The Danger of Assumptions in IT Management
Picture this: You’ve been using Group Policies to manage your workstations for years. Everything seems fine on the surface. But is it really? How do you know if your policies are actually applied correctly? Are they conflicting with local settings? Are there systems that somehow slipped through the cracks?
These aren’t just hypothetical questions. In the world of IT management, assumptions can be dangerous. You might think your environment is secure and well-managed, but without proper verification, you’re essentially flying blind.
Even if you’ve implemented Configuration Manager (ConfigMgr), are you using it to its full potential? Many organizations have ConfigMgr in place, but aren’t leveraging its powerful capabilities for system insights and management.
It’s time to stop assuming and start knowing. It’s time to harness the full power of Configuration Manager baselines and configuration items to truly understand and control your IT environment.
The Reality Check: Why We Need to Verify
Let’s face it: IT environments are complex beasts. Group Policies, local settings, user modifications, and various management tools all interact in ways that can be hard to predict. Without a systematic way to check and verify settings, you might be in for some unpleasant surprises.
Consider these scenarios:
- You think all your systems have the latest security patches, but do they really?
- You’ve set a policy to disable PowerShell v2, but is it actually removed from all machines?
- You believe your systems are encrypted with BitLocker, but are they, and what’s the key length?
These are the kinds of questions that keep IT professionals up at night. But they don’t have to.
Enter Configuration Manager: Your Window into Reality
This is where Configuration Manager shines. With ConfigMgr baselines and configuration items, you can:
- Actively check the actual state of your systems
- Compare that state against your desired configuration
- Get detailed reports on compliance and discrepancies
- Automatically remediate issues when possible
It’s not about assuming your policies are working. It’s about knowing they are, and having the data to prove it.
In the following sections, we’ll dive into specific examples of how you can use ConfigMgr to gain real, actionable insights into your IT environment. We’ll look at practical scripts you can use to check everything from installed features to registry settings.
Remember, in IT management, knowledge truly is power. And with Configuration Manager, that knowledge is at your fingertips.
Putting Configuration Manager to Work
Let’s look at some practical examples of how you can use Configuration Manager to gain real insights into your environment. These scripts can be used to create configuration items in ConfigMgr, allowing you to consistently check and report on your systems status.
Example 1: Verifying PowerShell v2 Removal
PowerShell v2 is outdated and can pose security risks. But how do you know it’s actually removed from all your systems? Here’s a script to check:
<#
=================================================================================
DISCLAIMER:
This script is provided "as-is" with no warranties. Usage of this script is at
your own risk. The author is not liable for any damages or losses arising from
using this script. Please review the full legal disclaimer at:
https://kaidojarvemets.com/legal-disclaimer/
=================================================================================
#>
#DISCOVERY SCRIPT
$Roll = Get-WindowsFeature -Name "PowerShell-V2" | Select-Object -ExpandProperty InstallState
if($Roll -eq "Installed"){
Write-Host "NOTOK"
}
Else{
Write-Host "OK"
}
#REMEDIATION SCRIPT (OPTIONAL)
Remove-WindowsFeature -Name "PowerShell-V2"
This script not only checks if PowerShell v2 is installed but also provides a remediation step to remove it if found. By implementing this as a configuration item in CM, you can:
- Get a clear view of which systems still have PowerShell v2 installed
- Automatically remove it from non-compliant systems
- Track your progress in eliminating this potential vulnerability across your environment
Example 2: Monitoring Recent Hotfixes
Ensuring systems are up-to-date with the latest hotfixes is crucial for security. But how do you know if systems are being updated regularly? This script checks for recent hotfix installations:
# Get the current date
$CurrentDate = Get-Date
# Define the date 30 days ago
$CutoffDate = $currentDate.AddDays(-30)
# Get a list of all installed hotfixes
$Hotfixes = Get-Hotfix
# Check if any hotfixes have been installed in the last 30 days
$RecentHotfixes = $Hotfixes | Where-Object {
$_.InstalledOn -ge $CutoffDate
}
If ($RecentHotfixes) {
Write-Output "OK"
} else {
Write-Output "NOTOK"
}
By implementing this as a configuration item, you can:
- Identify systems that haven’t received updates in the past 30 days
- Prioritize systems for manual investigation or forced updates
- Track update compliance across your entire environment
Example 3: Verifying Windows Update Server Configuration
Ensuring systems are updating from the correct source is critical for maintaining security and consistency. This script checks the Windows Update server configuration:
# Define the registry path and the key to check
$RegistryPath = "HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate"
$RegistryKey = "WUServer"
$ExpectedValue = "http://CM01.CONTOSO.COM:8530"
# Check if the registry key exists
If(Test-Path $RegistryPath) {
# Get the value of the registry key
$ActualValue = Get-ItemProperty -Path $RegistryPath -Name $RegistryKey | Select-Object -ExpandProperty $RegistryKey
# Compare the actual value with the expected value
If ($ActualValue -eq $ExpectedValue) {
Write-Output "OK"
} Else {
Write-Output "NOTOK"
}
} Else {
Write-Output "NOTOK"
}
Implementing this as a configuration item allows you to:
- Identify systems that are not correctly configured for your update server
- Ensure all systems are receiving updates from the approved source
- Quickly spot and correct any misconfigurations
Example 4: Checking Windows Defender Status on Servers
For Windows Server 2019 and 2022, it’s important to ensure Windows Defender is active. Here’s a script to verify this:
#Check Windows Server 2019 and 2022 Windows Defender Feature
$DefenderAVRole = Get-WindowsFeature -Name "Windows-Defender"
If($DefenderAVRole.InstallState -eq "Installed"){
Write-Host -Object "OK"
}
Else{
Write-Host -Object "NOTOK"
}
Using this as a configuration item enables you to:
- Confirm Windows Defender is installed on all applicable servers
- Identify any servers where Windows Defender is missing or disabled
- Maintain a consistent security posture across your server environment
The Power of Configuration Manager Reporting and Automation
While these individual checks are powerful, the real magic happens when you combine them into comprehensive reports and automated processes. Configuration Manager isn’t just a monitoring tool – it’s a powerhouse of automation and integration possibilities.
