Balancing Traditional Infrastructure with Modern Defense Strategies
In today’s rapidly evolving cloud era, there’s a palpable buzz around cloud solutions and AI-driven security measures. However, amidst this forward momentum, it’s crucial not to overlook the foundational on-premises systems that have been, and for many organizations, continue to be, the bedrock of their IT infrastructure. Active Directory (AD) stands out prominently in this context.
Originally conceived by Microsoft as a directory service for Windows domain networks, AD remains an indispensable tool for a multitude of organizations across the globe. It plays a pivotal role in managing and authenticating users and devices within a network. Yet, as cyber threats become increasingly sophisticated, many enterprises inadvertently leave their AD systems vulnerable. Whether it’s due to a lack of regular patching, default configurations that haven’t been updated, or the absence of periodic assessments, these oversights make AD a prime target for cyber adversaries.
It’s a stark reminder that while the allure of the cloud is undeniable, the security of foundational systems like AD cannot be relegated to the background. In this series of articles, I aim to shed light on the significance of Active Directory in the current cybersecurity landscape, emphasizing why its protection should remain a top priority. Furthermore, I will explore how tools like Defender for Identity can enhance the security posture of AD, ensuring that organizations have a holistic defense strategy in place.
Active Directory as the Backbone of Enterprise IT
User Authentication and Authorization
Active Directory’s primary role in any enterprise is to serve as the gatekeeper, ensuring that only authorized individuals gain access to the network and its resources. This is achieved through two main processes: authentication and authorization.
Authentication is the process of verifying the identity of a user. When an individual attempts to log into a network, AD checks their provided credentials (typically a username and password) against its stored data. If the credentials match, the user is authenticated.
Post-authentication, the process of authorization begins. This is where AD determines what resources the authenticated user can access and what actions they can perform. For instance, while an HR executive might have access to employee records, they might not have the rights to access financial data. Active Directory uses group memberships, access control lists, and other mechanisms to make these determinations, ensuring that users only access what they’re supposed to.
Resource Management and Access Control
Beyond just user identities, Active Directory plays a crucial role in managing the myriad of resources within an enterprise network. These resources can range from files and printers to applications and databases. AD allows administrators to categorize, allocate, and control access to these resources with precision.
Access control in AD is not just about granting permissions but also about denying them when necessary. Through detailed access control lists (ACLs), administrators can specify who can read, write, modify, or delete specific resources. This granularity ensures that sensitive data remains protected, accessible only to those with the right permissions.
Moreover, AD’s hierarchical structure, with its organizational units and groups, makes resource management efficient. Instead of assigning permissions to individual users, administrators can assign them to groups. Any user added to a group automatically inherits the permissions associated with that group, streamlining the access control process.
Revolutionize Your Security Operations with Microsoft Sentinel
Cybersecurity Implications
Single Point of Compromise
Active Directory, with its centralized nature, is both a boon and a potential vulnerability for enterprises. While it streamlines management and access control, it also presents a lucrative target for cyber adversaries. If compromised, AD can provide attackers with the keys to the entire kingdom, so to speak. This is because a breach in AD can potentially grant unauthorized access to every resource, user credential, and piece of data within the network. The centralized nature of AD, which is its strength, can also be its Achilles’ heel, making it a single point of failure. It underscores the importance of robust security measures to protect AD from potential breaches.
Privilege Escalation
One of the primary objectives of cyber attackers, once they gain a foothold in a network, is to escalate their privileges. Privilege escalation refers to the act of exploiting a bug, design flaw, or configuration oversight in an operating system or application to gain elevated access to resources that are normally protected from an application or user. In the context of AD, attackers might exploit misconfigurations or use techniques like Pass-the-Hash or Pass-the-Ticket to elevate their privileges. Once they have higher-level permissions, they can access sensitive data, deploy malware, or even take control of the entire system. Ensuring that user roles and permissions in AD are tightly controlled and regularly audited is crucial to prevent such escalation.
