Introduction
In our previous articles, we embarked on a journey through the foundational aspects of Active Directory (AD) and Microsoft Defender for Identity (MDI). We explored their core functionalities, shedding light on their pivotal roles in modern cybersecurity. As we progress in this series, it’s time to elevate our discussion. Today, we’ll delve deeper into the advanced capabilities of MDI, unveiling its integrative prowess with other Microsoft security tools. This synergy not only amplifies the protection offered but also streamlines the process of identity investigations and real-time responses.
Advanced Remediation Actions in MDI
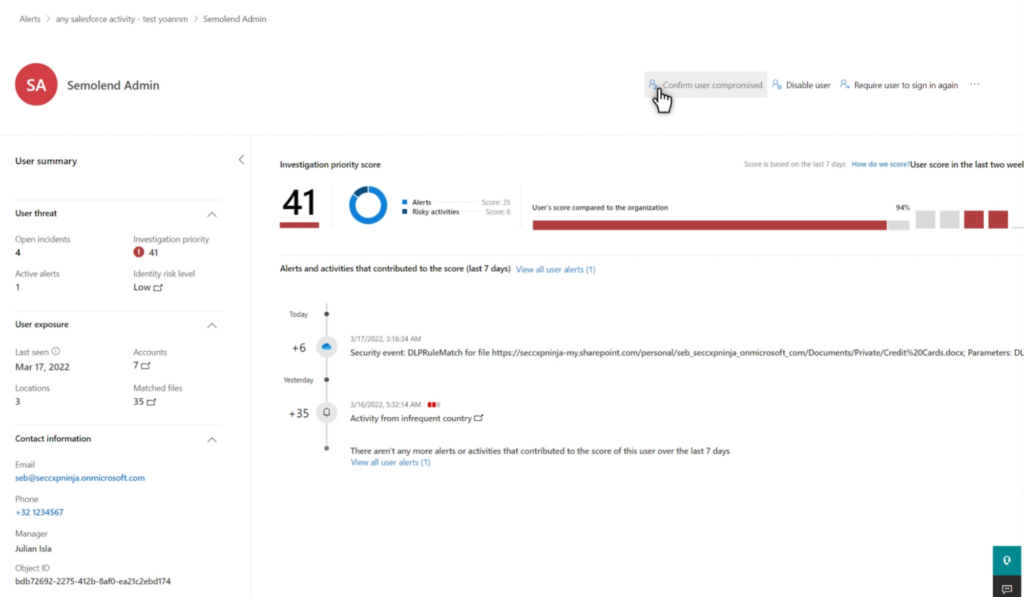
Microsoft Defender for Identity (MDI) is not just about identifying threats but also about taking actions against them. When a user account shows signs of compromise or suspicious behavior, MDI provides direct remediation actions to ensure the security of the network and prevent further malicious activities.
Here are the specific remediation actions available in MDI:
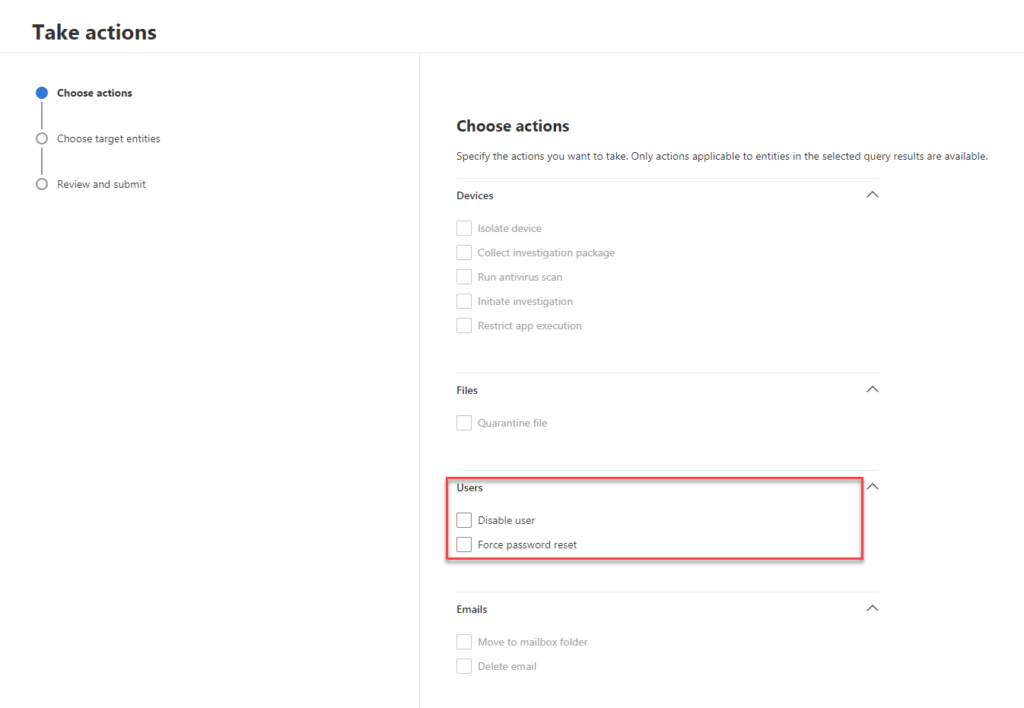
- Disable user in Active Directory: This action temporarily prevents a user from logging into the on-premises network. By disabling a potentially compromised account, you can halt any further lateral movement attempts and prevent data exfiltration.
- Suspend user in Entra ID: By suspending a user in Entra ID, you temporarily block their access to Entra ID. This action is crucial in minimizing the time between disabling a user in Active Directory and syncing this status to the cloud, ensuring that compromised users can’t exploit cloud resources.
- Reset user password: This action prompts the user to change their password during their next logon attempt. By forcing a password reset, you ensure that the account can’t be used for further impersonation attempts by potential attackers.
