In this blog post, we will explore how to retrieve Entra ID logs using Microsoft.Graph PowerShell Module. Entra ID Sign-In logs provide important insights into user authentication events, helping organizations monitor security and troubleshoot potential issues. The Microsoft.Graph PowerShell Module simplifies the process of accessing these logs, allowing you to manage and analyze them with ease.
Prerequisites
- Entra ID Global Administrator
- Latest Microsoft Graph PowerShell module
- PowerShell 7.x
- Visual Studio Code
Step 1: Install Microsoft.Graph PowerShell Module
First we need to install the Microsoft Graph PowerShell module:
Install-Module -Name Microsoft.Graph -Force -Verbose
Step 2: Define the desired permission scopes
We need to define the permission scopes required to access role management information in Entra ID. The following scopes are required to retrieve information about eligible role assignments:
$Scopes = @(
"AuditLog.Read.All",
"Directory.Read.All"
)
If you are unsure how to define the permissions scope for a particular command, you can try using the Find-MgGraphCommand cmdlet. While this command may not provide all the information you need, it can still give you some helpful hints.
Step 3: Connect to Microsoft Graph API
To connect to the Microsoft Graph API run the following command:
Connect-MgGraph -Scopes $Scopes
Step 4: Retrieve Sign-In Logs
Use the following script to filter sign-in logs based on display names:
$Logs = Get-MgAuditLogSignIn -Filter "startsWith(userDisplayName,'John')"
$Logs
Use the following script to filter sign-in logs based on User Principal name:
$Logs = Get-MgAuditLogSignIn -Filter "UserPrincipalName eq 'john@contoso.com'"
$Logs
Other examples
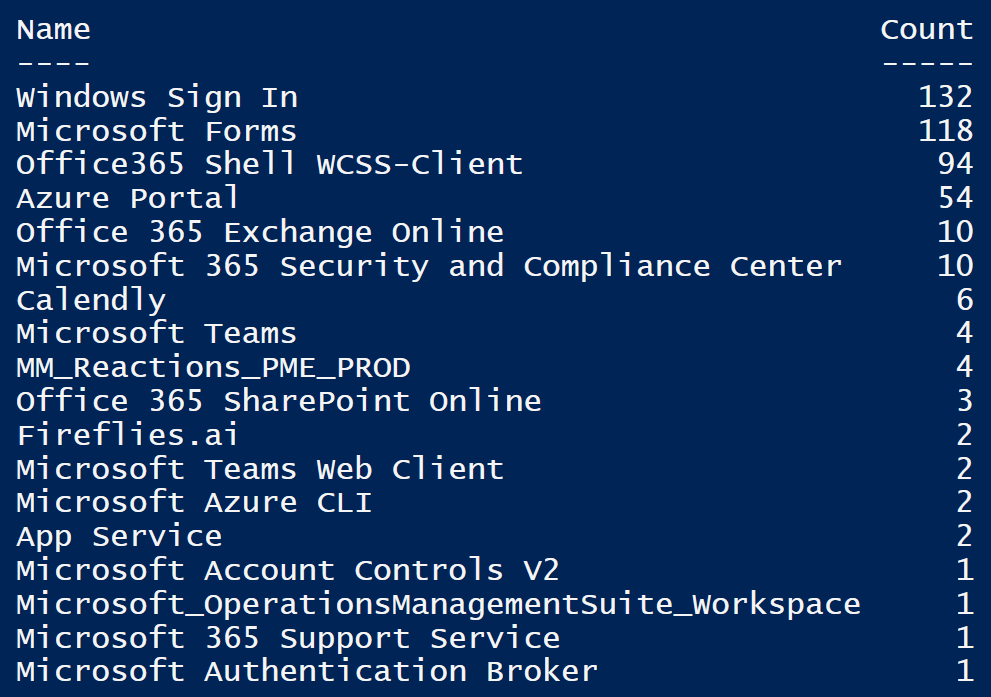
Group logs based on the AppDisplayNames:
$Logs = Get-MgAuditLogSignIn -Filter "startsWith(userDisplayName,'john')" -All
$Logs | Group-Object -Property AppDisplayName |
Select-Object -Property Name,Count |
Sort-Object -Property Count -Descending
Filter logs based on the AppDisplayName:
$Logs = Get-MgAuditLogSignIn -Filter "startsWith(userDisplayName,'john')" -All
$Logs = $Logs | Where-Object {$PSITEM.AppDisplayName -eq "Office 365 Client Admin"}
$Logs
Print out only the unique AppDisplayNames:
$Logs = Get-MgAuditLogSignIn -Filter "startsWith(userDisplayName,'john')" -All
$Logs | Select-Object -Property AppDisplayName -Unique
Sort sign-in logs based on the CreatedDateTime property and list the first ten results:
$Logs = Get-MgAuditLogSignIn -Filter "startsWith(userDisplayName,'john')" -Top 10
$Logs | Sort-Object -Property CreatedDateTime |
Select-Object -Property AppDisplayName,CreatedDateTime,UserDisplayName
Conclusion
In this blog post, I showed how to retrieve Entra ID Sign-In logs using Microsoft.Graph PowerShell Module. With these steps, you can easily monitor user authentication events and analyze them for security and troubleshooting purposes. For next steps, consider automating log analysis or integrating these logs into a centralized log management system for better visibility and monitoring.