Lateral Movement
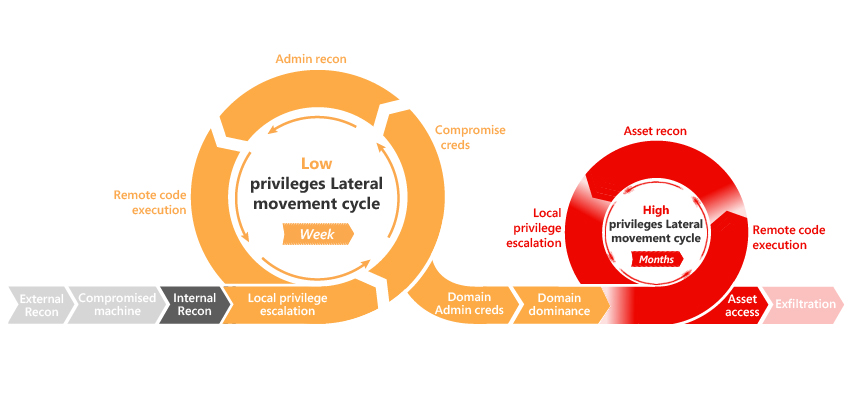
After gaining access to a network, attackers often don’t stop at the initial point of entry. They engage in what’s known as lateral movement, navigating through the network to locate valuable data or additional access points. Active Directory, with its comprehensive view of users, resources, and permissions, can inadvertently aid this movement if compromised.
One of the emerging concerns in the realm of lateral movement is the potential bridge between on-premises AD and cloud-based identity solutions like Entra ID (formerly Azure AD). If an attacker can compromise the on-premises AD, they might exploit configurations and trust relationships to pivot into cloud environments. This is especially concerning as many organizations are adopting hybrid models, where on-premises systems coexist and integrate with cloud services. A misconfiguration or vulnerability in the on-premises AD can potentially open doors to cloud resources, amplifying the impact of a breach.
Attackers can use AD to understand the network’s structure, identify potential targets, and move stealthily, often using legitimate credentials to avoid detection. Techniques like Kerberoasting or exploiting trust relationships between domains can facilitate this movement. Furthermore, with tools and techniques evolving, attackers can potentially exploit synchronization mechanisms or token-based authentications to move from on-premises AD to Entra ID.
Given this interconnected landscape, it’s paramount to ensure that on-premises configurations are robust and secure. Protecting AD, regularly reviewing configurations, and monitoring for unusual activity both on-premises and in the cloud are vital to detect and halt such movements early on.
Common Active Directory Threats
Pass-the-Ticket/Pass-the-Hash Attacks
Pass-the-Ticket and Pass-the-Hash are attack techniques that exploit the way Windows authentication works. These methods have been well-documented, with resources like PayloadsAllTheThings providing comprehensive insights into AD attacks.
In a Pass-the-Hash attack, adversaries capture a user’s hashed credentials from a compromised system. Instead of attempting to crack the hash to reveal the actual password, attackers use the hash itself to authenticate to other systems in the network. This allows them to impersonate legitimate users and gain unauthorized access.
Pass-the-Ticket attacks target Kerberos authentication. Once attackers have compromised a user’s credentials, they can request Kerberos tickets on their behalf. With these tickets, attackers can access various resources within the network as if they were legitimate users.
Both attacks bypass the need for an actual password, making traditional password-based defenses ineffective. They underscore the importance of securing and monitoring authentication mechanisms within AD.
Golden Ticket Attacks
Golden Ticket attacks are a form of Kerberos ticket forgery. In this attack, adversaries first compromise the Key Distribution Center (KDC) in Active Directory to gain access to the Ticket Granting Ticket (TGT) encryption key. With this key, they can create forged Kerberos tickets, known as “Golden Tickets“
These Golden Tickets grant attackers unrestricted access to any resource in the domain. Their longevity and stealthiness make them particularly dangerous. They can remain valid for extended periods, often up to 10 years, and can be renewed indefinitely, allowing attackers to maintain covert persistence in a network.
Reconnaissance
Before launching targeted attacks on an Active Directory infrastructure, adversaries often engage in reconnaissance. This phase involves gathering as much information as possible about the AD environment, its structure, users, permissions, and more.
Attackers use various tools and techniques to query AD for valuable information. For instance, they might enumerate user accounts to identify high-privilege users or discover group memberships to understand the organization’s structure.
One of the most powerful tools in this domain is mimikatz, which can extract plaintext passwords, hash, PIN code, and Kerberos tickets from memory. Another tool that has gained significant traction in both offensive and defensive security circles is BloodHound. BloodHound allows users to visualize Active Directory relationships and permissions, making it easier for blue teams to identify and rectify potential vulnerabilities, while also being a valuable asset for red teams and adversaries to map out attack paths.
The availability of such potent tools in the public domain underscores the importance of organizations being vigilant and proactive in their defense strategies. Reconnaissance, while seemingly benign as it doesn’t involve direct harm, is a precursor to more damaging attacks. Detecting and mitigating such activities early on is crucial to prevent subsequent breaches.
