Introduction
In the ever-evolving landscape of cybersecurity, having the right tools is only half the battle. The real challenge lies in effectively navigating and utilizing these tools when an incident arises. The Microsoft 365 Defender portal serves as a centralized hub for managing security incidents, providing a streamlined and intuitive user experience. This article offers a hands-on journey through the portal, highlighting the seamless integration of tools like Microsoft Defender for Identity and showcasing the practical steps involved in incident response. Whether you’re a seasoned security professional or just starting out, understanding the user experience within the Microsoft 365 Defender portal is important to effectively handle the incident. Let’s dive in.
Identifying an Incident
When it comes to cybersecurity, early detection is the key to effective mitigation. Anomalies, whether they manifest as unfamiliar login attempts, unexpected data access, or unusual network patterns, often serve as the first indicators of a potential security incident. Tools integrated within the Microsoft 365 Defender portal, especially Microsoft Defender for Identity, play a important role in detecting these early signs. By continuously monitoring user behaviors and network activities, they provide real-time alerts, ensuring that security teams are instantly aware of any suspicious activities. This immediate awareness allows for swift action, setting the stage for a comprehensive incident response process within the portal.
The Incident Dashboard
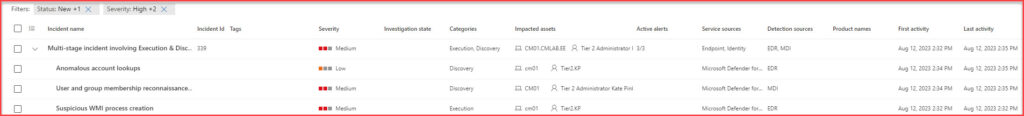
The Microsoft 365 Defender portal’s Incident Dashboard serves as the nerve center for security professionals, offering a comprehensive view of ongoing incidents. Here’s a breakdown of its features:
- Incident Timelines: These visual aids depict the progression of incidents, allowing teams to grasp the sequence and duration of suspicious activities.
- Severity Levels: Instantly gauge the urgency of each incident. The dashboard classifies incidents by their potential impact, from high-risk threats to minor anomalies.
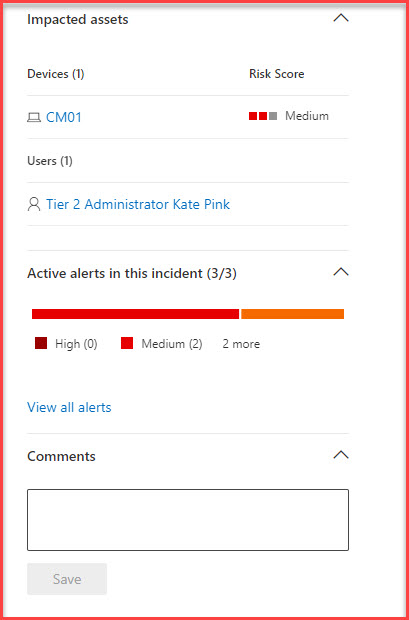
- Affected Entities: Identify which users, devices, or resources are embroiled in an incident. This information is crucial for understanding the incident’s scope and potential fallout.
- Integration with Microsoft Defender for Identity: The dashboard pulls in data from Microsoft Defender for Identity, offering a deeper context. This integration sheds light on identity-related anomalies, enriching the overall incident perspective.
To provide a simple example, consider an incident from Defender for Identity:
- Incident Name: Network mapping reconnaissance (DNS) on one endpoint
- Incident ID: 338
- Severity: Medium
- Categories: Discovery
- Impacted Assets: CM01.CMLAB.EE
- Active Alerts: 1
- Service Sources: Identity
- Detection Sources: MDI
- First Activity: 2023-08-11T07:30:12.838Z
- Last Activity: 2023-08-11T07:30:12.838Z
- Status: Active
The Incident Dashboard shows you the Incident Name and impacted assets, severity, and the Detection Sources. Incident management through the unified portal makes it much much easier for the incident responders.
