Introduction
Many organizations today rely on Configuration Manager for their update management needs. However, as cloud services become increasingly integral to IT operations, migrating to Azure Update Manager supplemented by Azure Arc presents a forward-looking strategy. This transition, though promising, requires careful planning and auditing to ensure a seamless migration. In this post, we’ll discuss how to prepare for this shift, spotlighting the essential steps and tools for auditing current maintenance windows and embracing Azure Maintenance Configurations.
Auditing Current Maintenance Windows
The first step in preparing for migration to Azure Update Manager is to assess your current maintenance windows in Configuration Manager. This involves understanding the configurations, durations, and schedules of these windows to identify any potential challenges or limitations that might affect migration.
To facilitate this audit, I have developed a PowerShell script that extracts and reports on the details of your Configuration Manager maintenance windows and it also analyzes the maintenance windows against the Azure Maintenance Configurations scheduling format and shows the correct value you need for the automation scripts.
Solution – Audit Configuration Manager Maintenance Windows for Azure
This section is reserved for our Premium Members only. Upgrade your membership to access this valuable content and unlock more benefits.
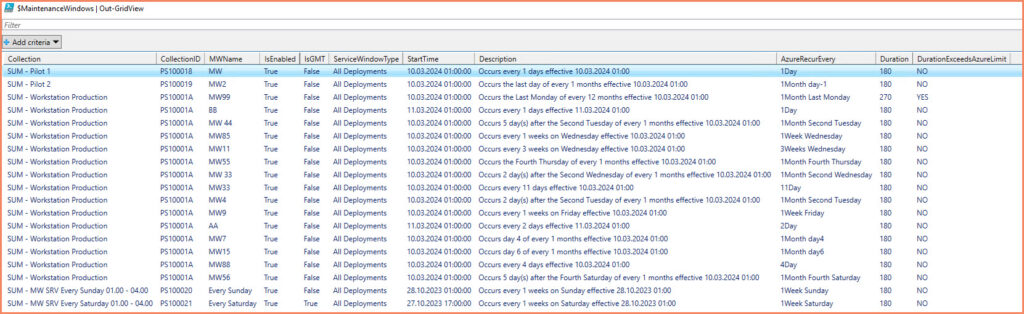
Script Output
The script provides a detailed output for each audited maintenance window from Configuration Manager, enabling a comprehensive review of current configurations against Azure Maintenance Configurations standards. For each maintenance window, the output includes essential attributes, such as scheduling details, duration, and whether adjustments are required to meet Azure’s limitations. This information is pivotal for planning your migration strategy, ensuring that maintenance windows are correctly replicated in Azure with minimal adjustments.
Here’s a breakdown of the output columns and what they represent:
- Collection: The name of the device collection the maintenance window applies to.
- CollectionID: A unique identifier for the device collection.
- MWName: The descriptive name of the maintenance window.
- IsEnabled: Indicates whether the maintenance window is currently active.
- IsGMT: Specifies whether the start time is based on GMT.
- ServiceWindowType: The type of operations allowed during the maintenance window.
- StartTime: When the maintenance window begins.
- Description: A brief overview of the maintenance window’s schedule.
- AzureRecurEvery: The equivalent recurrence pattern in Azure Maintenance Configurations format.
- Duration: The length of the maintenance window in minutes. Azure supports maintenance windows up to 3 hours and 55 minutes.
- DurationExceedsAzureLimit: Indicates if the window’s duration surpasses Azure’s maximum allowed time.
Understanding Azure Maintenance Configurations
Azure Maintenance Configurations offer a structured way to manage updates and maintenance tasks for both cloud and on-premises environments integrated with Azure, such as through Azure Arc. This feature enables administrators to define specific times for maintenance activities, helping ensure minimal disruption to operations. It supports detailed scheduling options, including the ability to set recurrence patterns, duration, and the exact timing of maintenance windows.
Utilizing Azure Maintenance Configurations can significantly streamline the process of applying updates across a diverse infrastructure. It allows for precise control over when maintenance tasks occur, providing the flexibility needed to align with business requirements and operational practices.
Creating and managing these configurations can be achieved through the Azure portal, using PowerShell for automated scripting, or via API´s. This means that organizations can adopt an approach that best matches their existing workflows and preferences, making it easier to integrate Azure Maintenance Configurations into their IT management practices.
Creating a Maintenance Configuration for Azure Arc-Connected Servers
When setting up maintenance configurations for Azure Arc-connected servers, it’s crucial to understand the specific requirements and limitations to ensure a smooth operation.
Here’s a detailed guide to help you navigate through this process:
- Duration Limit: The maximum duration for maintenance windows is currently set to 3 hours and 55 minutes. This is a key factor to consider during your planning phase to ensure your maintenance activities are appropriately scheduled within this timeframe.
- Timezone Formatting: The Timezone property requires a specific format. It’s important to note that the value should not be in all capital letters. Using all capital letters can prevent the schedule from being accessible through the Azure portal’s user interface.
- RecurEvery Formatting: The RecurEvery property demands special attention due to its specific formatting requirements. Initially, this might seem challenging, but to assist with this, I’ve developed a custom auditing script. This script not only examines your existing maintenance windows but also outputs the format required for Azure, simplifying the transition.
