Introduction
Many IT professionals find themselves at a crossroads when it comes to monitoring the Windows Local Administrator Password Solution (LAPS). You might have LAPS in place to ensure unique, regularly rotated passwords on your organization’s machines, but gaining clear insight into who’s accessing these credentials and when can be a challenge. Without that visibility, it’s tough to catch unusual behavior before it turns into a security incident.
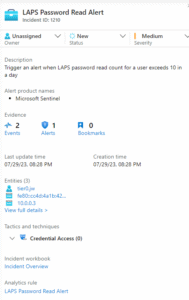
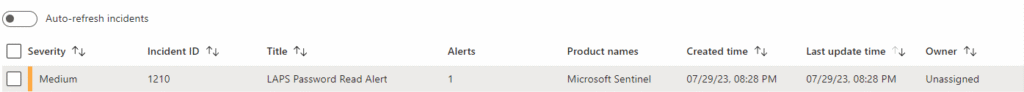
Imagine having a practical approach that helps you spot suspicious LAPS password retrieval events long before they lead to real trouble. Microsoft Sentinel, combined with the right event logs, can provide exactly that kind of insight. This guide will show you how to track LAPS activity using Event ID 4662. The goal is to hand you a set of clear instructions, turning guesswork into a solid understanding of what’s happening behind the scenes.
Why Visibility Matters
Picture this scenario: Your organization rolled out LAPS months ago, expecting it to lock down local administrator passwords. It did, but now questions linger. How do you verify that no one is pulling these passwords at odd hours? What if a compromised account is repeatedly retrieving credentials? You might never spot these patterns if you’re relying on guesswork or partial data.
This is where Sentinel and Event ID 4662 come into play. By keeping an eye on the right logs, you can pinpoint suspicious activity and respond before it does any harm. We’ve created a 15-page PDF guide to give you the roadmap you need – step-by-step instructions, real-world examples, and hands-on exercises that don’t leave you scratching your head.
Introducing The Premium Guide: “LAPS Activity Monitoring with Event ID 4662”
Available exclusively to our paying members, this resource is designed to turn you into someone who not only understands LAPS monitoring but can put it to work right away. Instead of trudging through scattered documentation, you’ll find everything you need in one place—clear explanations, practical examples, and meaningful exercises.
What Makes This Guide Worth Your Time
- Plain language: We avoid jargon and break down concepts so that both beginners and seasoned pros can follow along.
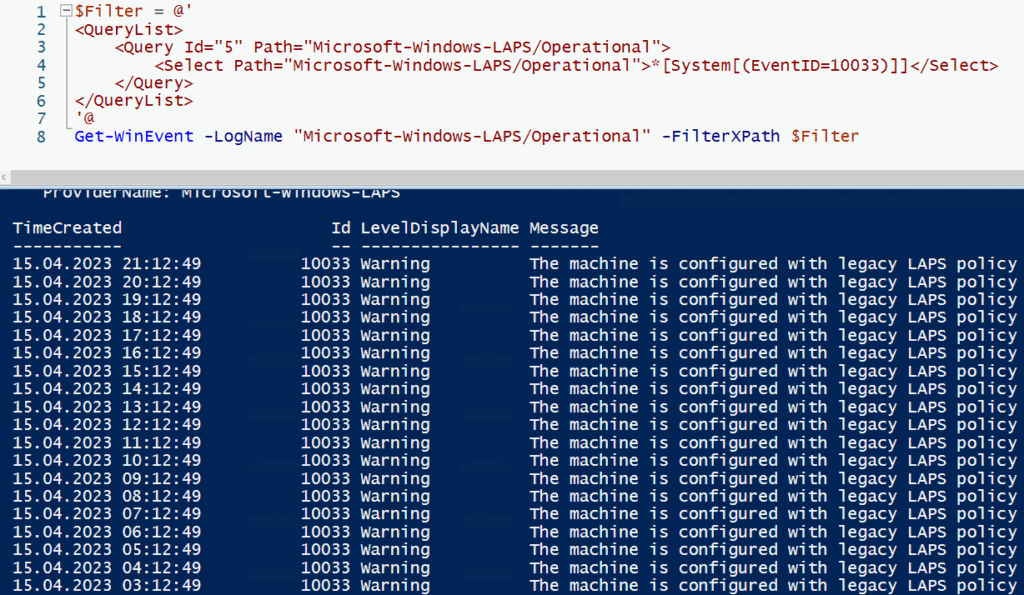
- Step-by-step instructions: We walk you through enabling audit settings in Active Directory, setting up Sentinel for these events, and writing your own KQL queries.
- Practical insights: Learn how to read LAPS passwords directly from Active Directory and understand the meaning behind GUIDs so you can quickly translate them into attributes.
What’s Inside the 15-Page PDF
- LAPS and Sentinel Setup
- Why pairing LAPS with Sentinel logging matters for your security posture.
- How Event ID 4662 fits into the picture.
- Understanding Event ID 4662
- What this event means and why you should pay attention.
- Identifying the signs that indicate suspicious behavior.
- Configuring Your Environment
- Adjusting audit settings in Active Directory so you’re capturing what you need.
- Fine-tuning Object Auditing to avoid unnecessary noise.
- Working with Sentinel
- Setting up Sentinel specifically to track these events.
- Writing KQL queries to find patterns, detect anomalies, and generate alerts.
- Creating custom analytics rules to stay ahead of issues.
- Navigating the Incident View so you can respond quickly.
- Hands-On Exercises
- Test your skills by retrieving LAPS passwords from Active Directory.
- Translate GUIDs into attributes you can actually use for investigations.
- Apply what you’ve learned through real-world scenarios.
Why This Matters for IT Pros
This guide doesn’t just hand you information—it shows you how to turn that information into action. After reading it, you’ll know where to look for suspicious activity, which queries to run, and how to use Sentinel’s features to your advantage. Instead of wondering if someone’s up to no good, you’ll have the tools to find out and respond.
Ready to Get Started?
Don’t leave your LAPS implementation only half-finished. By knowing how to track and analyze LAPS events, you put yourself in a stronger position to catch early warning signs and protect your systems. If you’re a premium member, you can access this guide now and start putting these ideas into practice.
The guide is now available on docs.kaidojarvemets.com, our new content platform, exclusively for premium members. If you’re a premium member and don’t have access yet, please let me know.
- Access the Guide: Tracking Windows LAPS Activity with Sentinel through Event ID 4662
Expand Your Windows LAPS Knowledge
Want to learn more? Check out these related resources:
- Monitoring Windows LAPS Deployment with Azure Workbook – Kaido Järvemets (kaidojarvemets.com)
- Your Ultimate Guide to Windows Local Administrator Password Solution (LAPS) – Kaido Järvemets (kaidojarvemets.com)
- KQL Queries for Windows LAPS Migration – Kaido Järvemets (kaidojarvemets.com)
- Monitor Windows LAPS Events with Microsoft Sentinel – Kaido Järvemets (kaidojarvemets.com)
- How to Update the Windows Server Active Directory Schema for the Latest Version of Windows LAPS – Kaido Järvemets (kaidojarvemets.com)
- Windows LAPS – New Group Policy Settings – Kaido Järvemets (kaidojarvemets.com)
- Windows LAPS EventIDs and XPath Queries – Kaido Järvemets (kaidojarvemets.com)
- Windows LAPS PowerShell Commands – Kaido Järvemets (kaidojarvemets.com)
For in-depth, personalized assistance with Microsoft Sentinel, explore our Microsoft Sentinel Services.