Introduction
In my previous article about hidden Domain Admins, we explored how management tools can create shadow administrators in your on-premises environment. Today, let’s tackle an equally critical question: Who has access to your Azure resources?
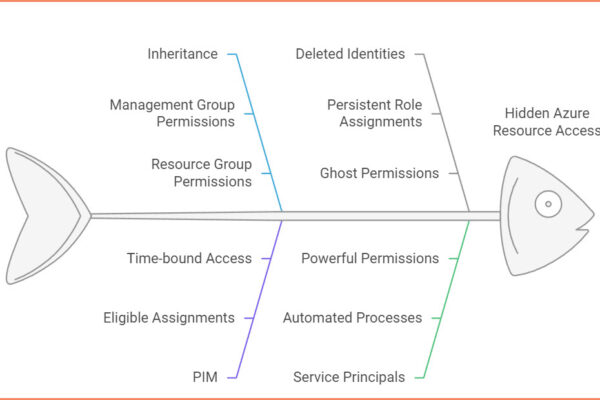
Azure’s hierarchical permission model can create a complex web of access rights that’s hard to untangle. From Management Groups down to individual resources, permissions can be inherited in ways that aren’t immediately obvious.
The Hidden Access Problem
Just like with Domain Admins, the real number of people who can access your Azure resources might surprise you.
Here’s what makes it complicated:
- Inheritance: Permissions flow down from Management Groups to Subscriptions to Resource Groups
- PIM (Privileged Identity Management): Eligible assignments that aren’t immediately visible
- Deleted Identities: Role assignments that persist even after users or service principals are removed
- Service Principals: Automated processes with powerful permissions
Introducing the Azure Resource Permissions Analyzer
To help tackle this challenge, I’ve created a PowerShell tool that provides clear visibility into your Azure resource permissions. This tool:
Important Note: This tool is designed to analyze permissions for one resource at a time. While it shows the complete permission picture for a single resource (including all inherited permissions), it’s not meant for bulk scanning of multiple resources. This focused approach allows for detailed analysis of critical resources like Arc-enabled servers, Key Vaults, or Storage Accounts.
- Shows all direct and inherited permissions for the specified resource
- Identifies PIM-eligible assignments affecting this resource
- Detects “ghost” permissions from deleted identities in the resource’s permission chain
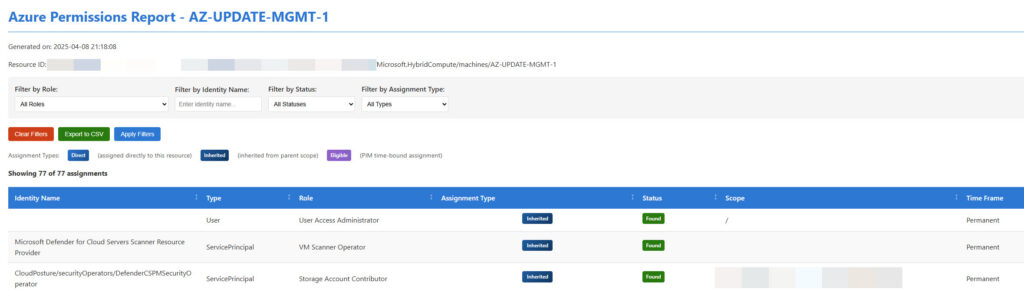
- Creates a beautiful HTML report for easy analysis of the resource’s permission structure
Key Features
- Visual permission hierarchy
- Detailed identity information
- Deleted identity detection
- Permission statistics
- Clean, modern HTML report
Understanding the Results
The tool generates a comprehensive report showing:
- Total Assignments: All permissions affecting your resource
- Direct vs Inherited: Clear separation of direct and inherited permissions
- PIM Eligibility: Time-bound privileged access
- Deleted Identities: Orphaned permissions that need cleanup
Best Practices for Azure Resource Access
- Regular Access Reviews
- Run this tool regularly
- Review inherited permissions
- Clean up deleted identity assignments
- Implement Least Privilege
- Use resource-specific roles instead of broad permissions
- Leverage PIM for just-in-time access
- Remove unnecessary inherited permissions
- Monitor and Alert
- Track permission changes
- Alert on high-privilege assignments
- Regular compliance checks
The Real Impact
Just like with Domain Admins, the impact of overlooked permissions can be severe:
- Data breaches through forgotten access paths
- Compliance violations from unauthorized access
- Security incidents from compromised accounts
Action Steps
- Download and run the tool on your critical resources
- Review the HTML report for unexpected access
- Clean up identified deleted identities
- Implement regular permission audits
- Consider PIM for privileged access
Conclusion
Understanding who has access to your Azure resources is critical for maintaining a secure environment. Don’t wait for an incident to realize you’ve given away more access than you thought.
As a Microsoft MVP focusing on Azure security, I’ve seen firsthand how hidden permissions can create security gaps in enterprise environments. The updated version of this tool now features improved reporting with automatic filtering, making permission analysis even faster. Premium members can access this script at docs.kaidojarvemets.com along with detailed documentation on how to use it effectively.
Not a Premium Member yet? Get access to this script and other time-saving security automation tools that will save you hours of manual permission analysis.