The Real-World Consequences of Neglecting Active Directory Security
Source – What Is the SolarWinds Hack and Why Is It a Big Deal? (businessinsider.com)
While we’ve discussed the technical aspects and importance of Active Directory, it’s crucial to understand the tangible, real-world implications of neglecting AD security. The global business impact of AD attacks is not just theoretical; it has the potential to halt factories, ground airplanes, disrupt stock markets, and even bankrupt corporations.
Case Studies – The Tangible Impact of AD Breaches
- SolarWinds (December 2020): A sophisticated cyberattack led to malware-infused updates being sent to end-users. This breach not only affected SolarWinds but also its vast clientele, showcasing the ripple effect of such attacks.
- US Pipeline (December 2019): A ransomware attack targeted a US pipeline, causing the facility to go offline for two days. This incident highlighted the potential of AD attacks to disrupt critical infrastructure.
- Travelex (December 2019): The foreign exchange company Travelex was hit by the Sodinokibi ransomware, leading to a significant disruption in its online services.
- Norsk Hydro (March 2018): One of the world’s largest aluminum producers had to switch to manual operations at several of its plants due to a ransomware attack, emphasizing the operational impact of such breaches.
- Maersk (June 2017): A NotPetya ransomware attack affected the Danish shipping giant, leading to an estimated loss of $300 million. This incident underscores the financial ramifications of AD breaches. I recommend watching different presentations around it on YouTube – (94) CyberSecurity Davos 2017 – Maersk – Business Impact – with EN subtitles – YouTube. There are many great insights and learnings from that incident.
- Sony’s PlayStation Network (April 2011): A massive breach led to an estimated loss of $171 million, highlighting the potential brand damage and loss of customer trust.
These incidents serve as stark reminders of the vulnerabilities that exist in even the most advanced IT infrastructures. They emphasize the importance of continuous real-time monitoring of AD to detect potential threats and breaches swiftly.
The Role of Active Directory in Cybersecurity Strategy
Auditing and Monitoring
Active Directory is the nerve center of many enterprise IT environments, making it a prime target for cyber adversaries. Given its significance, it’s imperative to keep a vigilant eye on all activities within AD. Auditing and monitoring involve tracking and analyzing changes, logins, permission modifications, and other activities within the directory.
To aid in this endeavor, there are specialized tools available that can provide in-depth assessments of AD’s security posture. One such renowned tool is PingCastle. PingCastle offers a comprehensive analysis of Active Directory’s health, highlighting potential vulnerabilities and providing actionable recommendations to bolster security. Its ability to perform regular health checks ensures that organizations can proactively address any security concerns, keeping their AD environment robust and resilient.
By leveraging tools like PingCastle and maintaining vigilant monitoring practices, organizations can detect unusual patterns or unauthorized actions that might indicate a security breach. Advanced monitoring solutions can also provide real-time alerts, ensuring that security teams are immediately informed of potential threats. Furthermore, regular audits can help in compliance with various industry regulations, ensuring that access controls and user activities align with best practices.
Regular Patching
Software vulnerabilities are a common entry point for cyberattacks. Active Directory, like any other software, can have vulnerabilities that, if exploited, can lead to unauthorized access or system compromise. Regular patching involves updating the AD software to fix known vulnerabilities. Microsoft regularly releases patches and updates to address security issues and enhance functionality.
In today’s cloud-centric world, organizations have the advantage of leveraging cloud-based solutions like Azure Update Management and Azure Update Center to streamline and automate the patching process. Both solutions provide a centralized view across hybrid environments, allowing IT teams to quickly assess the status of available updates and schedule installation times.
By integrating these Azure solutions, organizations can ensure a consistent and timely patching routine, reducing the manual overhead and minimizing the window of vulnerability. Furthermore, the flexibility offered by these tools means that businesses can customize their patching strategy to fit their unique operational needs and infrastructure.
By ensuring that Active Directory and other critical systems are always up-to-date, organizations can shield themselves from known threats, reduce their attack surface, and maintain a robust cybersecurity posture in an ever-evolving threat landscape.
Principle of Least Privilege (PoLP)
The Principle of Least Privilege is a foundational security concept that advocates for granting users and systems only the permissions they absolutely need to perform their tasks. In the context of Active Directory, this means ensuring that users, especially those with elevated privileges, have access only to the resources and actions necessary for their roles. Overly permissive settings can lead to inadvertent data exposure or provide avenues for attackers if they compromise a high-privilege account. Regularly reviewing and adjusting permissions in line with the PoLP can significantly reduce security risks.