- LinuxParameterClassificationToInclude: For Linux configurations, both Security and Critical classifications must be defined simultaneously. It’s not permissible to include only one of these classifications, emphasizing the need for precise specification.
- Windows Classifications: Windows classification options are straightforward. You can utilize the following values: ‘Critical’, ‘Security’, ‘UpdateRollup’, ‘FeaturePack’, ‘ServicePack’, ‘Definition’, ‘Tools’, ‘Updates’. These classifications allow for flexible and comprehensive maintenance planning.
Before proceeding with the New-AzMaintenanceConfiguration cmdlet, it’s essential to install the Az.Maintenance PowerShell module. This module can be easily installed from the PowerShell Gallery using the following command:
Install-Module -Name Az.Maintenance
This setup ensures you have the necessary tools and configurations to effectively manage maintenance schedules for your Azure Arc-connected servers, with a focus on compliance with Azure’s requirements and limitations.
Example of Creating a Maintenance Configuration
Below is a code snippet to demonstrate how to create a maintenance configuration. This example emphasizes the correct formatting for the duration, timezone, and classification properties, ensuring a successful configuration.
<#
=================================================================================
DISCLAIMER:
This script is provided "as-is" with no warranties. Usage of this script is at
your own risk. The author is not liable for any damages or losses arising from
using this script. Please review the full legal disclaimer at:
https://kaidojarvemets.com/legal-disclaimer/
=================================================================================
#>
$mwParams = @{
ResourceGroupName = "RG-PROD-IT-PATCHING-CONFIGURATION-WE"
Name = "MW-EVERY-SATURDAY-0200-0400"
Location = "West Europe"
MaintenanceScope = "InGuestPatch"
StartDateTime = "2024-03-11 02:00"
Timezone = "FLE Standard Time"
RecurEvery = "Week Saturday"
Duration = "02:00"
WindowParameterClassificationToInclude = @("FeaturePack", "ServicePack")
InstallPatchRebootSetting = "IfRequired"
LinuxParameterClassificationToInclude = @("Other")
ExtensionProperty = @{"InGuestPatchMode" = "User"}
}
# Create the maintenance configuration using splatting
New-AzMaintenanceConfiguration @mwParams
Patch Tuesday Maintenance Windows
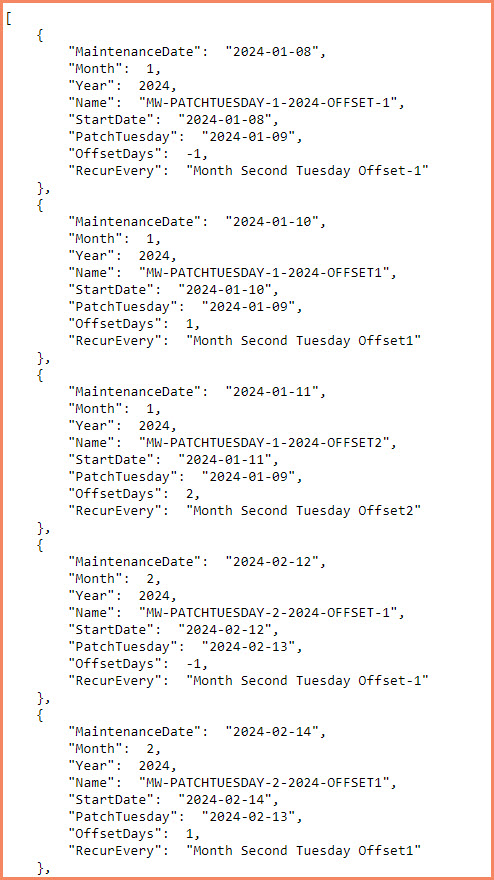
For many organizations, aligning maintenance schedules with Patch Tuesday is a critical part of their update management strategy. To support this, I’ve created a comprehensive JSON file that outlines maintenance windows for the entire year of 2024, specifically tailored around Patch Tuesday dates. This resource can be particularly valuable when planning your update schedules in Azure Update Manager, ensuring that maintenance activities are correctly timed with these important update releases.
The JSON file is available on GitHub and serves as a practical input for creating Azure Maintenance Configurations that coincide with Patch Tuesday. Here’s the link to access the file:
This file includes detailed schedules for each month, offering a streamlined approach to integrating Patch Tuesday into your Azure Update Management workflows. Whether you’re migrating existing maintenance windows or establishing new ones, this data may simplify the process, providing ready-to-use schedules that align with Patch Tuesday.
Summary
Transitioning from Configuration Manager to Azure Update Manager signifies a strategic shift towards a more integrated and cloud-based management approach for your IT infrastructure. This journey involves auditing existing maintenance windows, understanding Azure Maintenance Configurations, and leveraging PowerShell scripts for efficient migration. With the custom script provided, organizations can effortlessly align their current maintenance schedules with Azure’s requirements, ensuring a seamless migration process. Additionally, the Patch Tuesday Maintenance Windows resource offers a structured approach to scheduling updates based on critical security timelines.
Call to Action (CTA)
Schedule a Call Today and let’s ensure your transition to Azure Update Manager is seamless and optimized for your needs. I’m here to help you every step of the way.