Introduction
Welcome to this comprehensive guide on understanding and implementing Restricted Management Administrative Units in Entra ID. As we delve into this topic, it’s important to first understand the basics of Entra ID and the concept of Administrative Units.
Entra ID is Microsoft’s cloud-based identity and access management service. It helps organizations with a range of tasks, from managing and securing employee access to corporate resources, to facilitating collaboration with partners and customers. Entra ID is a critical component of the Microsoft 365 ecosystem and serves as the backbone of many other Microsoft services by providing a secure identity platform.
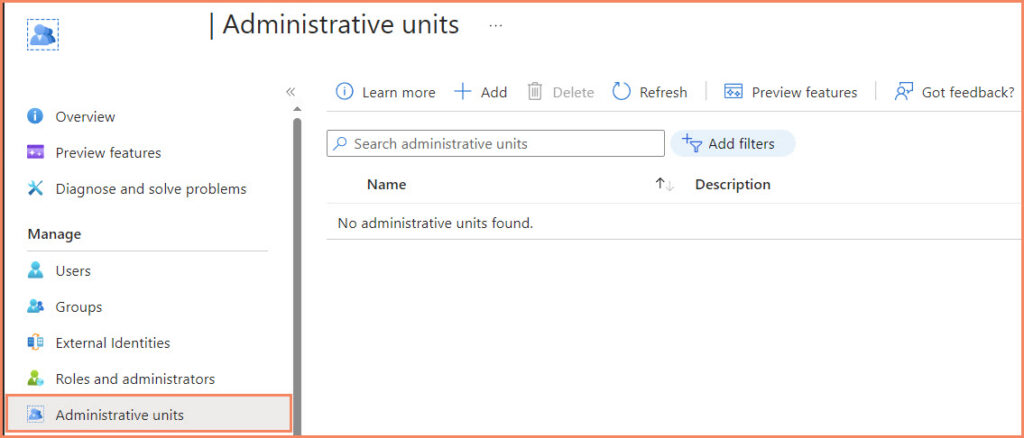
Administrative Units in Entra ID are a way to delegate administrative tasks and permissions within your organization. They act as containers for Entra ID resources, allowing you to group together users, groups, and other resources. Once these resources are part of an Administrative Unit, you can assign roles to users at the scope of that unit, effectively limiting their administrative permissions to just the resources within the unit.
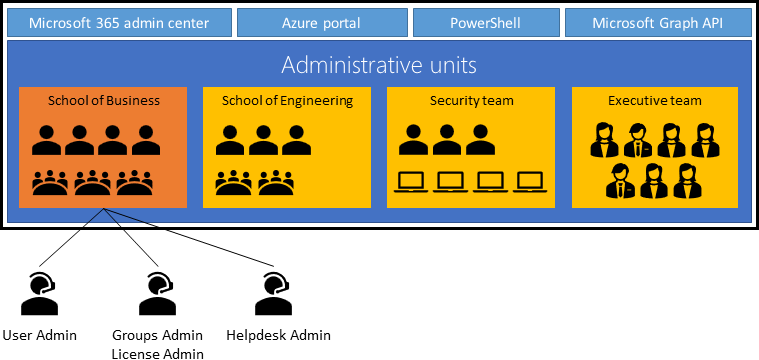
Restricted Management Administrative Units take this concept a step further. They are designed to provide an additional layer of security for privileged accounts. When an account is added to a Restricted Management Administrative Unit, only users who have been assigned a role within the scope of that unit can manage the account. This is a powerful tool for protecting privileged accounts from unauthorized changes and potential security threats.
In the following sections, we will delve deeper into the specifics of Administrative Units and Restricted Management Administrative Units, their use cases, limitations, and how to manage them effectively. Whether you’re a new Entra ID administrator or an experienced professional looking to enhance your knowledge, this guide aims to provide you with a thorough understanding of these important features.
Automation
Read more about how to automate your activities around the Administrative Units using the Microsoft Graph PowerShell Module.
