Introduction
For organizations leveraging Azure Arc to manage their hybrid environments, securing Tier-0 assets is critical. Tier-0 assets typically include domain controllers, identity management systems, and other infrastructure that, if compromised, could cause significant harm to an organization’s IT environment. One of the ways to enhance security for these assets is to disable the Run Command feature, which could be potentially exploited if not adequately secured.
Here’s a quick guide on how to disable this feature on your Tier-0 assets.
Test Script for Run Command
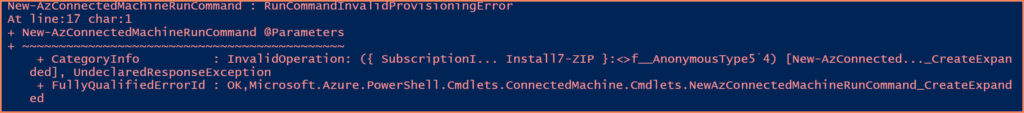
Before we disable the Run Command, let’s look at a test script that demonstrates how you could use this feature to silently install software on your servers. In this example, we’re using 7-Zip, a file archiver utility.
<#
=================================================================================
DISCLAIMER:
This script is provided "as-is" with no warranties. Usage of this script is at
your own risk. The author is not liable for any damages or losses arising from
using this script. Please review the full legal disclaimer at:
https://kaidojarvemets.com/legal-disclaimer/
=================================================================================
#>
# Define the script block
$Script =
$7ZIPURL = 'https://www.7-zip.org/a/7z2301-x64.exe'
$SourceFolder = 'C:\Windows\Temp\7z2301-x64.exe'
Invoke-WebRequest -Uri $7ZIPURL -OutFile $SourceFolder
# Execute the 7-Zip installer silently
Start-Process -FilePath 'C:\windows\Temp\7z2301-x64.exe' -ArgumentList "/S"
# Set parameters for the Run Command feature
$Parameters = @{
ResourceGroupName = "ResourceGroupName"
Location = "Location"
SourceScript = $Script
RunCommandName = "Install7-ZIP"
MachineName = "MachineName"
SubscriptionId = "SubscriptionId"
}
# Execute the Run Command
New-AzConnectedMachineRunCommand @Parameters
Disabling Run Command on Tier-0 Assets
Now, to enhance the security of your Tier-0 assets, you’ll want to block the Run Command feature to prevent its use. Here’s the simple command to disable it:
<#
=================================================================================
DISCLAIMER:
This script is provided "as-is" with no warranties. Usage of this script is at
your own risk. The author is not liable for any damages or losses arising from
using this script. Please review the full legal disclaimer at:
https://kaidojarvemets.com/legal-disclaimer/
=================================================================================
#>
azcmagent.exe config set extensions.blocklist "microsoft.cplat.core/runcommandhandlerwindows"
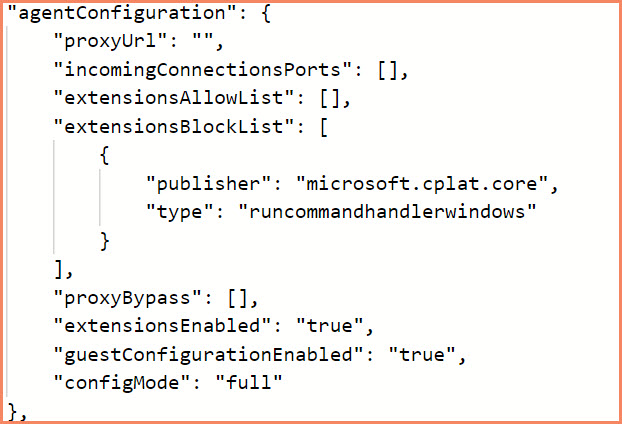
Run this command on your Azure Arc-enabled servers to add the Run Command handler to the blocklist, which will disable the feature and help to secure your Tier-0 assets.
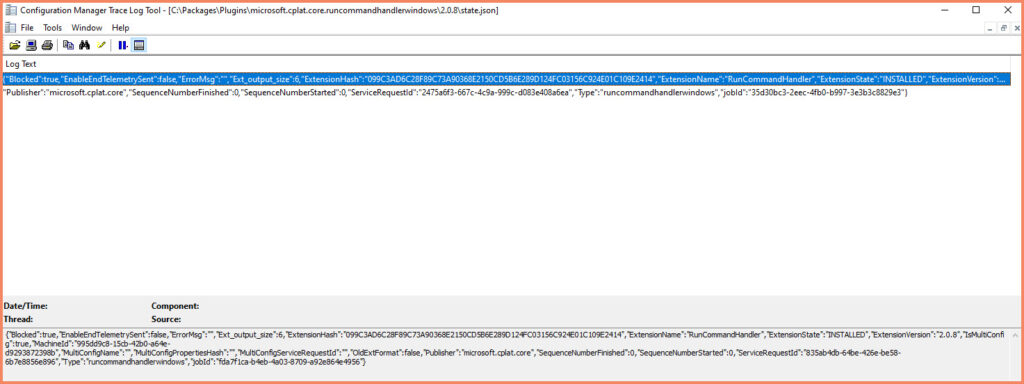
Viewing Blocked Extensions
When managing Azure Arc resources, it’s imperative to ensure that only trusted extensions are operational. Azure Arc provides a JSON view feature where you can inspect the ‘extensionsBlockList’ configuration. This section lists the extensions that are not permitted to execute, enhancing the security posture of your Tier-0 assets. It’s accessed directly within the Azure portal, providing a transparent and manageable approach to extension governance.
Conclusion
Managing your Tier-0 assets with Azure Arc provides great flexibility and control over your hybrid environments. However, it’s vital to ensure that these assets are appropriately secured. By disabling the Run Command feature, you can prevent unauthorized remote execution and maintain a robust security posture.
If you’ve found the solutions and insights shared here beneficial, please consider supporting this website and my work with a donation. Your contribution helps sustain and expand the resources available, enabling me to continue offering valuable content and tools. Thank you for your support!