These remediation actions are accessible directly from various points within MDI, including the user page, the user side panel, the advanced hunting page, and the action center. By providing these direct response capabilities, MDI empowers security teams to act swiftly and decisively against threats, ensuring a robust defense mechanism in real-time.
Microsoft Defender for Endpoint: Beyond Basic Protection
The collaboration between Microsoft Defender for Identity (MDI) and Microsoft Defender for Endpoint showcases the strength of unified security. While MDI focuses on identity-based threats, Defender for Endpoint expands the scope, offering comprehensive protection for devices against a wide range of cyber threats.
Defender for Endpoint isn’t just about passive protection; it’s a dynamic tool equipped with a range of incident response actions. When a threat is detected, administrators aren’t left scrambling. Instead, they have a suite of powerful tools at their fingertips:
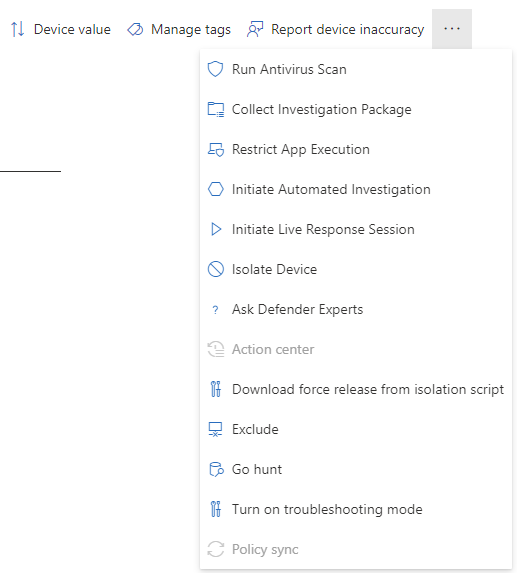
- Device Isolation: In the face of a potential compromise, Defender for Endpoint allows administrators to isolate devices. This ensures that the threat is contained, preventing its spread
- Collect investigation package: This action allows you to gather a package of forensic evidence from a machine. It’s useful for deep-dive investigations and can be used offline.
- Run antivirus scan: Initiates an immediate antivirus scan on the machine. This helps in detecting and dealing with any malicious entities.
- Restrict app execution: This action restricts the machine from running any software, except for the software that’s been pre-approved.