- Auditing Role Assignments of Entra ID Restricted Management Administrative Units with PowerShell – Kaido Järvemets (kaidojarvemets.com)
- Automating Entra ID Administrative Units with PowerShell – Kaido Järvemets (kaidojarvemets.com)
Microsoft Sentinel
Read more about how to analyze auditing logs using Microsoft Sentinel
Understanding Administrative Units
Administrative Units are a feature of Entra ID that provide a way to delegate administrative tasks within your organization. They act as containers for Entra ID resources, allowing you to group together users, groups, and other resources. This is particularly useful for larger organizations that require a way to delegate administrative tasks to different departments or teams.
Definition and Purpose of Administrative Units
An Administrative Unit is essentially a container for Entra ID resources. It can include users, groups, and other resources that you want to manage as a single entity. The main purpose of an Administrative Unit is to delegate administrative tasks and permissions. By assigning roles to users at the scope of an Administrative Unit, you can limit their administrative permissions to just the resources within that unit.
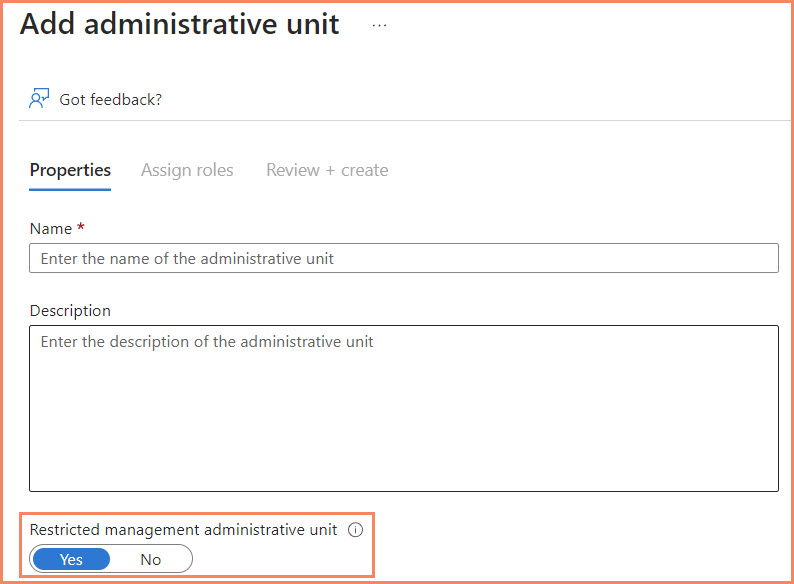
Creating and Managing Administrative Units
Creating an Administrative Unit in Entra ID is a straightforward process. Here are the general steps:
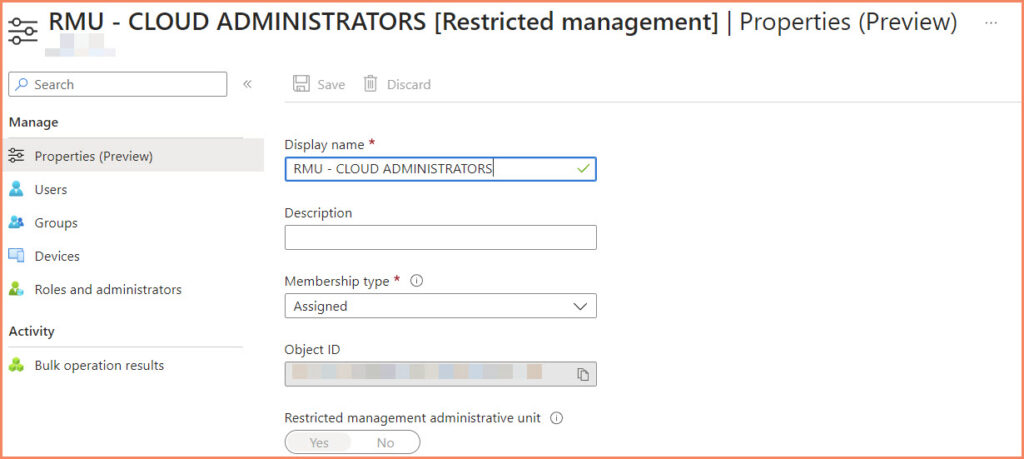
Once you’ve created an Administrative Unit, you can start adding resources to it. You can add users, groups, and devices. One important aspect of managing Administrative Units is setting the membership type. After creating an Administrative Unit, you can specify the membership type as either a dynamic user or dynamic device. This allows you to create dynamic Administrative Units that automatically include all users or devices that meet certain criteria. For example, you could set the membership type to ‘dynamic user’ and then configure the Administrative Unit to include all users in a specific department.
