Introduction
Managing permissions for system-assigned identities in Azure Automation and Azure Logic Apps can be tricky due to UI limitations, especially when dealing with Microsoft Graph permissions. This guide outlines how to use an Excel spreadsheet and PowerShell to delegate these permissions accurately. It aims to simplify permission assignment by detailing the use of New-MgServicePrincipalAppRoleAssignment cmdlet for system-assigned identities, making the process more direct and manageable.
The Excel Spreadsheet: A Detailed Permission Guide
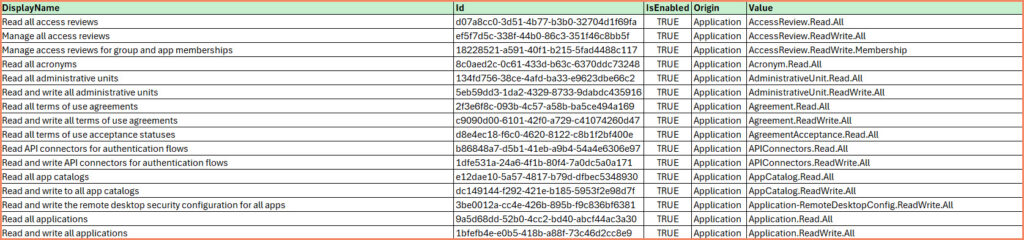
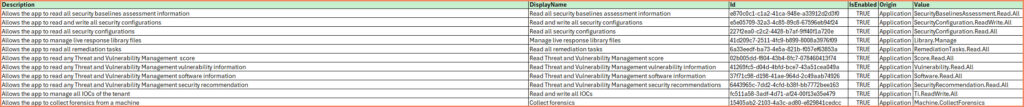
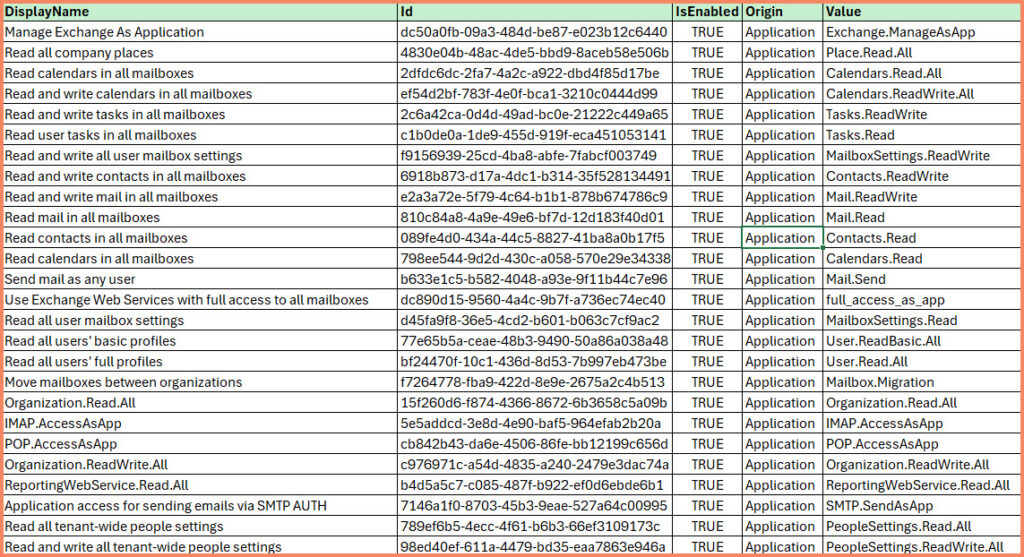
The heart of this guide is an Excel spreadsheet organized into four distinct pages: Microsoft Graph, Windows Defender ATP, Exchange Online and Microsoft Threat Protection. Version 1.1 of this spreadsheet includes permission sets specific to these services, offering a valuable resource for administrators tasked with managing system-assigned identities.
Excel Spreadsheet Structure
- Microsoft Graph: This page lists permissions related to Microsoft Graph, detailing the various operations that can be performed through the Graph API.
- Windows Defender ATP: Focuses on permissions for Defender for Endpoint, providing administrators with the capability to manage devices etc.
- Microsoft Threat Protection: Contains permissions for Microsoft Threat Protection.
- Exchange Online
The spreadsheet serves not just as a reference but as a practical tool for streamlining the process of permission assignment. By consolidating permission names and details in one place, it enables a straightforward method for identifying and assigning the appropriate permissions to system-assigned identities.
Utilizing the Spreadsheet with PowerShell
With the required permissions identified within the spreadsheet, they can be effectively assigned using the New-MgServicePrincipalAppRoleAssignment cmdlet in PowerShell. This cmdlet necessitates the specification of several parameters for successful permission assignment:
- AppRoleId: The unique identifier for the application role you wish to assign.
- ServicePrincipalId: The identifier for the service principal associated with the application or service you’re assigning permissions for.
- ResourceId: This parameter typically requires the object ID of the resource service principal for which the role is being assigned.
- PrincipalId: Represents the object ID of the system-assigned identity receiving the role assignment.
To obtain the ServicePrincipalId and ResourceID, use the Get-MgServicePrincipal cmdlet.
PowerShell Functions for Automated Permission Management
To further streamline the process of managing Graph permissions, we’ve developed two PowerShell functions:
- Grant-AutomationAccountGraphPermission
- Get-AutomationAccountGraphPermissions
These functions automate the process of assigning and reviewing
Microsoft Graph permissions for Azure Automation accounts. Here’s a brief overview of each function:
Grant-AutomationAccountGraphPermission
This function assigns a specific Microsoft Graph permission to an Azure Automation account.
This section is reserved for our Premium Members only. Upgrade your membership to access this solution and unlock more benefits.
Get-AutomationAccountGraphPermissions
This function retrieves all currently assigned Microsoft Graph permissions for an Azure Automation account.
This section is reserved for our Premium Members only. Upgrade your membership to access this solution and unlock more benefits.
Benefits of This Approach
- Time-Saving
- Automate permission assignments with a single PowerShell command.
- Error Reduction
- Use the Excel spreadsheet as a reference to ensure accurate permission names.
- Improved Auditing
- Quickly generate reports of current permissions for compliance and security reviews.
Conclusion
By combining the Excel spreadsheet for reference and these PowerShell functions for execution, you can significantly simplify the process of managing Microsoft Graph permissions for Azure Automation accounts. This approach not only saves time but also reduces the risk of errors in permission assignments.
We encourage you to download the Excel spreadsheet and incorporate these PowerShell functions into your Azure management workflows. If you have any questions or feedback, please leave a comment below.