- Initiate automated investigation: This action starts an automated investigation on the machine. The investigation can result in various remediation actions, depending on the findings.
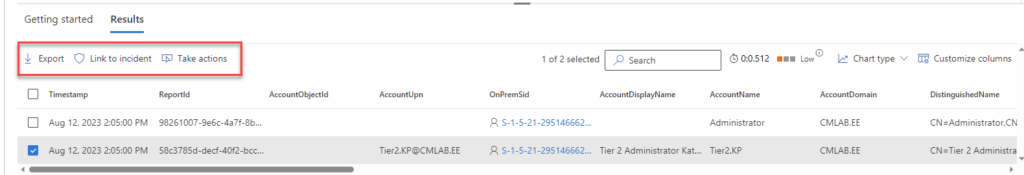
The Microsoft 365 Defender portal serves as the backbone for this integration, bringing together the capabilities of MDI and Defender for Endpoint. Through this portal, organizations can seamlessly access and utilize the combined features of both tools, ensuring a unified and comprehensive approach to security.
The integration of MDI with Defender for Endpoint represents a holistic approach to security. It’s not just about detecting threats but also about understanding them and responding effectively. With these combined tools, organizations are not just shielded from threats; they’re equipped to face them head-on.
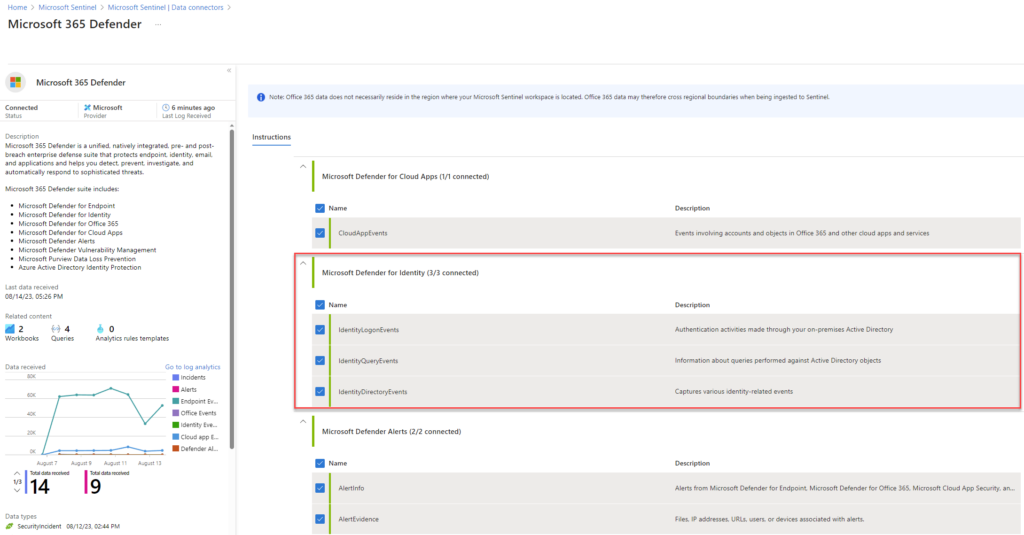
M365 Defender XDR Data Connector in Sentinel
I recommend implementing Sentinel for additional benefits if you are using Microsoft 365 Defender solutions today. Sentinel allows you to define custom analytics rules and attach automated responses for these rules. Sentinel offers built-in tasks within the Sentinel, and you can combine your automation rules with Logic Apps. Logic Apps allow you to do a lot more. You can connect to Defender for Endpoint, Azure Automation, etc., to perform different activities.
M365 Defender Data Connector in Sentinel Integration Benefits:
- Incident Automation
- Improved Threat Analysis
- Custom Responses with Logic Apps
The Power of Integration: Microsoft’s Unified Security Approach
In the dynamic landscape of cybersecurity, the ability to centralize and streamline operations is paramount. Microsoft’s security ecosystem, with Microsoft Defender for Identity (MDI) as a pivotal component, exemplifies this principle by offering a cohesive and integrated approach.
