Introduction
Ensuring seamless integration and alignment between Microsoft Sentinel’s Analytics Rules and Data Collection Rules (DCR) is paramount for effective threat detection and response. However, a recurring challenge many organizations face is verifying that the Event IDs in their Analytics Rules are indeed covered by their DCRs. This alignment is crucial because any discrepancy can lead to missed detections or incomplete data collection, potentially affecting the overall efficacy of the SIEM setup.
This solution, developed over two days, streamlines your auditing process, potentially saving you between €2,400 and €8,800 in development costs alone. Dive into the technical details below, and find a complete breakdown of the value proposition at the end of this post.
Kaido Järvemets
In this guide, we’ll explore a PowerShell-based approach to audit and verify the alignment between Analytics Rules and DCRs, ensuring that your configurations are optimized for maximum coverage and efficiency.
Get-KJSentinelAnalyticsRulesEventIDs Function
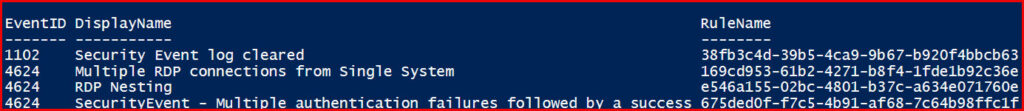
The Get-KJSentinelAnalyticsRulesEventIDs function is designed to extract EventIDs from Microsoft Sentinel’s Analytics Rules. By providing the necessary Azure Log Analytics Workspace details, this function fetches all the Analytics Rules and then filters out the relevant Event IDs.
Function Code
This section is reserved for our Premium Members only. Upgrade your membership to access this valuable content and unlock more benefits.
Usage
$ExtractedAnalyticsRulesInfo = Get-KJSentinelAnalyticsRulesEventIDs -ResourceGroupName "YOUR_RESOURCE_GROUP" -SentinelWorkspaceName "YOUR_WORKSPACE"
Output
Get-KJSentinelDataCollectionRules Function
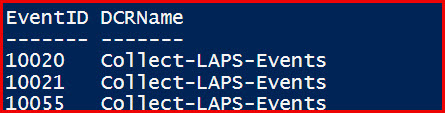
The Get-KJSentinelDataCollectionRules function is tailored to extract Event IDs from Microsoft Sentinel’s Data Collection Rules (DCR). This function goes through all the Data Collection Rules and extracts the relevant Event IDs, ensuring you have a comprehensive list of Event IDs that your Sentinel environment collects.
Function Code
This section is reserved for our Premium Members only. Upgrade your membership to access this valuable content and unlock more benefits.
Usage
$ExtractedDCREventIDs = Get-KJSentinelDataCollectionRules
This section is reserved for our Premium Members only. Upgrade your membership to access this valuable content and unlock more benefits.
Usage
Get-KJSentinelSecurityAnalyticsRules -ResourceGroupName "YOUR_RESOURCE_GROUP_NAME" -SentinelWorkspaceName "YOUR_WORKSPACE_NAME"
Compare-KJSentinelAnalyticsRulesData Function
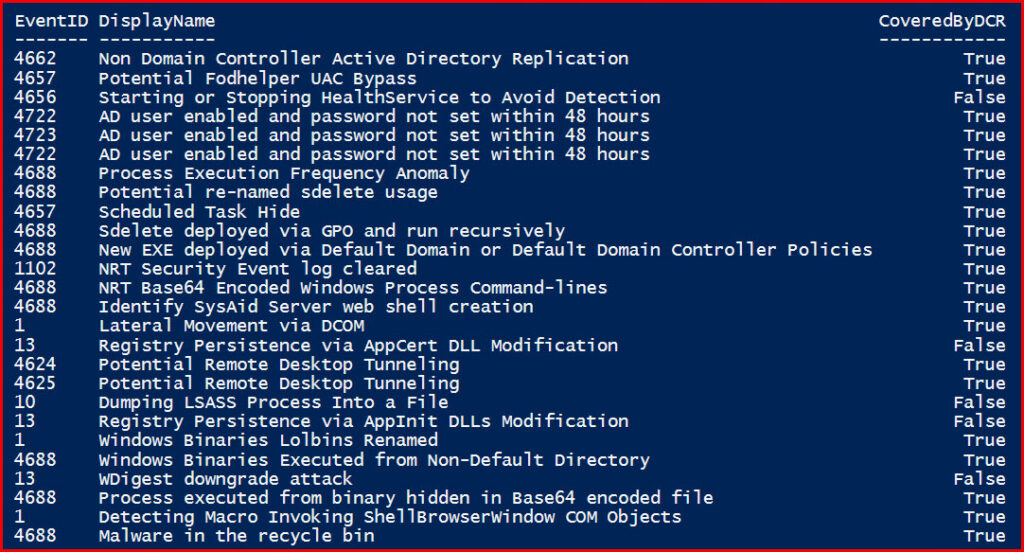
The Compare-KJSentinelAnalyticsRulesData function serves as the heart of our auditing process. Its primary role is to compare the Event IDs extracted from the Analytics Rules against those from the Data Collection Rules. This comparison ensures that our Data Collection Rules are indeed collecting all events we’re monitoring with our Analytics Rules.
Function Code
This section is reserved for our Premium Members only. Upgrade your membership to access this valuable content and unlock more benefits.
Usage
Compare-KJSentinelAnalyticsRulesData -ExtractedDCREventIDsInfoObject $ExtractedDCREventIDs -ExtractedAnalyticsRulesInfoObject $ExtractedAnalyticsRulesInfo
Output
Solution Download (Premium Members)
Value Delivered
The utility of this solution extends beyond its immediate function. It represents a significant investment of expertise and effort aimed at streamlining the auditing process of Microsoft Sentinel analytics rules. Here’s a breakdown of the value delivered
Development Effort
Time Invested: Two full working days (approximately 16 hours) were dedicated to the development, testing, and documentation of this script.
Cost-Benefit Analysis
Monetary Value: The professional hourly rate for developing such scripts ranges between €150 and €550. Therefore, replicating such a script from scratch could cost between €2,400 and €8,800 (€150/€550 * 16 hours).
Operational Efficiency: Automating the auditing process can save substantial time and effort, especially in larger or more complex environments. The exact time and cost savings will depend on the specifics of your operation, but the potential for enhanced operational efficiency is significant.
By leveraging this script, you are not only saving valuable development time but also gaining a tool that has been crafted with expertise to ensure reliability and effectiveness in auditing your Microsoft Sentinel analytics rules.
Conclusion
Auditing is essential to maintaining a robust and secure Microsoft Sentinel setup. As we’ve explored throughout this post, ensuring that our Analytics Rules align with our Data Collection Rules is critical. Any misalignment or oversight can lead to potential security blind spots, making our infrastructure vulnerable to threats we believe we’re monitoring.
For those who recognize the importance of a well-audited and optimized Sentinel setup but might need assistance or guidance, I offer specialized services tailored to Microsoft Sentinel. Whether you’re just starting out or looking to refine your existing setup, I’m here to help. Explore my Microsoft Sentinel services to see how we can work together to enhance your security posture.
Let’s ensure that our security infrastructure is not just operational, but optimal.