Introduction
Monitoring Data Collection Rules (DCRs) in Azure significantly influences the operation of Microsoft Sentinel, Microsoft’s cloud-native SIEM system. While commonly associated with Azure-based resources, DCRs are critical for managing data across various environments, including on-premises data centers and other cloud platforms. This expanded capability enables Sentinel to gather and analyze data from a diverse array of sources, ensuring robust security management across an organization’s entire digital landscape, not just within Azure. By integrating data from both Azure and non-Azure environments, Sentinel can provide a more unified security posture, critical for detecting and responding to threats wherever they may occur.
Here’s why this monitoring is critical:
- Security Threats: If an adversary manages to delete or alter DCRs, they can effectively blind Sentinel, preventing it from detecting malicious activities or breaches. This leaves the environment vulnerable to further undetected attacks.
- Data Availability: The association or linkage of DCRs to specific resources is pivotal. If these associations are removed—whether through configuration errors or malicious intent—the logs vital for monitoring and alerting will cease to flow into Sentinel, again creating a blind spot.
- Integrated Defense Systems: Many Azure services, such as Defender for SQL rely on DCRs for their security operations. If a DCR is compromised, it could disrupt the threat detection capabilities of these services, potentially leading to unmitigated risks in SQL database environments.
- Cost Management: Unmonitored changes to DCRs can lead to unexpected costs due to either excessive data logging from misconfigurations or inadequate logging leading to missed opportunities for optimization.
- Governance and Compliance: Regular monitoring helps ensure that changes to DCRs comply with organizational policies and regulatory requirements, maintaining a strong governance posture within Azure.
By integrating Azure Log Analytics and the Azure Resource Graph with Sentinel, organizations can enhance their monitoring strategies, enabling a more robust defense mechanism against threats and ensuring that governance and compliance standards are consistently met. This integration not only simplifies the management of DCRs but also empowers organizations to maintain a secure and compliant Azure environment.
Integration of Azure Log Analytics and Resource Graph
The integration of Azure Log Analytics with the Azure Resource Graph through the arg(“”) data connector is a strategic enhancement for Microsoft Sentinel. This data connector allows users to execute queries against Azure Resource Graph data directly within Azure Log Analytics workspaces. This capability is particularly important because not all relevant data is available in the AzureActivity table.
The AzureActivity table captures a range of telemetry about operations on Azure resources, but it doesn’t encompass all the metadata and configurations stored across various Azure services. For comprehensive security monitoring and to create enriched reports, additional data must be pulled from the Azure Resource Graph. This graph maintains extensive details about Azure resources, including those not logged by standard telemetry or operational logs.
By using the arg(“”) data connector, administrators and security analysts can perform complex joins and queries that merge data from these disparate sources. This approach enhances Microsoft Sentinel’s monitoring capabilities by providing a more holistic view of the environment. Analysts can use this integrated data to detect anomalies, review configurations, and ensure compliance with security policies more effectively.
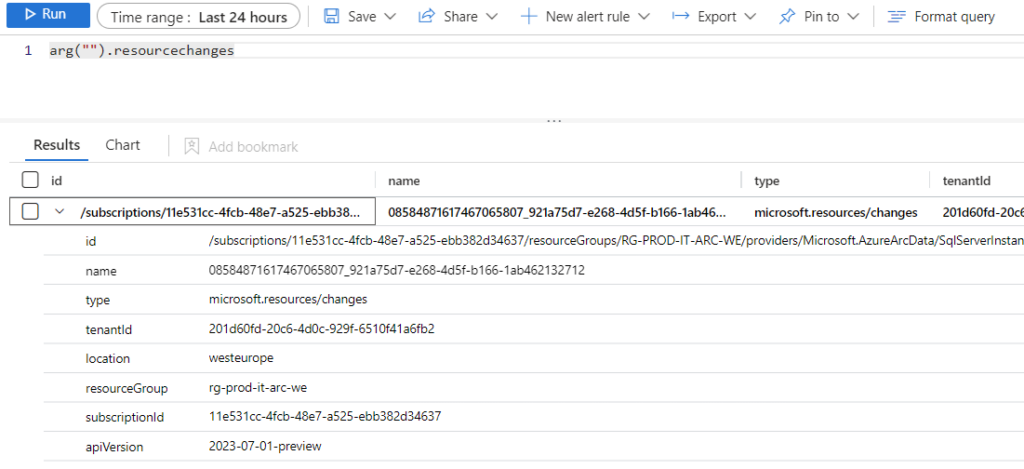
The resourcechanges Table in Azure Resource Graph
The resourcechanges table in the Azure Resource Graph provides detailed insights into the changes made to Azure resources. This capability is important for tracking configuration changes and ensuring compliance with governance policies. By accessing this table, users can view historical changes, compare different states of a resource, and understand the context and impact of each modification.