Managing an Administrative Unit involves assigning roles to users at the scope of the unit. This can be done by navigating to the unit in the Azure portal, clicking on “Roles and administrators“, and then clicking on the role you want to delegate and the user you want to assign it to.
Remember, the user will only have the permissions of the assigned role for the resources within the Administrative Unit. This allows you to delegate administrative tasks in a controlled and secure manner.
Understanding Restricted Management Administrative Units
As organizations grow and their Entra ID environments become more complex, the need for more granular control over administrative tasks and permissions becomes apparent. This is where Restricted Management Administrative Units come into play.
Definition and Purpose
Restricted Management Administrative Units are an enhanced version of Administrative Units in Entra ID. They are designed to provide an additional layer of security for privileged accounts by restricting who can manage these accounts.
When an account is added to a Restricted Management Administrative Unit, only users who have been assigned a role within the scope of that unit can manage the account. This means that even Global Administrators cannot manage these accounts unless they have been assigned a role within the scope of the Restricted Management Administrative Unit.
Difference Between Administrative Units and Restricted Management Administrative Units
While both Administrative Units and Restricted Management Administrative Units serve the purpose of delegating administrative tasks and permissions, there are key differences between the two.
Administrative Units act as containers for Entra ID resources, allowing you to group together users, groups, and other resources. Once these resources are part of an Administrative Unit, you can assign roles to users at the scope of that unit, effectively limiting their administrative permissions to just the resources within the unit. However, Global Administrators in your organization can still manage all resources, including those within Administrative Units, even if they haven’t been explicitly assigned a role at the scope of the unit.
On the other hand, Restricted Management Administrative Units add an extra layer of protection for privileged accounts. When an account is added to a Restricted Management Administrative Unit, only users who have been assigned a role at the scope of that unit can manage the account. This is true even for Global Administrators. If a Global Administrator hasn’t been assigned a role at the scope of the Restricted Management Administrative Unit, they won’t be able to manage the accounts within the unit.
In summary, while both types of units allow for delegation of administrative tasks, Restricted Management Administrative Units provide an additional layer of security by limiting who can manage the accounts within the unit, thereby protecting privileged accounts from unauthorized changes.
Why Use Restricted Management Administrative Units?
As organizations grow and their Entra ID environments become more complex, the need for more granular control over administrative tasks and permissions becomes apparent. This is where Restricted Management Administrative Units come into play. They provide several key benefits that make them a valuable tool for organizations of all sizes.
Protecting Privileged Accounts
One of the primary benefits of Restricted Management Administrative Units is the protection they provide for privileged accounts. Privileged accounts, such as those of Global Administrators or other high-level roles, have access to sensitive resources and operations within your Entra ID environment. If these accounts are compromised, it can lead to significant security risks.
By using Restricted Management Administrative Units, you can limit who can manage these privileged accounts. Even Global Administrators cannot manage the accounts within a Restricted Management Administrative Unit unless they have been assigned a role within the scope of that unit. This adds an extra layer of security and helps to protect your privileged accounts from unauthorized changes.
Compliance Control for Managing Resources
Restricted Management Administrative Units also provide a way to meet compliance requirements. Many organizations are subject to regulations that require them to limit access to certain resources and control who can perform administrative tasks.
With Restricted Management Administrative Units, you can easily delegate administrative tasks to specific users or groups, and limit their permissions to specific resources. This can help you to meet compliance requirements by providing a clear and auditable trail of who has access to what resources, and what they can do with those resources.
Controlling Access to Sensitive Applications
In addition to protecting privileged accounts and helping with compliance, Restricted Management Administrative Units can also be used to control access to sensitive applications. If you have applications that contain sensitive data or perform critical business functions, you can use Restricted Management Administrative Units to limit who can manage these applications.
