In this blog post, we will explore the new Group Policy settings for Windows LAPS, which can be found in Computer Configuration -> Administrative Templates -> System -> LAPS. These settings provide IT admins with increased control over the management of local administrator account passwords, making it easier to maintain security within the organization.
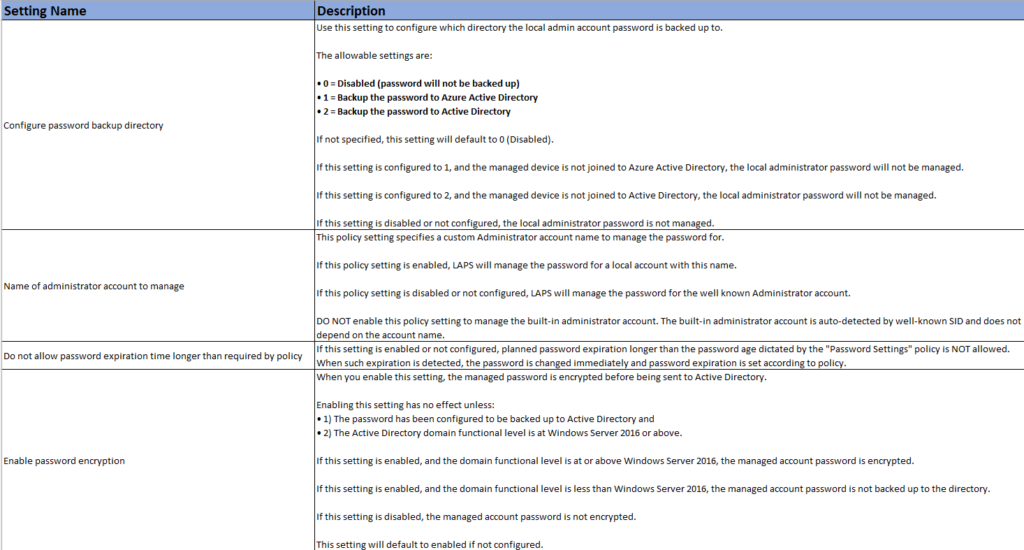
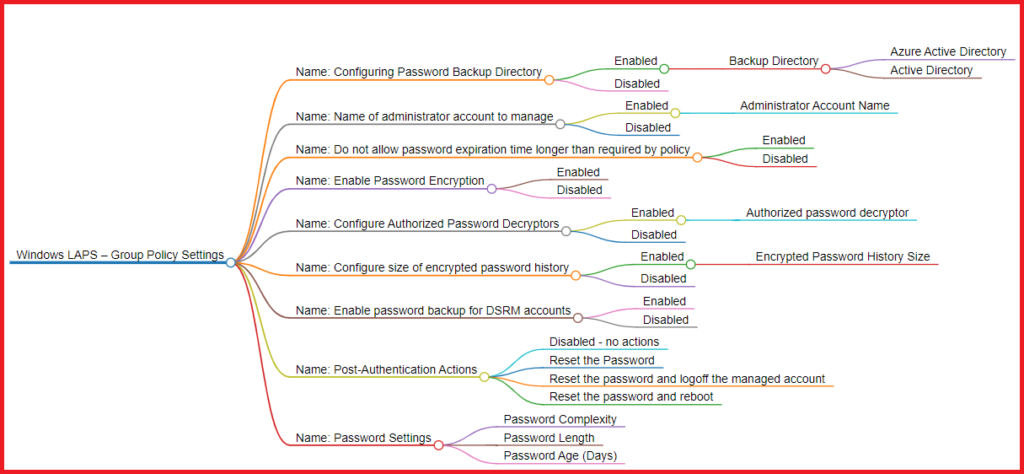
Policy 1: Configuring Password Backup Directory (NEW)
This new LAPS setting allows IT administrators to choose the directory where the local admin account password is backed up. They can choose between three options:
- Disabled (default): Password will not be backed up.
- Azure Active Directory: Back up the password to Azure AD.
- Active Directory: Back up the password to AD.
These options provide flexibility depending on your organization’s infrastructure and requirements. However, ensure that the managed device is joined to the chosen directory for the password to be managed.
Policy 2: Name of administrator account to manage
With this setting, you can specify a custom administrator account name for LAPS to manage the password. This adds versatility to LAPS, as it can now manage passwords for custom-named local admin accounts, in addition to the well-known Administrator account.
Policy 3: Do not allow password expiration time longer than required by policy
To enhance security, this new setting ensures that if a planned password expiration exceeds the age limit defined in the “Password Settings” policy, the password will be changed immediately, and the expiration will be set according to the policy.
Policy 4: Enable Password Encryption (NEW)
For added security, this setting enables password encryption before sending it to Active Directory. Keep in mind that it requires the password to be backed up to Active Directory and the domain functional level to be at least Windows Server 2016.
Policy 5: Configure Authorized Password Decryptors (NEW)
This setting allows admins to define which users or groups can decrypt encrypted passwords. By default, Domain Admins have this privilege, but you can specify a custom group or user using SID in string format or the “domain(group or user)” format.
Policy 6: Configure size of encrypted password history (NEW)
Control the number of previous encrypted passwords stored in Active Directory with this setting. It requires that the password be backed up to Active Directory and that password encryption be enabled.
Policy 7: Enable password backup for DSRM accounts (NEW)
For domain controllers, this setting allows the management and backup of the Directory Services Restore Mode (DSRM) administrator account password to Active Directory. It requires that password encryption be enabled.
Policy 8: Post-Authentication Actions (NEW)
Define actions to be executed after authentication by the managed account with this policy. Choose between resetting the password, resetting the password and logging off the managed account, or resetting the password and rebooting the device, all with a specified grace period.
Actions:
- Disabled – no actions
- Reset the Password
- Reset the password and logoff the managed account
- Reset the password and reboot
Policy 9: Password Settings
Customize password parameters, such as complexity, length, and age, to tailor the security requirements to your organization’s needs.
Windows LAPS GPO Settings Excel Spreadsheet
Download the Group Policy Excel spreadsheet containing all the necessary information about the new LAPS settings, making it even easier to understand and implement these policies in your organization.
Download
Conclusion
The new Windows LAPS Group Policy settings give IT administrators more control and flexibility when managing local administrator account passwords. Implementing these policies will help your organization stay secure and maintain a robust password management system for your Windows environment. Remember to test these policies thoroughly in a lab environment before deploying them to your production network. Happy securing!