How resourcechanges Works
The resourcechanges table records each change made to Azure resources, detailing what was changed, by whom, and when. This includes changes to configurations, relationships, and properties of Azure resources. Each record in the table captures:
- The type of resource affected.
- The operation that triggered the change (e.g., update, delete).
- Metadata about the change, such as the initiator and timestamp.
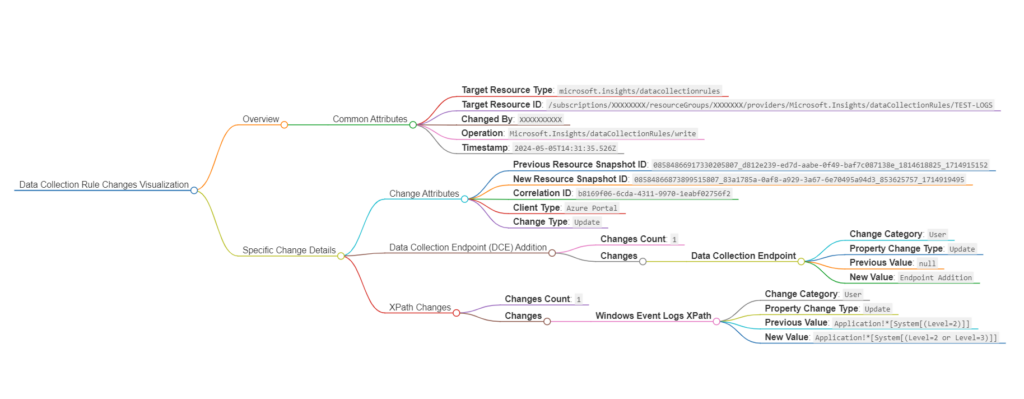
Example Use Cases: DCR Changes in XPath and DCE
For instance, monitoring changes in Data Collection Rules (DCRs), specifically looking at modifications to XPath queries and Data Collection Endpoint (DCE) configurations, helps maintain effective data collection strategies. Here are two simplified examples showing how DCRs might change:
- XPath Query Update: An XPath query within a DCR is updated to include both levels 2 and 3 logs. This change expands the scope of data collection, potentially increasing the volume and detail of logs collected.
- Data Collection Endpoint Insertion: A new data collection endpoint is added to a DCR.
Querying Changes with resourcechanges
To track and analyze these changes, you can use a simple query based on the CorrelationId, which links changes recorded in the resourcechanges table with activities logged in the AzureActivity table. Here’s how you might structure such a query to fetch changes related to a specific CorrelationId:
This section is reserved for our Premium Members only. Upgrade your membership to access this valuable content and unlock more benefits.
KQL Queries for Data Collection Rules
The provided KQL (Kusto Query Language) queries are designed to monitor various activities related to Data Collection Rules (DCRs) in Microsoft Sentinel. These activities include creating new rules, associating or disassociating them with resources, and joining this data with changes logged via the Azure Resource Graph.
Monitoring New DCR Creation
This query monitors the creation of new DCRs, checking for successful write operations
This section is reserved for our Premium Members only. Upgrade your membership to access this valuable content and unlock more benefits.
DCR Associations – Add and Remove
These queries monitor when DCRs are associated with or disassociated from resources:
This section is reserved for our Premium Members only. Upgrade your membership to access this valuable content and unlock more benefits.
This section is reserved for our Premium Members only. Upgrade your membership to access this valuable content and unlock more benefits.
Combining DCR Write Events with Resource Changes
This query combines DCR write events from the AzureActivity table with resource change events from the Azure Resource Graph, using CorrelationId to link related entries:
This section is reserved for our Premium Members only. Upgrade your membership to access this valuable content and unlock more benefits.
Conclusion
The integration of Azure Log Analytics, the Azure Resource Graph, and Microsoft Sentinel forms a robust framework for security management within Azure and hybrid-cloud environments. This comprehensive setup not only simplifies the monitoring of Data Collection Rules (DCRs) but also enhances the ability to visualize and analyze data across various platforms.
By leveraging the resourcechanges table, organizations can gain deep insights into the historical changes made to their Azure resources, helping them to maintain operational integrity, ensure compliance with governance policies, and respond proactively to security threats. The ability to query and analyze these changes in detail supports a stronger security posture by enabling more informed decision-making and more precise incident response strategies.
Furthermore, tools like Markmap offer innovative ways to visualize complex datasets, making it easier for teams to understand the impact of changes and communicate this information effectively across the organization.
In sum, as cloud environments become increasingly complex and integrated with on-premises and other cloud infrastructures, the need for sophisticated monitoring tools becomes more apparent. Microsoft Sentinel, with its powerful integrations and capabilities, stands out as an essential component of modern cloud security strategies, ensuring that organizations can guard against threats and manage their cloud resources effectively.