Backup and Recovery
Despite the best security measures, there’s always a risk of data loss or system compromise, be it from cyberattacks, hardware failures, or human errors. Having a robust backup and recovery strategy for Active Directory is crucial.
One of the modern solutions that organizations are turning to is Azure Backup. Azure Backup offers a cloud-based, scalable solution to protect your data and applications. It provides simple, secure, and cost-effective capabilities to backup your Active Directory and ensure data integrity. With features like incremental backups, data encryption, and geographically dispersed data centers, Azure Backup ensures that your data is not only backed up but also remains secure and readily accessible when needed.
Regular backups ensure that, in the event of data loss or corruption, organizations can restore their directory to a previous state. Moreover, in the face of ransomware attacks, where attackers might encrypt critical data, having backups can be a lifeline, allowing organizations to restore their systems without paying ransoms. Whether you’re using traditional backup methods or cloud-based solutions like Azure Backup, the key is to have a well-tested recovery plan. This ensures that, post-incident, operations can resume with minimal downtime, preserving business continuity.
Compliance
In the realm of cybersecurity, compliance isn’t just about adhering to external regulations; it’s also about ensuring internal consistency and uniformity across systems. For organizations with multiple domain controllers, maintaining consistent settings and configurations becomes paramount. Discrepancies or deviations can introduce vulnerabilities or lead to operational inefficiencies.
Active Directory plays a pivotal role in this aspect. Given its centralized nature, AD can serve as the reference point for compliance checks, ensuring that all domain controllers adhere to the desired configurations and standards. Regular compliance checks can help identify any deviations or misconfigurations, allowing for timely remediation.
To aid in this endeavor, tools like Configuration Manager Baselines can be invaluable. They allow organizations to define desired configurations and then assess systems against these baselines, highlighting any discrepancies. Furthermore, Azure Automanage Machine Configuration Services offers a cloud-based solution to automate and standardize server configurations. With its overview, organizations can ensure that their servers, including domain controllers, are consistently configured in line with best practices. This not only enhances security but also simplifies the compliance reporting process, providing clear visibility into the state of the infrastructure.
Such compliance measures, while often seen as administrative overhead, are crucial in the larger cybersecurity strategy. They ensure that the organization’s defenses are uniformly robust, leaving no weak links that could be exploited by adversaries.
Integrating Active Directory with Modern Security Solutions
Active Directory (AD) has long been a cornerstone of enterprise IT, serving as a central repository for user identities and access controls. However, as cybersecurity threats have evolved, so too has the need for more advanced security solutions that can seamlessly integrate with AD.
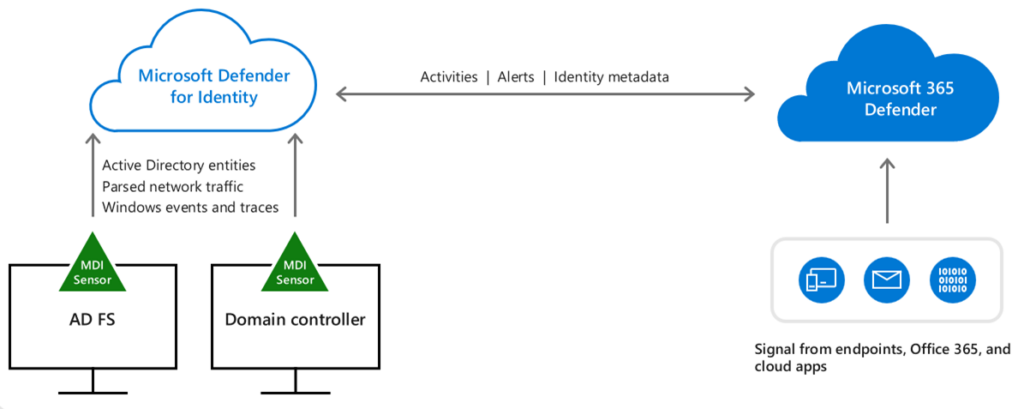
Enter Microsoft Defender for Identity (MDI). MDI is a cloud-based security solution tailored to detect and respond to identity-based threats in real-time. By harnessing the rich signals from Active Directory, MDI can pinpoint suspicious activities, from unusual login patterns to potential privilege escalations. This not only provides a more comprehensive view of potential security threats but also enhances the overall security posture by bridging the gap between traditional AD controls and modern threat detection capabilities.