Here’s how this integration amplifies security operations:
- One-Stop Management: The beauty of Microsoft’s integrated approach is the elimination of silos. Security professionals can navigate threats, analyze data, and initiate responses across services like Defender for Endpoint and Microsoft Sentinel, all from a unified platform.
- 360-Degree Visibility: The seamless flow of data across the platform, facilitated by MDI, ensures a comprehensive view of security events. This holistic perspective is invaluable in identifying trends, correlations, and potential threats.
- Agile Responses: In the face of potential threats, every second counts. The integrated nature of Microsoft’s security services ensures that alerts are not only consolidated but also acted upon with unmatched speed and precision.
- Simplicity in Complexity: The challenge in modern cybersecurity is managing the vast array of tools and data streams. Microsoft’s unified approach simplifies this complexity, ensuring that security operations are efficient and error-free.
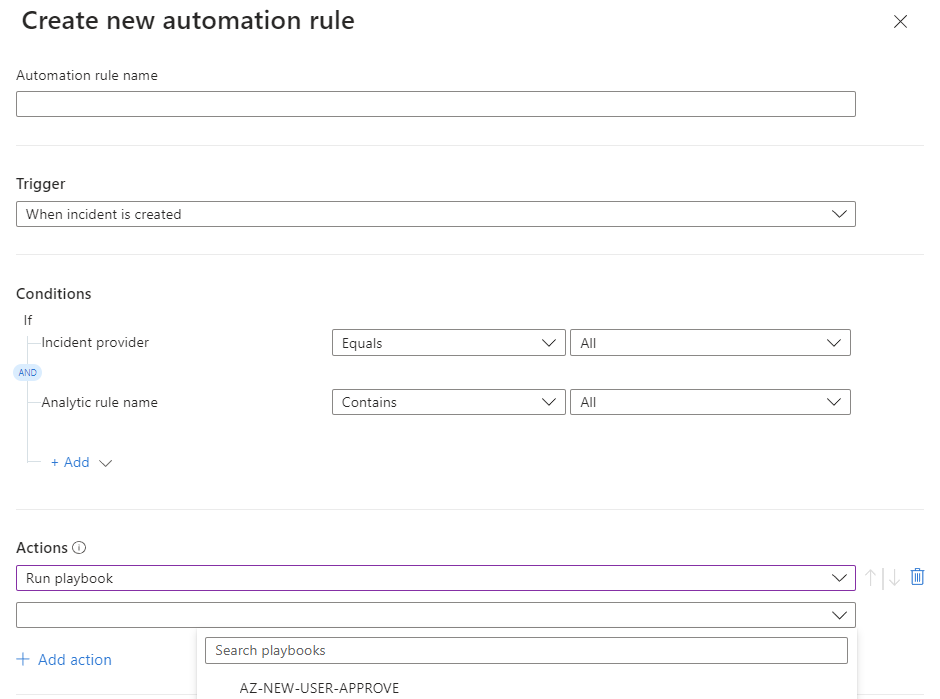
Let’s visualize this with a practical example
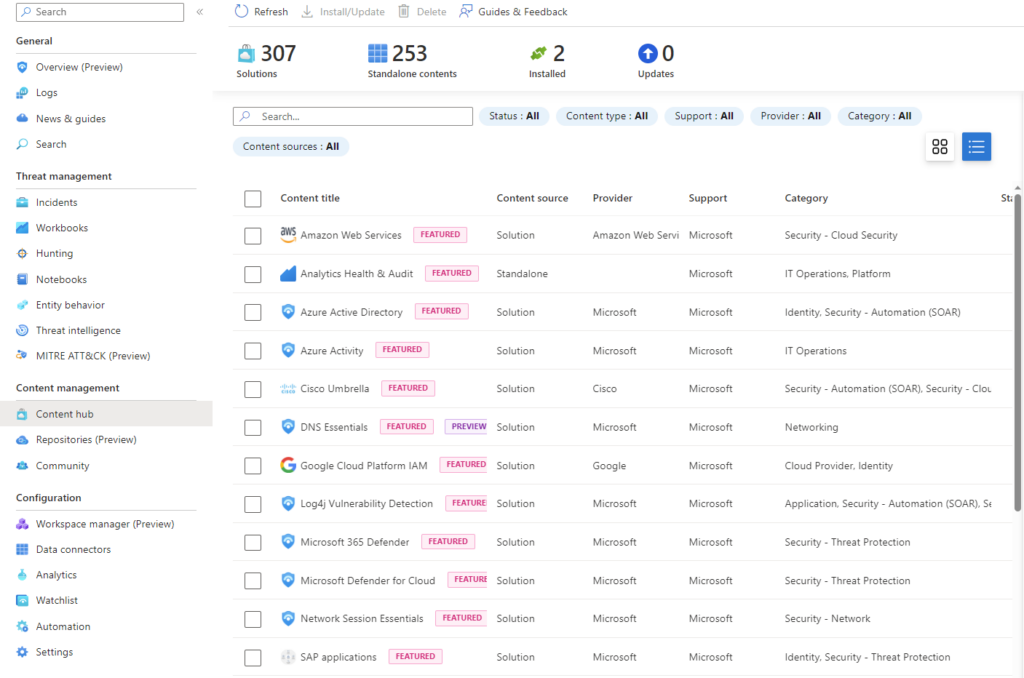
When MDI detects a threat within the Active Directory, it immediately identifies and flags this security issue. This alert is then channeled to Microsoft Sentinel. If associated automation rules are set up in Sentinel, they are triggered. For instance, one such rule could initiate device isolation, but there are numerous other actions and solutions available, both from Microsoft and the community. It’s worth noting that Microsoft has built a content hub for Sentinel, which is directly accessible from the Sentinel console, offering a plethora of pre-configured solutions and insights.
This collaboration between Microsoft’s Defender security services and Sentinel exemplifies the power of an integrated security strategy. This comprehensive approach is not commonly found among other vendors, which is one of the reasons Microsoft’s security services stand out.
Conclusion
In today’s rapidly evolving cyber landscape, a fragmented approach to security is a recipe for vulnerabilities. The true strength lies in unification, where different tools and platforms come together, working in harmony. With Microsoft Defender for Identity (MDI) at its core, organizations are not just leveraging a tool but adopting an ecosystem. This ecosystem, with its seamless integrations and advanced capabilities, offers a comprehensive shield against potential threats.