Incident Investigation
The Microsoft 365 Defender portal is designed to provide a comprehensive and detailed view of each incident, ensuring that incident responders can quickly understand and act on threats:
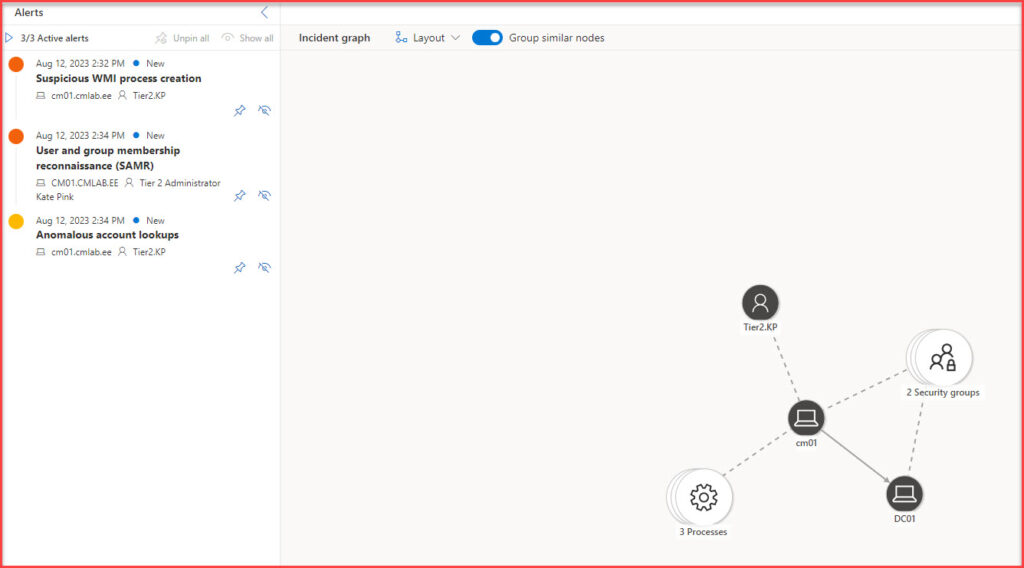
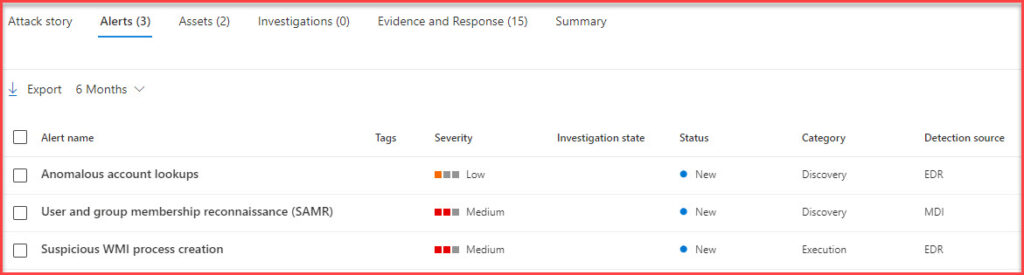
- Incident Graph (Attack Story): This visual representation provides an immediate overview of the incident, showcasing device names, the type of attack, timestamps, and the current status. It’s a snapshot that gives investigators a starting point.
