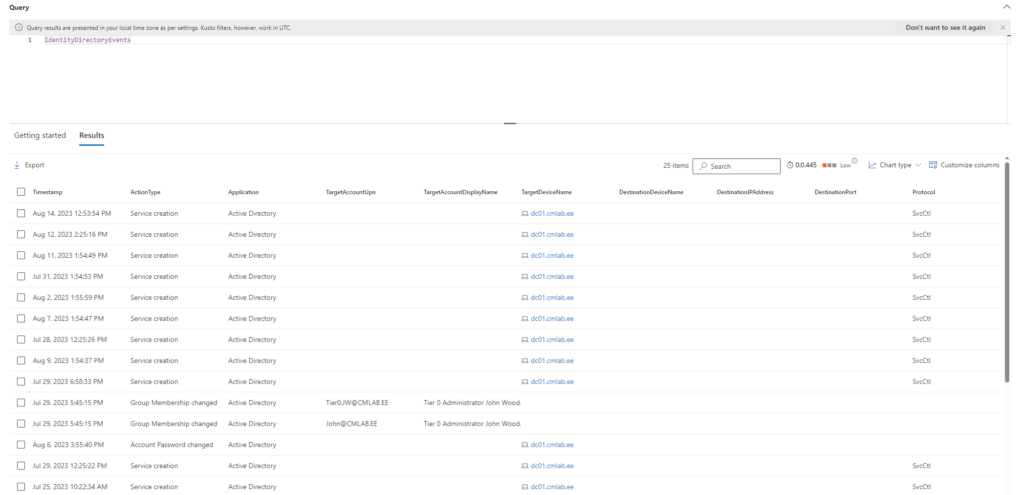
IdentityDirectoryEvents Table
The IdentityDirectoryEvents table in Microsoft Defender for Identity is a crucial tool for organizations utilizing on-premises domain controllers with Active Directory. This table meticulously tracks and logs all events associated with these controllers. From new service installations, PowerShell script executions, to changes in user account details or group memberships, every action is recorded.
For instance, the ActionType column alone can reveal:
- New service installations, indicating potential software updates or the introduction of new tools.
- PowerShell script executions, which might suggest administrative tasks or, in some cases, malicious activities.
- Changes in account details, such as password modifications, UPN name alterations, or even account expirations, providing a clear picture of user account management activities.
Furthermore, the table can highlight potential security concerns, such as the identification of potential lateral movement paths or instances of private data retrieval.
The IdentityDirectoryEvents table offers a comprehensive overview of all directory-related activities, ensuring that organizations maintain the sanctity and security of their domain. Leveraging the rich data from this table allows businesses to bolster their defenses and stay ahead of potential cyber threats.
Advanced Hunting through the security.microsoft.com portal
The security.microsoft.com portal is a cornerstone of Microsoft’s security ecosystem, serving as a unified platform for all Microsoft 365 Defender products. This consolidation provides administrators and security engineers with unparalleled oversight and control, streamlining their efforts in a single, powerful interface. When combined with Microsoft Defender for Identity (MDI), it offers an even more robust defense layer. And for those instances where deeper analysis is required, data can be seamlessly integrated into Sentinel, ensuring that organizations are always equipped to counter the most sophisticated of cyber threats. One platform, multiple solutions, infinite possibilities.
- Seamless Integration with MDI: The security.microsoft.com portal effortlessly integrates with MDI. This synergy ensures that the intricate data from MDI’s advanced hunting tables is easily accessible. From tracking authentication events to scrutinizing Active Directory queries or delving into user account details, the portal offers a cohesive platform for data visualization and analysis.
- Real-time Monitoring: The portal excels in offering real-time monitoring capabilities. With continuous data influx from MDI, organizations gain an immediate overview of their identity-centric activities, promptly identifying any deviations or suspicious undertakings.
- Alerts and Notifications: The portal is adept at generating context-rich alerts, drawing from the MDI data. These notifications provide a granular understanding of the threat type, the entities involved, and potential repercussions, ensuring that security teams are always in the know.
- Swift Response Mechanisms: Merely identifying threats isn’t enough; timely and effective action is paramount. The portal facilitates this with its integrated tools. Whether it’s enforcing a password reset, disabling a user, or delving into a comprehensive investigation, the portal streamlines these actions, ensuring threats are neutralized promptly.
The integration of MDI with the security.microsoft.com portal showcases Microsoft’s dedication to creating a comprehensive security environment. This unified platform, equipped with real-time monitoring, detailed alerts, and efficient response tools, empowers organizations to fortify their digital identities against the ever-present cyber challenges.
Crafting Proactive Defense Strategies with MDI
Integration is King
The power of Microsoft 365 Defender lies in its unified platform. By seamlessly integrating Defender for Endpoint, Defender for Office 365, Defender for Cloud Apps, and MDI, it provides a centralized hub for all your security needs. This all-in-one portal not only offers a wealth of information but also facilitates direct actions – from device isolation to log collection and live response.
Harness the Power of Unified Threat Detection
The platform’s strength is its ability to amalgamate data from diverse Microsoft security solutions, offering a comprehensive perspective on potential threats. This unified approach ensures that even the most intricate vulnerabilities are promptly detected and addressed, making the most of the interconnected data from various sources.
Maintain a Robust Security Posture
Consistency in security measures is paramount. With everything housed under one roof in the Microsoft 365 Defender portal, organizations can ensure that all protective measures are harmoniously aligned, eliminating potential gaps in defense.
Swift and Coordinated Responses
In the face of a security incident, rapid response is crucial. The integrated tools within the Microsoft 365 Defender portal enable swift, coordinated actions against threats, from isolating affected systems to launching in-depth threat assessments.
Stay Ahead with Adaptive Security
Cyber threats are ever-evolving. The Microsoft 365 Defender platform is designed to not only address current challenges but also to anticipate and adapt to future threats, ensuring organizations remain resilient against the shifting cyber landscape.
Maximize Efficiency with Automation
Operational efficiency is at the forefront of the Microsoft 365 Defender design. Through automation, routine tasks are streamlined, reducing the potential for human error and allowing IT teams to focus on strategic security initiatives.
With the unified Microsoft 365 Defender portal, organizations are equipped with a comprehensive, integrated approach to digital security, ensuring resilience and readiness in the face of diverse cyber challenges.
Conclusion
In today’s intricate digital ecosystem, the need for a unified, comprehensive security solution has never been more pressing. The Microsoft 365 Defender portal stands out as a beacon, offering organizations a centralized hub that integrates various Microsoft security solutions. By providing a holistic view of potential threats and facilitating swift, coordinated responses, the platform ensures that organizations remain resilient and proactive in their defense strategies. The future of cybersecurity lies in integration, and with Microsoft 365 Defender, that future is here.
Empower Your Cybersecurity Journey
Explore my Defender for Identity and Sentinel service offerings to learn how I can assist in implementing and optimizing these solutions for your business. For deeper insights, discussions, and expert advice, consider joining my blog membership and be part of a community that prioritizes cybersecurity excellence.
Don’t Wait for a Breach
Be proactive and safeguard your organization’s future today. Cyber threats are evolving, and preparation is key. By taking steps now to enhance your cybersecurity measures, you’re investing in the resilience and security of your organization’s digital assets.
Reserve your spot now and take the first step towards a more secure future.