Harnessing 1000+ Built-in Cmdlets
Configuration Manager comes with a staggering 1,176 built-in PowerShell cmdlets. Yes, you read that right – over a thousand cmdlets at your fingertips! This extensive library gives you unprecedented control and flexibility in managing your environment.
With these cmdlets, you can:
- Build custom automation processes
- Create detailed, tailored reports
- Integrate CM data with other systems (like JIRA for ticketing)
- Perform bulk operations across your entire infrastructure
- Automate repetitive tasks and free up your time for strategic work
The possibilities are virtually limitless. Whether you’re looking to streamline your workflow, enhance your reporting, or create complex management scripts, these cmdlets provide the building blocks you need.
From Data to Action: Reporting and Beyond
Configuration Manager allows you to aggregate data from all your configuration items, giving you a bird’s-eye view of your entire environment. But it doesn’t stop at just collecting data – you can use this data to drive real action in your organization.
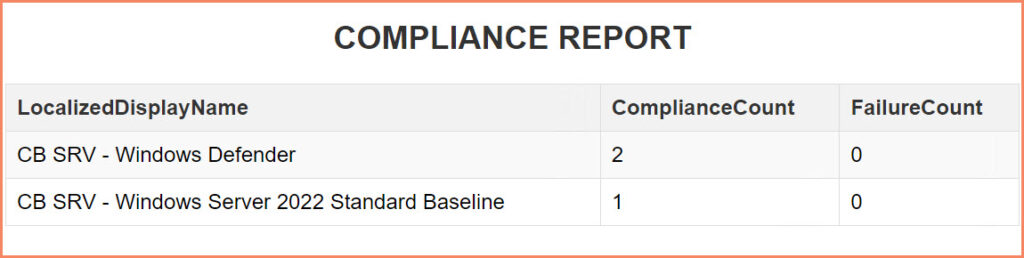
Here’s a simple script to generate an HTML report of your baseline compliances:
$css = @"
<style>
body { font-family: Arial, sans-serif; }
h2 { color: #333; text-align: center; }
table { width: 100%; border-collapse: collapse; margin: 20px 0; }
table, th, td { border: 1px solid #ddd; }
th, td { padding: 8px; text-align: left; }
th { background-color: #f2f2f2; color: #333; }
tr:nth-child(even) { background-color: #f9f9f9; }
tr:hover { background-color: #f1f1f1; }
.container { width: 80%; margin: auto; }
</style>
"@
$Info = Get-CMBaseline -Name "*CB SRV -*" -Fast | Select-Object -Property LocalizedDisplayName,ComplianceCount,FailureCount
$Info | ConvertTo-Html -Head "<h2>COMPLIANCE REPORT</h2>$css" | Out-File C:\Temp\ComplianceReport.html
- Automatically create JIRA tickets for non-compliant systems
- Send daily compliance summaries to team leads via email / Microsoft Teams
- Trigger remediation scripts based on compliance status
- Export data to third-party visualization tools for executive dashboards
- Integrate with your ITSM tool to update configuration items automatically
The key is to think beyond just monitoring and reporting. Use Configuration Manager as the central nervous system of your IT operations, driving processes, decisions, and actions across your entire infrastructure.
Remember, with great power comes great responsibility (and great opportunity). Start small, experiment, and gradually build more complex automations as you become comfortable with the tools at your disposal. Before you know it, you’ll have transformed your IT operations from reactive to proactive, from guesswork to certainty.
Conclusion: From Assumption to Knowledge – Your Journey Begins Here
By implementing these configuration items and leveraging Configuration Manager’s reporting capabilities, you’re moving from a world of assumptions to one of concrete knowledge. You’re not just hoping your systems are configured correctly – you’re verifying it, consistently and automatically.
It’s important to note that the examples we’ve discussed here are just the tip of the iceberg. Configuration Manager baselines are incredibly versatile, and there are many other excellent examples available online. I strongly encourage you to do your own research and explore the wealth of baselines that others in the IT community have developed. You might find pre-made solutions for challenges you’re facing or inspiration for creating your own custom baselines.
For those new to Configuration Manager or hesitant about making automated changes, remember that remediation through baselines is entirely optional. You can start by using baselines purely for reporting and gaining insights into your environment.
This approach allows you to:
- Understand your current configuration state without making any changes
- Identify areas that need attention
- Plan your remediation strategies carefully before implementing them
As you become more comfortable with the tool and confident in your baselines, you can gradually implement automated remediation where it makes sense for your organization.
Remember, in the world of IT management, what you don’t know can hurt you. With Configuration Manager baselines and configuration items, you have the tools to know your environment inside and out. Start small, learn continuously, and gradually expand your use of these powerful features.
Whether you’re just starting out or looking to enhance your existing Configuration Manager implementation, baselines and configuration items offer a path to better, more informed IT management. Use them wisely, and you’ll sleep better at night knowing your systems are exactly as they should be – and more importantly, you’ll have the data to prove it.