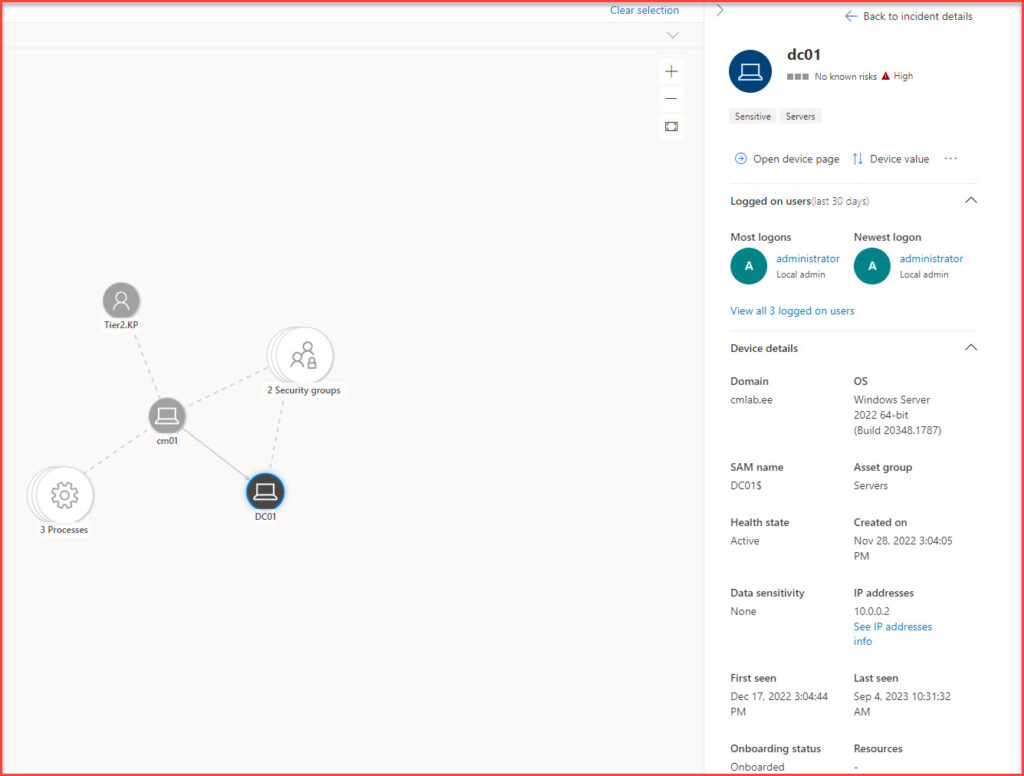
- Device Details: By clicking on a device within the Incident Graph, you can access more detailed information about that device, if available. This can include its history, associated users, and more.
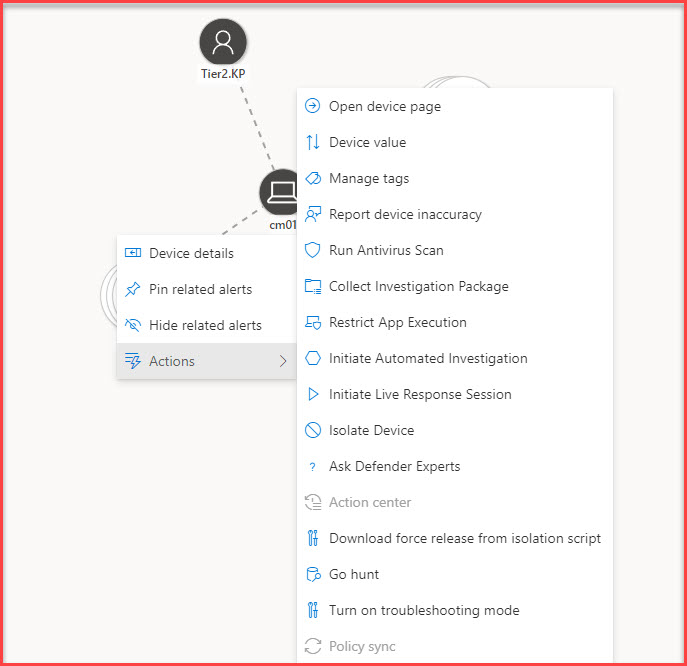
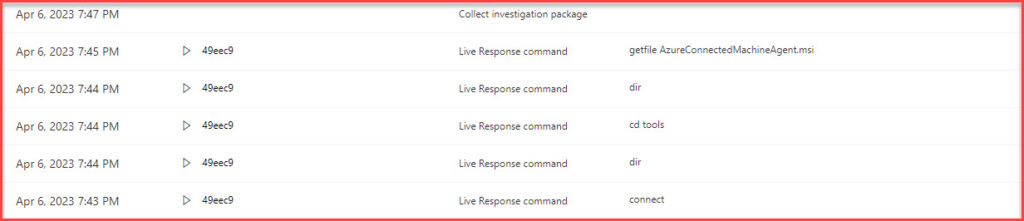
- Direct Actions from the Graph: Not only can you view device details, but you can also initiate direct actions from the attack story panel. Whether you need to isolate a device, collect additional logs, or take other remedial actions, the portal allows for swift response.