By adding these applications to a Restricted Management Administrative Unit, you can ensure that only users who have been assigned a role within the scope of that unit can manage the application. This can help to prevent unauthorized changes to the application and protect your sensitive data.
What Can Be Managed with Restricted Management Administrative Units?
Restricted Management Administrative Units in Entra ID provide a way to delegate administrative tasks and permissions within your organization. They allow you to control who can manage certain resources and what actions they can perform. Let’s delve into the specifics of what can be managed with Restricted Management Administrative Units.
Types of Objects That Can Be Members
Restricted Management Administrative Units can contain various types of Entra ID resources. The following types of objects can be members of a Restricted Management Administrative Unit:
- Users
- Groups
- Devices
Types of Operations That Are Blocked
Certain operations are blocked within a Restricted Management Administrative Unit to ensure the security of privileged accounts. For administrators not explicitly assigned at the Restricted Management Administrative Unit scope, operations that directly modify the Entra ID properties of objects in Restricted Management Administrative Units are blocked, whereas operations on related objects in Microsoft 365 services aren’t affected.
Here’s a detailed breakdown of the types of operations that are blocked and allowed:
Operation type | Blocked | Allowed |
Read standard properties like user principal name, user photo | ||
Modify any Entra ID properties of the user, group, or device | ||
Delete the user, group, or device | ||
Update password for a user | ||
Modify owners or members of the group in the Restricted Management Administrative Unit | ||
Add users, groups, or devices in a Restricted Management Administrative Unit to groups in Entra ID | ||
Modify email & mailbox settings in Exchange for the user in the Restricted Management Administrative Unit | ||
Apply policies to a device in a Restricted Management Administrative Unit using Intune | ||
Add or remove a group as a site owner in SharePoint |
Understanding these operations and their restrictions is crucial for effectively managing resources within a Restricted Management Administrative Unit. It allows you to ensure the security of privileged accounts while still allowing certain operations to be performed on related objects in Microsoft 365 services.
Who Can Modify Objects
The ability to modify objects within a Restricted Management Administrative Unit is limited to users who have been assigned a role within the scope of that unit. This includes Global Administrators, unless they have been assigned a role within the scope of the Restricted Management Administrative Unit.
Here are the roles that can be assigned within Entra ID Administrative Unit and their respective permissions:
Role | Permissions |
Authentication Administrator | Can access to view, set and reset authentication method information for any non-admin user. |
Cloud Device Administrator | Limited access to manage devices in Entra ID. |
Groups Administrator | Members of this role can create/manage groups, create/manage groups settings like naming and expiration policies, and view groups activity and audit reports. |
Helpdesk Administrator | Can reset passwords for non-administrators and Helpdesk Administrators. |
License Administrator | Can manage product licenses on users and groups. |
Password Administrator | Can reset passwords for non-administrators and Password Administrators. |
Printer Administrator | Can manage all aspects of printers and printer connectors. |
SharePoint Administrator | Can manage all aspects of the SharePoint service. |
Teams Administrator | Can manage the Microsoft Teams service. |
Teams Devices Administrator | Can perform management related tasks on Teams certified devices. |
User Administrator | Can manage all aspects of users and groups, including resetting passwords for limited admins. |
Limitations and Constraints
While Restricted Management Administrative Units in Entra ID provide a powerful way to enhance security and compliance, they do come with certain limitations and constraints. It’s important to understand these limitations to use Restricted Management Administrative Units in your organization effectively.
Limitations of Restricted Management Administrative Units
Here are some of the key limitations of Restricted Management Administrative Units:
- Limited Object Types
- Currently, only users, groups, service principals, and managed identities can be members of a Restricted Management Administrative Unit. Other types of Entra ID resources cannot be added to a Restricted Management Administrative Unit.
- Limited Role Assignments
- Role assignments for a Restricted Management Administrative Unit can only be made to users. Groups cannot be assigned roles within a Restricted Management Administrative Unit.
