Introduction
If your organization is currently using Azure Update Management, Microsoft offers a streamlined way to deploy Azure Arc agents through your existing Update Management infrastructure. This method leverages your current setup to simplify the Arc agent deployment process.
Current State of Azure Update Management
Azure Update Management has been replaced by Azure Update Manager, which offers enhanced capabilities including zero-touch onboarding, Azure Policy integration, and improved update management through Azure Resource Manager. While Update Manager is now the recommended solution for new deployments, existing Update Management customers can still use their infrastructure to deploy Arc agents.
Deployment Methods for Azure Arc
There are several ways to deploy the Azure Arc agent:
- Manual installation
- Service principal for large-scale deployments
- Azure Update Management (for existing Update Management customers)
- Az.ConnectedMachine PowerShell module
- Desired State Configuration
- Script feature in Configuration Manager
- Group Policy
- Windows Admin Center
- Custom Task Sequence in Configuration Manager
If you’re already using Update Management, deploying Arc agents through this existing infrastructure can be the most straightforward option. The rest of this post will guide you through this process.
What is Azure Automation Update Management?
Azure Update Management is a cloud-based service that manages and deploys updates for Windows and Linux computers. It helps reduce the time and effort needed to keep systems up-to-date with the latest security patches, hotfixes, service packs, and more.
Update Management integrates with Azure Log Analytics, storing all data in the same Workspace. This makes it easier to create Workbooks, Alerts, and Automation. For organizations already using Update Management, this integration provides an efficient path to deploy Azure Arc-enabled servers agents.
If you’re an experienced Update Management administrator, you’ll be familiar with the Patch-MicrosoftOMSComputers runbook used for patching. Similarly, for Arc deployment, Microsoft provides a master runbook called Add-AzureConnectedMachines that runs directly on your servers under the system runbook hybrid worker.
Requirements
To deploy Azure Arc agent through Update Management, you need:
- Azure Log Analytics Workspace
- Microsoft Monitoring Agent installed and configured on your servers
- Azure Automation Account
- Azure Update Management solution activated
- Automation Job Operator role permissions
- Permissions to create Service Principals
- Permissions to manage Resource Group / Subscription
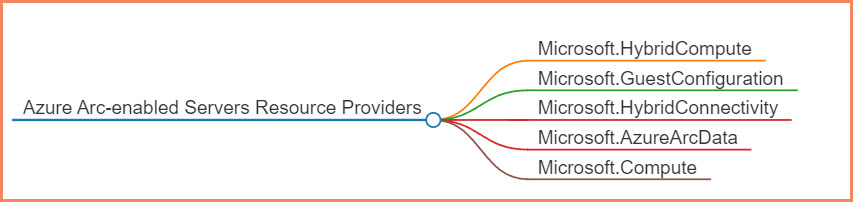
- Azure resource providers for Azure Arc enabled-servers
Resource Planning
Before deploying Azure Arc, take time to plan your resource groups. You can onboard all servers into a single resource group or split them into multiple ones based on administration model, location, services, etc. Azure Arc fully supports moving resources between resource groups.
Resource Providers
Azure Private Link and Azure Arc
Azure Private Link offers a robust solution for securely connecting servers to Azure Arc, eliminating the need to use public networks. This method significantly enhances security by allowing private connections directly to Azure Arc, ensuring that data from Azure Arc-enabled machines or servers is accessed only through authorized private networks. By utilizing Azure Private Link, all traffic is kept within the Microsoft Azure backbone network.
Azure Arc Agent Deployment Through Update Management
The deployment process automatically:
- Creates an Entra ID Service Principal for authentication and onboarding
- Installs the Connected Machine Agent
- Onboards the server to Azure Arc service
Deployment Steps
- Open Azure Portal (portal.azure.com) and search for Azure Arc
- On the Azure Arc panel, choose “Add Resources“
- On the Azure Arc resources panel, choose “Add a Machine“
- On the Add servers with Azure Arc panel, select “Add servers from Update Management”
- Specify the following information:
- Subscription
- Resource Group
- Region
- Authentication
- Connectivity Method (Public endpoint, Proxy Server, Private Endpoint)
- Click “+Add Servers” and choose the servers to add
- Choose “Create a new service principal” or use existing one
- Specify Tags
- Review deployment information and click Add
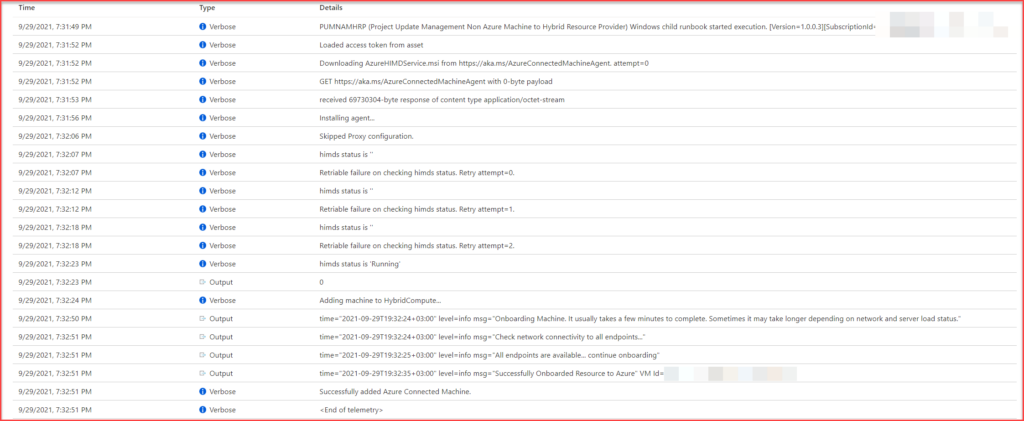
These steps initiate the Add-AzureConnectedMachines runbook. For Windows servers, it executes Add-AzureConnectedMachineWindows, and for Linux servers, Add-AzureConnectedMachineLinux. Both runbooks execute under the system Hybrid Runbook Worker.
Conclusion
For organizations already using Azure Update Management, deploying Azure Arc agents through this existing infrastructure provides a streamlined and efficient approach. The process leverages your current Update Management setup, making it a practical choice for Arc adoption. While Azure Update Management is being replaced by Azure Update Manager for update management tasks, this deployment method remains available for existing customers.
Key benefits of this deployment approach include:
- Automated service principal creation and configuration
- Simplified agent deployment using existing infrastructure
- Support for both Windows and Linux environments
- Flexible connectivity options including private networking
- Integration with existing security and management practices
As you plan your Azure Arc deployment, consider your resource organization strategy and security requirements. Whether you choose to deploy through Update Management or another method, ensure your approach aligns with your organization’s operational needs and security policies.