- Alerts Overview: The second page of the incident view lists all the alerts associated with that incident. This aggregation ensures that you have a complete picture of what triggered the incident and the various alerts that were raised in its wake.
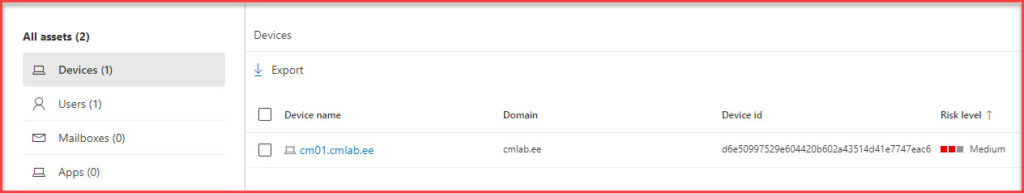
- Assets Panel: The third section provides a view of all the assets involved in the incident. This includes devices, users, mailboxes, and apps, giving a comprehensive view of the scope of the incident.
- Investigations: The fourth panel delves into investigations related to the incident. This can include automated investigations triggered by the system or manual investigations initiated by security professionals.
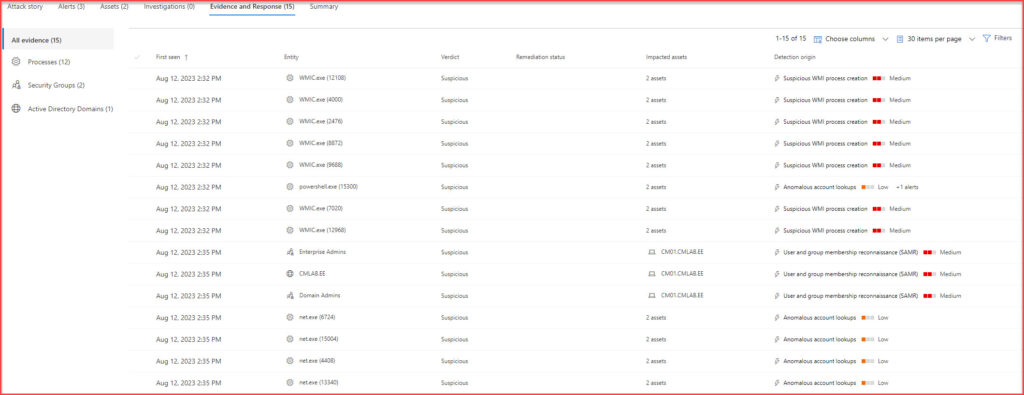
- Evidence and Response: This section provides a collated view of all the evidence related to the incident and the responses that were initiated. It’s a crucial section for understanding the actions taken during the incident response.
