Introduction
For those utilizing Microsoft Sentinel, it’s important to have a clear understanding of the event logs you are collecting. The spreadsheet I have developed is a practical tool that enables both consultants and customers to quickly identify which event IDs are included in the Microsoft Sentinel Common Events package. This clarity is crucial when setting up Windows Servers for security event monitoring.
Utilizing the “Windows Security Events via AMA” Data Connector
Microsoft Sentinel includes the “Windows Security Events via AMA” Data Connector, facilitating the streamlined collection of Windows security event logs. This connector utilizes the Azure Monitoring Agent (AMA) and Data Collection Rules (DCR) to efficiently gather the required security event logs. By navigating to the data connector page, users can easily create a new Data Collection Rule by specifying its name, resource group, and subscription.
Specifying Log Collection Preferences
During the creation process, it’s possible to specify which logs to collect, offering four distinct options:
- All Security Events
- Common
- Minimal
- Custom
A critical aspect of using Microsoft Sentinel involves understanding what’s included in the Common Security Events package. This includes identifying the event IDs and the advanced audit policy categories they belong to. It’s important to note that if the advanced audit policies are not configured correctly on the Active Directory (AD) side, it could result in the absence of logs in Sentinel. Therefore, evaluating whether the common logs package suffices for security monitoring is vital.
The process of creating Data Collection Rules (DCR) with the “Windows Security Events via AMA” Data Connector automatically includes a “CreatedBy” tag, labeled as “Sentinel“. Sentinel now permits the creation of a new DCR without the necessity of selecting any resources.
Instead, Azure policies should be utilized for establishing the associations. This approach simplifies the setup process, enabling you to first create the DCR and subsequently manage machine associations through policies.
Azure Policies for Data Collection Rule and Data Collection Endpoint Associations
Microsoft offers a range of policies to configure Windows and Linux machines to be associated with a Data Collection Rule or a Data Collection Endpoint. These policies are:
- Configure Windows Virtual Machines to be associated with a Data Collection Rule or a Data Collection Endpoint
- Configure Windows Arc Machines to be associated with a Data Collection Rule or a Data Collection Endpoint
- Configure Windows Machines to be associated with a Data Collection Rule or a Data Collection Endpoint
- Configure Linux Machines to be associated with a Data Collection Rule or a Data Collection Endpoint
- Configure Linux Virtual Machines to be associated with a Data Collection Rule or a Data Collection Endpoint
- Configure Linux Arc Machines to be associated with a Data Collection Rule or a Data Collection Endpoint
The policies for configuring Windows Machines and Linux Machines to be associated with a Data Collection Rule or a Data Collection Endpoint support three distinct resource types:
- Windows Virtual Machines
- Virtual Machine Scale Sets
- Arc Machines
Other policies are tailored to specific resource types.
Excel Spreadsheet for Common Logs
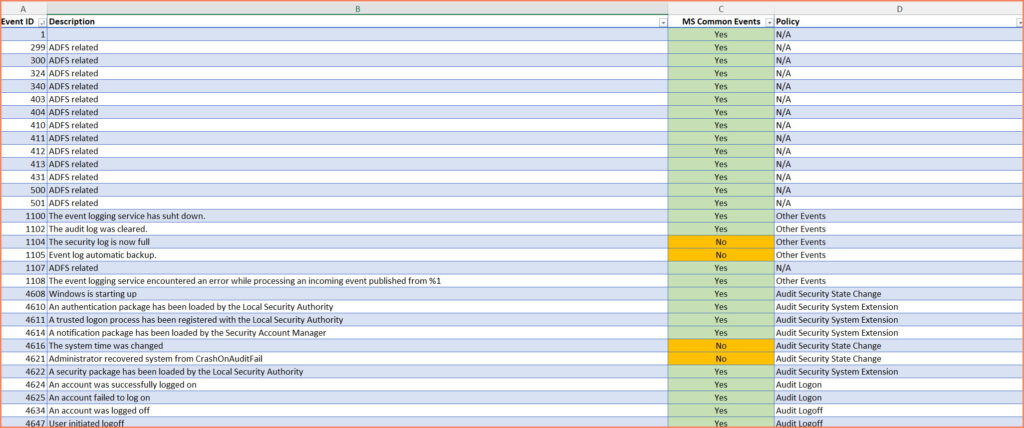
This Excel spreadsheet not only lists the standard Event IDs included in the Microsoft Sentinel Common Security package but also highlights additional Event IDs to the same audit categories. Those Event IDs that are part of the Common package are marked with ‘YES‘ for quick reference. In contrast, the ones not included in the package are indicated with ‘NO‘. In total, the spreadsheet covers up to 141 Event IDs within the Common Security package.
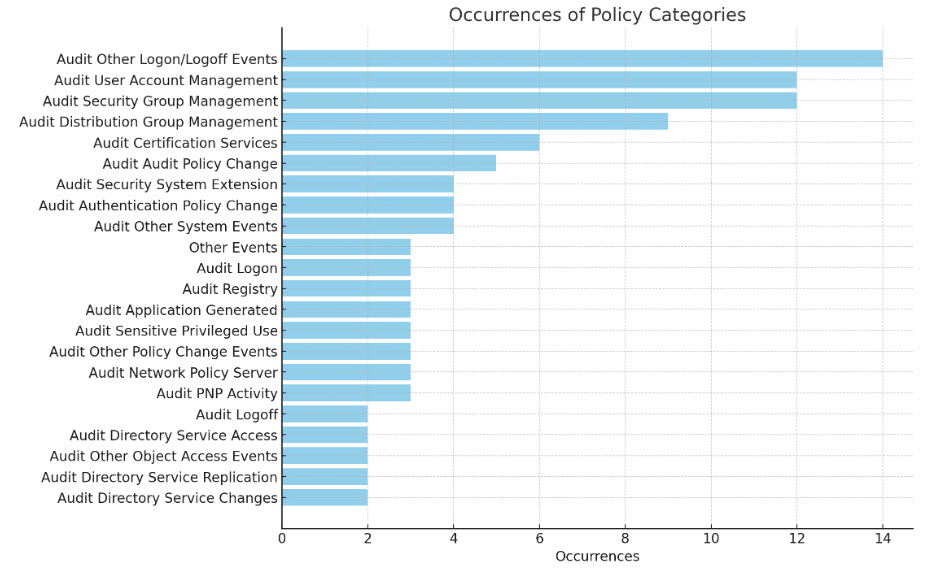
Based on my research, we can identify the following Active Directory Advanced Audit Policy categories.