Introduction
Azure Arc is a service from Microsoft designed to help you manage and monitor your on-premises and hybrid servers using the same methodologies and tools available for Azure resources. Through Azure Arc, you can manage servers via Azure Resource Manager templates, enforce policies and compliance standards, and utilize Azure Monitor and Azure Log Analytics for troubleshooting and monitoring.
Azure Arc is increasingly favored by organizations seeking a unified and centralized management solution for their on-premises and hybrid servers while leveraging Azure’s advanced features and capabilities. A notable advantage of Azure Arc is the ability to employ Azure VM extensions on your infrastructure, enhancing server functionality and automating routine tasks.
I have detailed the usage of Azure Arc in deploying the Custom Script Extension for Windows across Arc-connected nodes in recent blog posts. This extension supports the execution of PowerShell or Bash scripts on your Azure VMs, facilitating tasks such as software installation, settings configuration, and updates application.
For comprehensive guidance, please refer to my step-by-step blog posts:
It’s important to note that executing PowerShell scripts from various sources introduces security risks, as malicious actors could exploit this functionality. Many organizations now utilize Microsoft Sentinel for integrated SIEM and SOAR capabilities. If you haven’t explored this, I strongly advise you to consider its implementation.
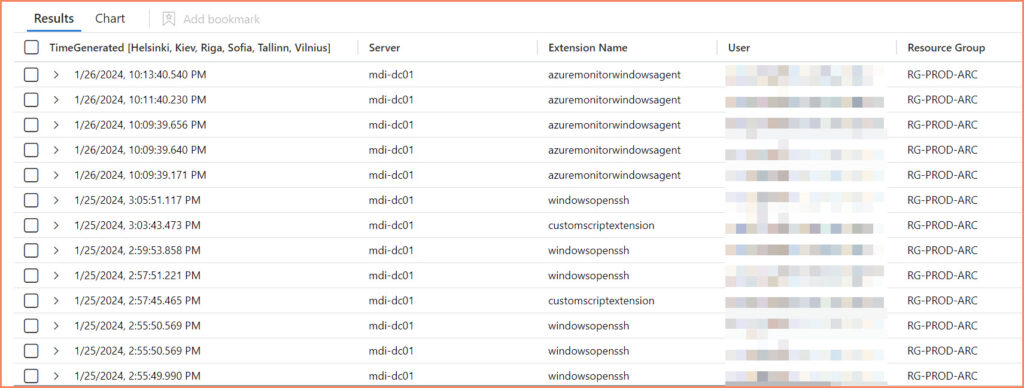
For those interested in gaining insights into extension installations and other activities, I’ve developed the following KQL query. This query can be applied in Workbooks or used to enhance your detection strategies.
AzureActivity | where OperationNameValue == "MICROSOFT.HYBRIDCOMPUTE/MACHINES/EXTENSIONS/WRITE" and ResourceProviderValue == "MICROSOFT.HYBRIDCOMPUTE"
| extend Properties = (parse_json(Properties))
| extend Server = split(Properties.resource,"/")[0]
| extend ["Extension Name"] = split(Properties.resource,"/")[1]
| extend User = Properties.caller
| extend ["Resource Group"] = Properties.resourceGroup
| extend ["Susbcription ID"] = Properties.SubscriptionId
| extend ["IP Address"] = CallerIpAddress
| extend ["Activity Status"] = Properties.activityStatusValue
| project TimeGenerated,Server, ['Extension Name'], User, ['Resource Group'], ['Susbcription ID'], ['IP Address'],["Activity Status"]
| sort by TimeGenerated