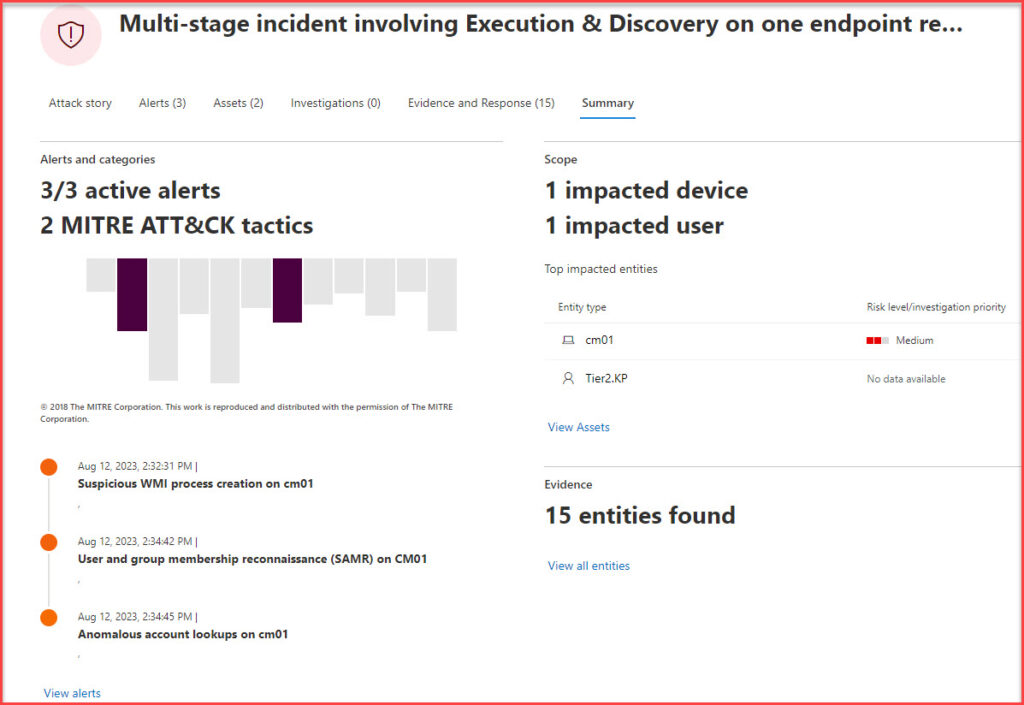
- Summary: The Summary page in the Microsoft 365 Defender portal offers a concise overview of an incident. It showcases recognized Mitre ATT&CK tactics, the timeline of the incident, involved entities, and the status. This snapshot provides security professionals with essential details briefly, aiding in swift decision-making.
If you click on a specific alert, you’re taken to a more detailed view. This includes the attack path, device risk levels, alert status, and other crucial details that provide context and depth to the alert. Incident investigation is where data becomes actionable intelligence. With the structured and detailed approach of the Microsoft 365 Defender portal, security professionals are equipped to understand, analyze, and respond to incidents effectively.
Collaborative Analysis
Collaboration is key. Addressing complex incidents often requires the collective expertise of multiple team members, each bringing their unique perspective to the table. The Microsoft 365 Defender portal recognizes this and offers features to foster teamwork:
- Shared Investigation Space: Within the portal, team members can simultaneously access incident details, ensuring everyone is on the same page. This shared space eliminates information silos and promotes a unified response.
- Comments & History: As you delve into an incident, you can add comments or highlight specific data points. These comments are visible to all team members, facilitating knowledge sharing and ensuring that critical insights aren’t missed.
- Historical Context: Past incidents and their resolutions can offer valuable insights. The portal allows teams to access historical data, ensuring that past experiences inform current responses.
By fostering collaboration, the Microsoft 365 Defender portal ensures that incident response is not just swift but also well-informed, leveraging the collective expertise of the entire security team.
Incident Remediation
When an incident is identified and thoroughly investigated, the next critical step is remediation. The goal is to quickly address the threat, minimizing potential damage and ensuring the integrity of the organization’s digital assets. With Microsoft Defender for Identity integrated into the Microsoft 365 Defender portal, this process becomes streamlined and effective:
- Automated Responses: For certain well-defined threats, the portal allows for automated responses. This means that as soon as a threat is detected, predefined actions can be triggered, reducing the window of vulnerability.