- Limited Role Scope
- Roles assigned within a Restricted Management Administrative Unit only apply to the resources within that unit. They do not extend to other resources in the Entra ID organization.
Constraints for Restricted Management Administrative Units
In addition to the above limitations, there are also certain constraints when working with Restricted Management Administrative Units:
- Global Administrators: Even Global Administrators cannot manage resources within a Restricted Management Administrative Unit unless they have been assigned a role within the scope of that unit.
- Role Assignment Scope: When assigning roles, the scope of the role cannot be changed. It is automatically set to the Restricted Management Administrative Unit.
- Role Assignment Limit: Each Restricted Management Administrative Unit can have a maximum of 100 role assignments.
Entra ID Service Limits and Restrictions
Here are some of the key service limits and restrictions in Entra ID that apply specifically to Administrative Units and Restricted Management Administrative Units:
- Administrative Units: A single Entra ID tenant can have up to 500 Administrative Units. This limit includes both regular Administrative Units and Restricted Management Administrative Units.
- Role Assignments: Each Administrative Unit, including Restricted Management Administrative Units, can have up to 100 role assignments. This limit includes both active and expired assignments.
How These Limits Apply to Restricted Management Administrative Units
Restricted Management Administrative Units are subject to the same service limits and restrictions as regular Administrative Units. This means that you can have up to 500 Restricted Management Administrative Units in a single Entra ID tenant, and each of these units can have up to 100 role assignments.
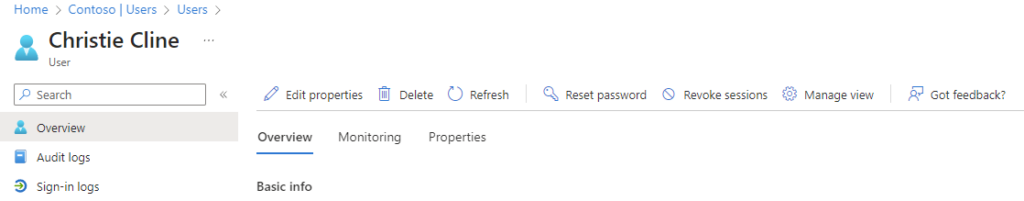
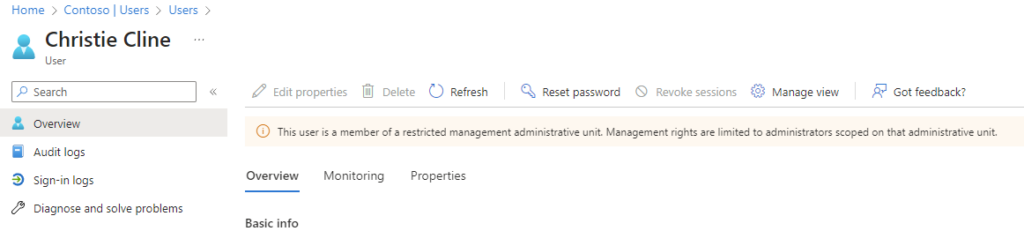
Example: Restricting Helpdesk Access to Finance Department Users
In this scenario, we have an organization with the following Entra ID configuration:
- Helpdesk Employee: Adele, who is a member of the User Administrator role at the tenant level. Her email is adelev@XXX.onmicrosoft.com.
- Finance Department Employees: Cameron and Christie, whose emails are CameronW@XXXX.OnMicrosoft.com and ChristieC@XXX.OnMicrosoft.com.
As a User Administrator at the tenant level, Adele has the ability to manage all users in the tenant. This includes the ability to reset passwords, which is a critical task for a helpdesk employee. However, this also means that Adele can manage users who are part of sensitive departments, such as Finance, which might not be desirable due to the sensitive nature of their work.
Even if the administrator adds the Finance department users to a standard Administrative Unit, Adele would still be able to reset their passwords. This is because her User Administrator role is assigned at the tenant level, which gives her permissions to manage all users in the tenant, regardless of whether they are part of an Administrative Unit or not.
To restrict Adele’s permissions so that she cannot manage the Finance department users, the organization can use a Restricted Management Administrative Unit. By adding Cameron and Christie to a Restricted Management Administrative Unit, the organization can ensure that only users who have been assigned a role within the scope of that unit can manage those users.