The advantages of such a unified approach are clear: enhanced visibility, streamlined operations, faster response times, and a more robust defense mechanism. But beyond these tangible benefits, there’s the peace of mind that comes from knowing that your organization’s digital assets are protected by a cohesive and coordinated security strategy.
Call to Action
Are you ready to fortify your organization’s digital defenses and stay a step ahead of cyber threats? Don’t miss the opportunity to join my upcoming exclusive webinar, where I dive into the world of Microsoft Defender for Identity (MDI) and explore its comprehensive implementation process. This webinar is designed to empower you with the knowledge and tools you need to enhance your organization’s cybersecurity posture.
Reserve Your Spot Today
Mark your calendar for Thursday, September 14, 2023, from 10:00 AM to 12:00 PM Pacific Time (US & Canada). The webinar will be hosted on Microsoft Teams, providing you with a convenient and interactive platform to learn from a cybersecurity expert.
Limited Spaces Available
Space is limited, so make sure to secure your spot early. To register for this free webinar and gain valuable insights into mastering the implementation of Microsoft Defender for Identity, please complete the registration form. Registration form – Mastering Microsoft Defender for Identity: A Comprehensive Guide to Implementation – Kaido Järvemets (kaidojarvemets.com)
Empower Your Cybersecurity Journey
In addition to the webinar, explore my Defender for Identity and Sentinel service offerings to learn how I can assist in implementing and optimizing these solutions for your business. For deeper insights, discussions, and expert advice, consider joining my blog membership and be part of a community that prioritizes cybersecurity excellence.
Don’t Wait for a Breach
Be proactive and safeguard your organization’s future today. Cyber threats are evolving, and preparation is key. By taking steps now to enhance your cybersecurity measures, you’re investing in the resilience and security of your organization’s digital assets.
Reserve your spot now and take the first step towards a more secure future.