Azure Monitoring Agent (AMA) allows us to collect logs and other performance and diagnostic data from virtual machines(Windows or Linux). If you use Microsoft Sentinel to monitor your hybrid-cloud environment, you may have already enabled the Azure Monitoring Agent Extension on your servers to collect data from these machines. AMA uses Data Collection Rules to collect event logs, performance data, etc., from the servers.
As an administrator, it is super important that the AMA Extension is installed on every server.
If you manage Microsoft Sentinel in your organization, you can configure the following detection rule to detect instances of the AMA (Azure Monitoring Agent) Extension being uninstalled. If necessary, you can scope this rule to apply only to specific nodes or other resources.
Prerequisites:
- Azure Log Analytics Workspace
- Microsoft Sentinel
- Azure Activity Data Connector configured
- Azure Arc Connected Machines
In this KQL query I’m using the AzureActivity table and filtering data based on the OperationNameValue. OperationNameValue must be “MICROSOFT.HYBRIDCOMPUTE/MACHINES/EXTENSIONS/DELETE“
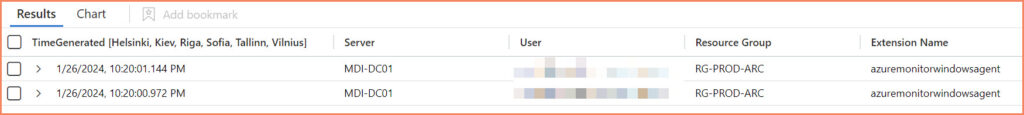
AzureActivity | where OperationNameValue == "MICROSOFT.HYBRIDCOMPUTE/MACHINES/EXTENSIONS/DELETE" and ActivityStatusValue == "Success"
| extend Properties = (parse_json(Properties))
| extend Server = toupper(split(Properties.resource,"/")[0])
| extend ["Extension Name"] = split(Properties.resource,"/")[1]
| extend User = Properties.caller
| extend ["Resource Group"] = Properties.resourceGroup
| extend ["Susbcription ID"] = Properties.SubscriptionId
| extend ["IP Address"] = CallerIpAddress
| extend ["Activity Status"] = Properties.activityStatusValue
| where ['Extension Name'] == "amawindows" or ['Extension Name'] == "azuremonitorwindowsagent"
| project TimeGenerated,Server, User, ['Resource Group'],["Extension Name"],['Susbcription ID'], ['IP Address'],["Activity Status"]
| sort by TimeGenerated