In addition to MDI, Microsoft Sentinel stands out as a powerful security information and event management (SIEM) and Security orchestration, automation, and response (SOAR) solution that offers advanced threat hunting, analytics, and investigation capabilities. By installing the Azure Arc agent, organizations can extend Sentinel’s visibility into on-premises environments, including Active Directory. This integration allows security teams to visualize data using Azure Workbooks, connect Microsoft 365 Defender data sources, and engage in proactive threat hunting. The combined strength of MDI and Sentinel ensures that organizations have a holistic view of their security landscape, enabling them to detect, investigate, and respond to threats with greater agility.
While MDI itself doesn’t isolate machines, its integration capabilities, combined with Sentinel’s automation rules and other Defender products allow for a more dynamic response to detected threats. For instance, upon detecting a potential security alert can be sent to Sentinel enabling them to take swift action. Moreover, the cloud-based nature of both tools ensures that they’re always updated with the latest threat intelligence, offering proactive defense measures against emerging threats.
One of the standout features of both MDI and Sentinel is their ability to integrate seamlessly with other Microsoft security solutions. This interoperability facilitates data correlation and provides security teams with a unified dashboard for more efficient investigations. When an incident occurs, having interconnected tools can significantly expedite the investigation process, ensuring timely threat mitigation.
Basics Are Still Important
In the rapidly evolving landscape of cybersecurity, it’s easy to become enamored with cutting-edge technologies and complex defense strategies. However, amidst the buzz of cloud solutions and AI-driven security measures, it’s important not to overlook the significance of foundational practices. The basics, often considered the building blocks of a strong cybersecurity posture, still play a critical role in safeguarding an organization’s digital assets.
One valuable approach is AD tiering, which involves segmenting Active Directory environments based on the sensitivity of the resources they manage. By categorizing resources and controlling access within these tiers, organizations can limit the potential impact of a breach. This strategic division enhances security by containing threats and reducing the lateral movement that attackers can exploit.
Additionally, embracing the concept of a “home field advantage” as detailed in the book “Cybersecurity Attacks – Red Team Strategies: A practical guide to building a penetration testing program having homefield advantage” by Johann Rehberger, can significantly bolster an organization’s security stance. The book emphasizes the importance of understanding your own network environment better than potential adversaries do. By doing so, you can identify vulnerabilities, anticipate attack paths, and design countermeasures that proactively protect against threats. This practice not only strengthens your defenses but also aligns with the principle of proactive cybersecurity.
While advanced tools and technologies are essential, the combination of effective AD tiering and a robust understanding of your network’s unique dynamics can be powerful weapons in the fight against cyber threats. These approaches don’t necessarily require significant financial investments, but they do demand a commitment to proactive planning, continuous learning, and the application of best practices.
Conclusion
In the intricate tapestry of modern cybersecurity, Active Directory remains a pivotal thread, binding together the myriad of digital identities within an organization. Its integration with advanced tools like Microsoft Defender for Identity and Sentinel showcases the evolution of cybersecurity measures, adapting and growing in response to the ever-changing threat landscape. As cyber adversaries become more sophisticated, it’s imperative for businesses to not only understand the tools at their disposal but to leverage them effectively, ensuring a proactive and robust defense strategy.
Call to Action
Are you ready to fortify your organization’s digital defenses and stay a step ahead of cyber threats? Don’t miss the opportunity to join my upcoming exclusive webinar, where I dive into the world of Microsoft Defender for Identity (MDI) and explore its comprehensive implementation process. This webinar is designed to empower you with the knowledge and tools you need to enhance your organization’s cybersecurity posture.
Reserve Your Spot Today
Mark your calendar for Thursday, September 14, 2023, from 10:00 AM to 12:00 PM Pacific Time (US & Canada). The webinar will be hosted on Microsoft Teams, providing you with a convenient and interactive platform to learn from a cybersecurity expert.
Limited Spaces Available
Space is limited, so make sure to secure your spot early. To register for this free webinar and gain valuable insights into mastering the implementation of Microsoft Defender for Identity, please complete the registration form. Registration form – Mastering Microsoft Defender for Identity: A Comprehensive Guide to Implementation – Kaido Järvemets (kaidojarvemets.com)
Empower Your Cybersecurity Journey
In addition to the webinar, explore my Defender for Identity and Sentinel service offerings to learn how I can assist in implementing and optimizing these solutions for your business. For deeper insights, discussions, and expert advice, consider joining my blog membership and be part of a community that prioritizes cybersecurity excellence.
Don’t Wait for a Breach
Be proactive and safeguard your organization’s future today. Cyber threats are evolving, and preparation is key. By taking steps now to enhance your cybersecurity measures, you’re investing in the resilience and security of your organization’s digital assets.
Reserve your spot now and take the first step towards a more secure future.