In this setup, Adele would not be able to manage Cameron and Christie, unless she is specifically assigned a role within the scope of the Restricted Management Administrative Unit that contains these users. This provides an additional layer of security for the Finance department users, ensuring that their accounts can only be managed by authorized personnel.
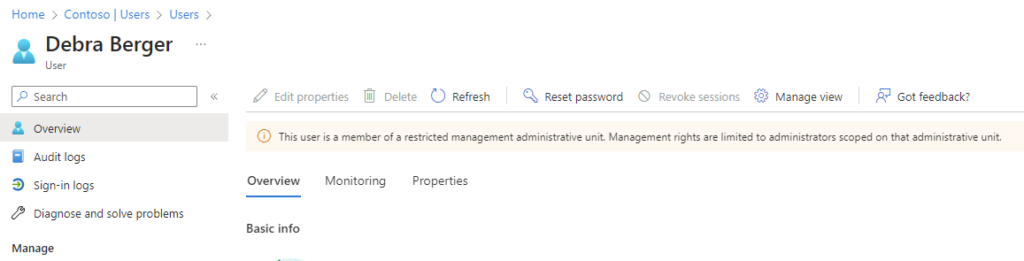
Example: Restricting Helpdesk Access to Global Administrator Accounts
In this scenario, we have an organization with the following Entra ID configuration:
- Helpdesk Employee: Adele, who is a member of the User Administrator role at the tenant level. Her email is adelev@XXXX.onmicrosoft.com.
- Global Administrator: Debra, who has permissions to request Entra ID Global Administrator permissions (Eligible assignments). She currently has no active permissions. Her email is DebraB@XXXX.OnMicrosoft.com.
As a User Administrator at the tenant level, Adele has the ability to manage all users in the tenant. This includes the ability to change user details such as department and office location, which is a common task for a helpdesk employee. However, this also means that Adele can manage the account details of Debra, who is a Global Administrator.
While this might be acceptable in some organizations, others might prefer to restrict access to Global Administrator accounts to prevent unauthorized changes. This is where Restricted Management Administrative Units can be useful.
By adding Debra to a Restricted Management Administrative Unit, the organization can ensure that only users who have been assigned a role within the scope of that unit can manage Debra’s account. In this setup, Adele would not be able to manage Debra’s account, unless she is specifically assigned a role within the scope of the Restricted Management Administrative Unit that contains Debra’s account.
This provides an additional layer of security for Global Administrator accounts, ensuring that their accounts can only be managed by authorized personnel. It also allows the organization to maintain a clear separation of duties, with helpdesk employees managing regular user accounts and specific administrators managing Global Administrator accounts.
Automation
Read more about how to automate your activities around the Administrative Units using the Microsoft Graph PowerShell Module.
- Auditing Role Assignments of Entra ID Restricted Management Administrative Units with PowerShell – Kaido Järvemets (kaidojarvemets.com)
- Automating Entra ID Administrative Units with PowerShell – Kaido Järvemets (kaidojarvemets.com)
Microsoft Sentinel
Read more about how to analyze auditing logs using Microsoft Sentinel
Conclusion
Restricted Management Administrative Units in Entra ID offer a powerful way for organizations to enhance their security posture and streamline administrative tasks. By providing a way to segregate administrative duties and restrict access to sensitive resources, they help organizations maintain a robust and secure environment.
The flexibility of these units allows for a wide range of use cases, from protecting executive accounts to managing external contractors and meeting compliance requirements. Despite certain limitations and constraints, their benefits in terms of security and control are significant.
As organizations continue to adopt cloud services and the complexity of managing identities and access increases, features like Restricted Management Administrative Units will become increasingly important. By understanding and leveraging these features, organizations can ensure they are making the most of what Entra ID has to offer.
Whether you’re a new Entra ID administrator or an experienced professional, I hope this comprehensive guide has provided valuable insights into the use of Restricted Management Administrative Units. As with any features, the key to success lies in understanding its capabilities and knowing how to apply them effectively in your unique environment.