- Integration with Other Defender products: Microsoft Defender for Identity doesn’t operate in isolation. It’s part of a broader ecosystem of security tools within the Microsoft 365 suite. This integration ensures that actions taken in one tool are reflected across the board, providing a cohesive response strategy.
- Detailed Logging: Every action taken during the remediation process is logged within the portal. This not only provides a clear record for future reference but also aids in accountability and compliance.
By leveraging the capabilities of Microsoft Defender for Identity during the remediation phase, organizations can ensure that their response to incidents is both swift and effective, addressing threats head-on and safeguarding their digital environment.
Post-Incident Analysis and Improvement
After resolving an incident, it’s important to step back and evaluate the entire event. This post-incident analysis phase within the Microsoft 365 Defender portal is dedicated to extracting insights and refining strategies for the future:
- Incident Review: Delve into the specifics of the incident. Analyze the root cause, the response timeline, and the effectiveness of the remediation steps taken. This review helps in identifying areas of improvement.
- Security Strategy Refinement: Based on the insights from the incident review, adjust and refine the organization’s security protocols and strategies. This ensures that the organization is better equipped to handle similar threats in the future.
- Training and Awareness: If the incident highlighted gaps in staff knowledge or awareness, use this opportunity to enhance training programs. Ensure that all team members are up-to-date with the latest security best practices.
- Tool and Resource Evaluation: Assess if the current tools and resources were adequate in handling the incident. If there are shortcomings, consider augmenting or updating the tools to better suit the organization’s needs.
The post-incident phase is not just a retrospective exercise. It’s an active effort to continuously improve, ensuring that the organization’s security posture remains robust and resilient against evolving threats. In many cases companies are not doing it and they just skip it.
Conclusion
Navigating the complexities of incident response requires a combination of robust tools and a clear strategy. The Microsoft 365 Defender portal, with its comprehensive features and user-centric design, offers organizations a reliable ally in this endeavor. By leveraging its capabilities and continuously refining strategies based on insights and feedback, organizations can ensure that they are always a step ahead in their cybersecurity journey.
It is really important to practice incident response! Microsoft changes M365 Defender Portal quite often and it is important to understand all these changes. If the incident arises, you have the needed knowledge and experience.
Call to Action
Are you ready to fortify your organization’s digital defenses and stay a step ahead of cyber threats? Don’t miss the opportunity to join my upcoming exclusive webinar, where I dive into the world of Microsoft Defender for Identity (MDI) and explore its comprehensive implementation process. This webinar is designed to empower you with the knowledge and tools you need to enhance your organization’s cybersecurity posture.
Reserve Your Spot Today
Mark your calendar for Thursday, September 14, 2023, from 10:00 AM to 12:00 PM Pacific Time (US & Canada). The webinar will be hosted on Microsoft Teams, providing you with a convenient and interactive platform to learn from a cybersecurity expert.
Limited Spaces Available
Space is limited, so make sure to secure your spot early. To register for this free webinar and gain valuable insights into mastering the implementation of Microsoft Defender for Identity, please complete the registration form. Registration form – Mastering Microsoft Defender for Identity: A Comprehensive Guide to Implementation – Kaido Järvemets (kaidojarvemets.com)
Empower Your Cybersecurity Journey
In addition to the webinar, explore my Defender for Identity and Sentinel service offerings to learn how I can assist in implementing and optimizing these solutions for your business. For deeper insights, discussions, and expert advice, consider joining my blog membership and be part of a community that prioritizes cybersecurity excellence.
Don’t Wait for a Breach
Be proactive and safeguard your organization’s future today. Cyber threats are evolving, and preparation is key. By taking steps now to enhance your cybersecurity measures, you’re investing in the resilience and security of your organization’s digital assets.
Reserve your spot now and take the first step towards a more secure future.